Cybersecurity breaches in healthcare cost australian organisations an average of AUD 2.15 million per incident. For Brisbane healthcare businesses, protecting patient data is more than a legal requirement. It is a crucial safeguard for reputation and trust. By understanding step-by-step strategies to strengthen data protection—from risk assessments to ongoing audits—you gain practical tools to defend sensitive information and meet strict regulatory standards.
Table of Contents
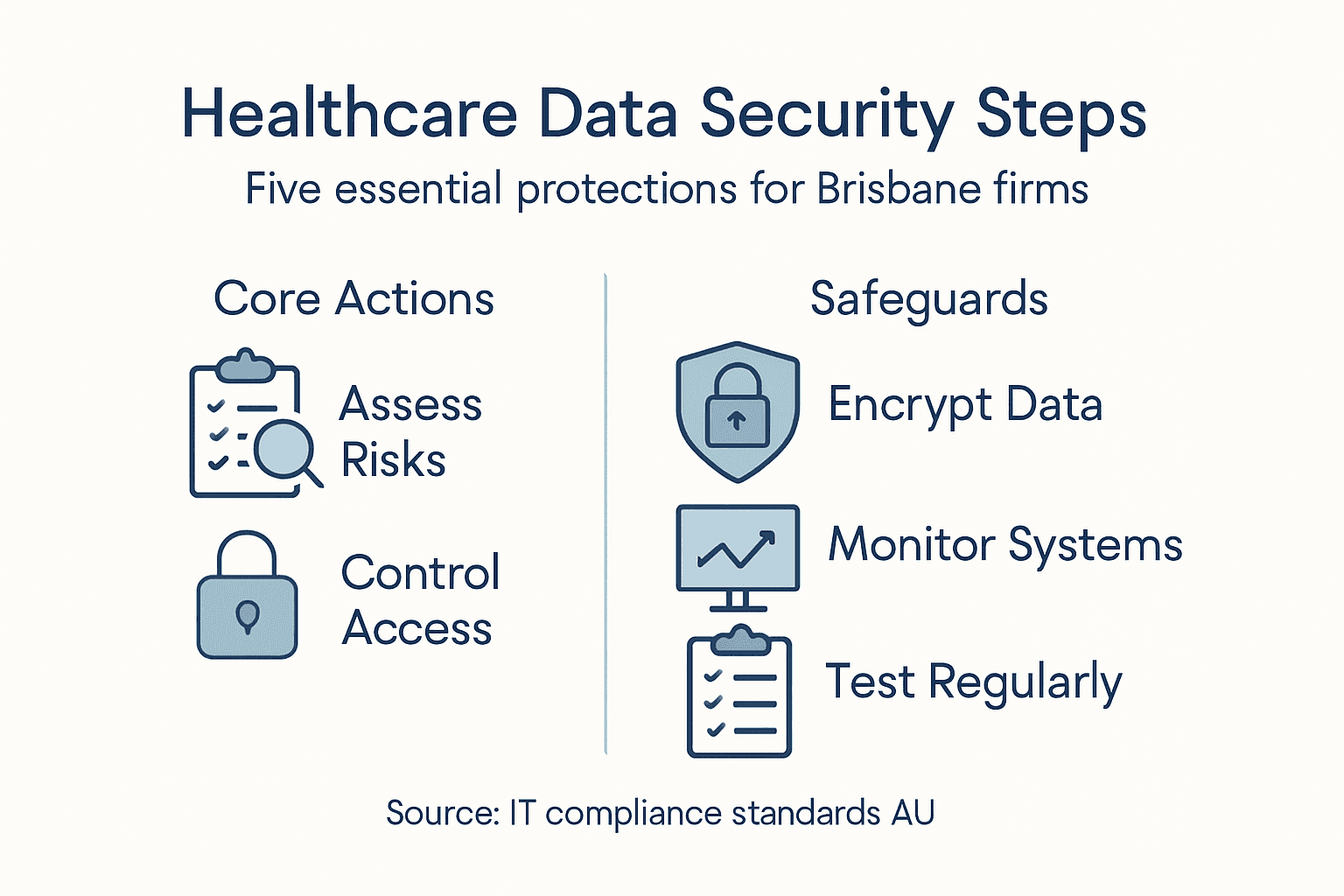
- Step 1: Assess Current Data Protection Risks
- Step 2: Implement Robust Access Controls
- Step 3: Deploy Encryption And Secure Backups
- Step 4: Monitor Systems For Breaches And Compliance
- Step 5: Verify Effectiveness Through Audits And Testing
Quick Summary
| Important Insight | Explanation |
|---|---|
| 1. Assess Data Protection Risks | Conduct a comprehensive risk assessment to identify vulnerabilities in data systems, ensuring patient information is secure from potential breaches. |
| 2. Implement Access Controls | Establish role-based access control and regularly review permissions to limit unauthorized access to sensitive patient information. |
| 3. Use Encryption and Backups | Apply end-to-end encryption for data and follow a robust backup strategy to safeguard patient records from cyber threats. |
| 4. Monitor Systems Continuously | Employ real-time monitoring tools to detect unusual activity and ensure compliance with healthcare standards, protecting patient data. |
| 5. Conduct Regular Audits and Testing | Regularly perform vulnerability assessments and penetration tests to validate the effectiveness of cybersecurity measures and identify weaknesses. |
Step 1: Assess current data protection risks
Identifying and understanding your healthcare firm’s data protection vulnerabilities is the critical first step in building a robust cybersecurity strategy. Brisbane healthcare businesses must systematically evaluate their current information security landscape to pinpoint potential weaknesses before they can be exploited.
