More than 35 percent of australian small and medium businesses have experienced a cyber incident in the past year. For IT managers in Brisbane financial services, protecting sensitive data and meeting strict compliance standards is a daily challenge. This guide delivers practical network security insights tailored for australian SMBs, highlighting real-world strategies and essential controls to reduce cyber risk and ensure regulatory confidence.
Table of Contents
- Defining Network Security For SMBs
- Key Types Of Network Security Controls
- Essential Regulatory Frameworks In Australia
- Core Requirements And Compliance Obligations
- Risks And Consequences Of Poor Security
- Common Mistakes And How To Avoid Them
Key Takeaways
| Point | Details |
|---|---|
| Ongoing Network Security | For Brisbane SMBs, network security is a continuous process that requires regular updates and monitoring to counter evolving cyber threats. |
| Holistic Defence Strategy | Implement a multi-layered approach combining preventative, detective, and corrective controls for maximum protection against cyber risks. |
| Compliance is Essential | Understanding and adhering to Australian regulatory frameworks is crucial for maintaining robust cybersecurity and avoiding legal penalties. |
| Education and Training | Continuous employee training and security awareness are vital to mitigate common mistakes and enhance the overall security posture of the organisation. |
Defining network security for SMBs
Network security represents a comprehensive set of technologies, processes, and practices designed to protect an organisation’s digital infrastructure and data from unauthorised access, cyber attacks, and potential breaches. For Brisbane small and medium businesses (SMBs), understanding network security is not just a technical requirement but a critical business survival strategy.
In the Australian context, SMBs face significant cyber risks that demand proactive protection. Recent cybersecurity research from the Australian Cyber Security Centre reveals that many small businesses remain vulnerable due to limited resources and inadequate security frameworks. Fundamentally, network security encompasses several key components that work together to safeguard digital assets:
- Firewall protection
- Intrusion detection systems
- Access control mechanisms
- Encryption protocols
- Regular security updates and patch management
Brisbane SMBs must recognise that network security is not a one time implementation but an ongoing process of monitoring, updating, and adapting to emerging digital threats. Strategic cybersecurity approaches recommended by the Australian Computer Society highlight the importance of developing dynamic, adaptable security strategies that can evolve with technological landscapes.