Start by conducting a comprehensive risk assessment that maps out all data storage systems patient record databases, electronic health record platforms, and communication channels. The National Healthcare Interoperability Plan recommends examining each system’s security protocols and potential points of unauthorized access. This means reviewing network configurations device connections staff access permissions and data transfer mechanisms. Pay special attention to legacy systems which often contain unpatched vulnerabilities that cybercriminals can target.
Your assessment should include an inventory of all digital and physical assets tracking where sensitive patient information is stored processed and transmitted. Engage your IT team or a specialised cybersecurity consultant to perform vulnerability scans and penetration testing to simulate potential breach scenarios. Healthcare cybersecurity protocols emphasise identifying weak points in your current infrastructure that could compromise patient data privacy.
Practical Advice:Create a detailed spreadsheet documenting every system network and device that handles patient information to ensure comprehensive risk tracking.
Step 2: Implement robust access controls
Effective access control is your primary defence against unauthorized data breaches in healthcare environments. This critical step involves creating a systematic approach to managing who can view access and modify sensitive patient information across your Brisbane healthcare organisation.

Implement Role Based Access Control strategies that precisely define user permissions based on specific job functions. This means carefully mapping each staff member’s role and corresponding data access requirements. Medical receptionists would have different access levels compared to senior clinicians or administrative managers. Regularly review and update these role assignments to reflect staff changes personnel movements and evolving organisational structures.
Aligning with National Safety and Quality Health Service Standards requires developing a comprehensive access management framework. This involves implementing multi factor authentication strong password policies automatic session timeouts and detailed logging of all system access attempts. Conduct periodic access rights audits to identify and immediately remove unnecessary or outdated permissions ensuring your security remains dynamic and responsive.
Practical Advice:Create a detailed permissions matrix documenting exact access levels for each role and review this document quarterly to maintain precise access control.
Step 3: Deploy encryption and secure backups
Protecting sensitive patient data requires a strategic approach to encryption and backup systems that safeguards your healthcare organisation against potential data breaches and system failures. This step focuses on implementing robust data protection mechanisms that ensure the confidentiality and recoverability of critical patient information.
Cloud computing solutions offer advanced encryption technologies that provide comprehensive protection for healthcare data. Implement end to end encryption for all patient records electronic communications and storage systems. This means converting sensitive information into unreadable code that can only be accessed with specific decryption keys ensuring that even if unauthorized parties intercept the data they cannot comprehend its contents.
Establish a comprehensive backup strategy that follows secure data backup protocols including regular scheduled backups stored in multiple isolated locations. Create redundant backup systems that automatically save patient records clinical notes and administrative data at frequent intervals. These backups should be encrypted separately from the primary data storage and tested regularly to confirm data integrity and quick recoverability in case of system failures or cyberattacks.
Practical Advice:Implement a 321 backup rule create three separate backup copies using two different storage media with one copy stored offsite to maximise data protection and recovery options.
Step 4: Monitor systems for breaches and compliance
Continuous monitoring of your healthcare organisation’s digital infrastructure is crucial for detecting potential security vulnerabilities and maintaining regulatory compliance. This step involves implementing systematic approaches to track system performance identify potential breaches and ensure ongoing adherence to national healthcare standards.
Medical device incident monitoring requires comprehensive tracking and reporting mechanisms that capture any unusual system activities or potential security risks. Implement advanced monitoring tools that provide real time alerts for suspicious access attempts unusual data transfer patterns or potential unauthorized system interactions. These tools should generate detailed logs that can be reviewed regularly and cross referenced with your access control and encryption protocols.
Aligning with National Safety and Quality Health Service Standards means establishing a proactive compliance monitoring framework. This involves conducting regular internal audits scheduling periodic security assessments and maintaining comprehensive documentation of all system activities. Create a dedicated compliance team responsible for reviewing monitoring reports investigating potential incidents and ensuring your healthcare organisation remains ahead of emerging cybersecurity threats.
Practical Advice:Develop an automated reporting dashboard that consolidates security logs compliance metrics and potential risk indicators to provide a quick visual overview of your system’s health and security status.
Step 5: Verify effectiveness through audits and testing
Validating your data protection strategies requires systematic and rigorous testing to ensure your cybersecurity measures function precisely as designed. This step focuses on developing comprehensive audit processes that thoroughly examine your healthcare organisation’s security infrastructure and compliance mechanisms.
Healthcare practitioner audits provide a structured approach to verifying organisational compliance. Conduct regular comprehensive security assessments that simulate potential breach scenarios penetration testing and vulnerability scanning. These audits should examine every aspect of your data protection framework including access controls encryption protocols network security and staff adherence to established security procedures. Document all findings meticulously and develop immediate remediation strategies for any identified weaknesses.
Systematic review mechanisms help identify subtle vulnerabilities that might otherwise remain undetected. Comprehensive audit mechanisms trigger awareness and knowledge sharing among your team ensuring everyone understands their role in maintaining robust cybersecurity. Schedule quarterly external security assessments involving independent cybersecurity experts who can provide unbiased evaluations of your current protection strategies. Encourage open communication about potential risks and create a culture of continuous improvement and proactive security management.
Practical Advice:Create a standardised audit checklist that covers technical security measures staff training compliance and incident response protocols to ensure consistent and thorough evaluation of your data protection framework.
Here’s a comparison of key cybersecurity best practices at each step for Brisbane healthcare organisations:
| Step | Core Focus | Example Actions | Intended Outcome |
|---|---|---|---|
| Assess Risks | Identify vulnerabilities | Asset inventory, risk assessment | Expose weak points early |
| Access Controls | Limit unauthorised access | Role-based permissions, audits | Minimise internal/external threats |
| Encryption & Backups | Safeguard data | End-to-end encryption, 321 backup rule | Prevent data loss and breaches |
| Monitor & Comply | Ongoing system vigilance | Real-time alerts, compliance audits | Quickly detect and mitigate threats |
| Audit & Test | Validate security effectiveness | Penetration tests, external audits | Ensure measures work as intended |
Strengthen Your Brisbane Healthcare Firm’s Data Security with Expert IT Support
Protecting sensitive patient information is vital for Brisbane healthcare organisations facing increasing cybersecurity risks and complex compliance standards. As this article highlights, challenges like managing access controls, deploying encryption, monitoring for breaches, and verifying security measures demand specialised expertise and proactive solutions. At IT Start, we understand these critical pain points and are committed to helping local healthcare businesses safeguard their data through tailored managed IT support and advanced cybersecurity services.
Empower your organisation with robust role based access control systems, end-to-end encryption, secure backup strategies and continuous monitoring to prevent data breaches and ensure compliance. Our team brings local knowledge certified standards and a strategic, business-first approach to reduce risks and enhance operational efficiency. Don’t leave your patient data vulnerable. Discover how our healthcare IT solutions can secure your organisation today by contacting us for a free consultation. Take the first step towards confident data protection with IT Start. Learn more about how we help Brisbane healthcare firms with managed IT support and professional cybersecurity services.
Frequently Asked Questions
How can Brisbane healthcare firms assess their data protection risks?
Identifying data protection risks involves conducting a comprehensive risk assessment. Map out data storage systems, patient record databases, and communication channels to uncover vulnerabilities, and perform regular vulnerability scans to stay ahead of potential threats.
What access control measures should be implemented in healthcare organisations?
Implement Role Based Access Control strategies that define user permissions based on job functions. Regularly review access levels and maintain a permissions matrix to ensure only necessary personnel can modify sensitive patient information.
How can encryption safeguard sensitive healthcare data?
Use end-to-end encryption for all patient records and electronic communications to protect data confidentiality. Ensure that backups are also encrypted and test their integrity regularly to confirm that critical information can be recovered effectively.
What steps should be taken to monitor systems for breaches in a healthcare organisation?
Implement advanced monitoring tools that provide real-time alerts for unusual activities or potential security breaches. Regularly review system logs to ensure you can quickly address any detected vulnerabilities or compliance issues.
How often should audits be conducted to verify cybersecurity measures?
Conduct security audits and penetration testing at least quarterly to ensure your data protection measures are effective. Document findings thoroughly and develop immediate remediation plans for any identified weaknesses.
What practical strategies can be used to create a strong cybersecurity culture?
Encourage open communication about potential security risks among staff and provide regular training on security procedures. Foster a culture of continuous improvement, allowing team members to report concerns and participate in proactive security management.
Recommended
- Cyber Security Definition – Why It Matters for Brisbane Healthcare SMEs – IT Start
- Sensitive Data Protection – Key Compliance for Brisbane Firms – IT Start
- Cloud Security in Cloud Computing—Why It Matters – IT Start
- How to Secure Your Data for Brisbane Businesses Effectively – IT Start
- Creating appropriate confidential meeting spaces for therapy and counseling practices — Union Hall Workspace