Pro Tip: Security Baseline Check: Conduct a comprehensive network security audit every six months to identify potential vulnerabilities and ensure your current protective measures remain effective against the latest cyber threats.
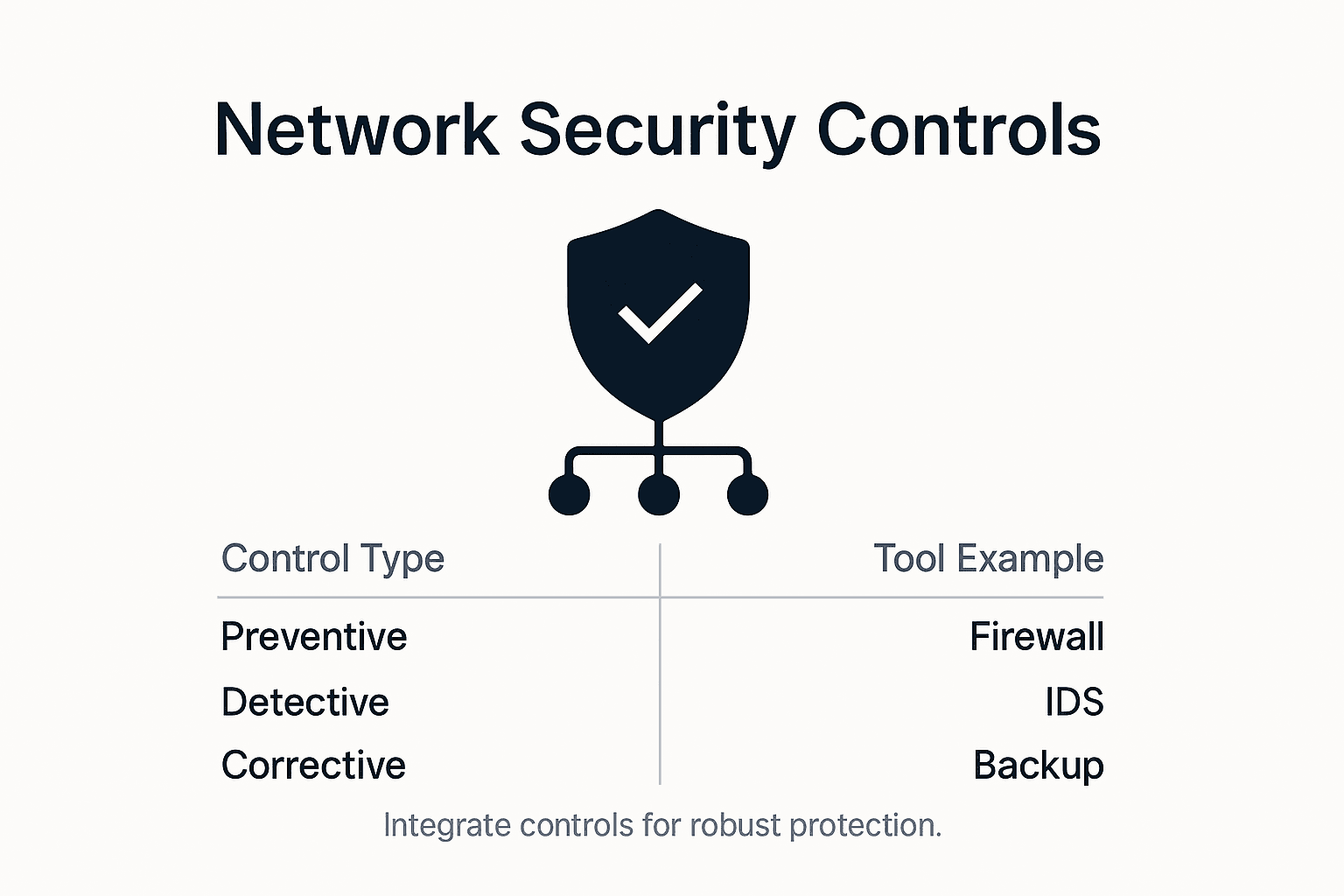
Key types of network security controls
Network security controls represent the strategic defences that protect an organisation’s digital infrastructure, forming a comprehensive shield against potential cyber threats. These controls are not standalone mechanisms but interconnected layers designed to prevent, detect, and respond to security incidents effectively.
The Australian Government’s Information Security Manual categorises network security controls into several critical types:
Preventative Controls:
- Firewalls and network segmentation
- Strong authentication mechanisms
- Access control policies
- Encryption technologies
- System hardening techniques
Detective Controls:
- Intrusion detection systems
- Security information and event management (SIEM) tools
- Log monitoring and analysis
- Vulnerability scanning
- Anomaly detection software
Corrective Controls:
- Incident response plans
- System recovery procedures
- Patch management processes
- Backup and restoration protocols
- Threat containment strategies
Guidance from AUSCERT emphasises that Brisbane SMBs must implement these controls holistically, recognising that each type of control plays a unique role in maintaining robust network security. The key is creating a multi-layered defence strategy that adapts to evolving cyber threats and organisational needs.
Here’s how common network security controls differ in purpose and business outcome:
| Security Control Type | Main Objective | Typical Tools/Processes | Business Impact |
|---|---|---|---|
| Preventative | Block threats before they enter | Firewalls, access policies | Reduces frequency of incidents |
| Detective | Identify breaches in progress | SIEM, log analysis, anomaly tools | Enables rapid threat detection |
| Corrective | Restore normal operations | Backups, incident response plans | Minimises recovery time and loss |
Pro Tip: Control Integration Strategy: Develop a comprehensive security framework that integrates preventative, detective, and corrective controls, ensuring each layer of your network defence communicates and reinforces the others for maximum protection.
Essential regulatory frameworks in Australia
Australian regulatory frameworks for network security represent a comprehensive approach to protecting digital infrastructure across businesses of all sizes. These frameworks provide structured guidance for organisations to maintain robust cybersecurity practices, ensuring that digital assets remain protected from evolving cyber threats.
The 2023-2030 Australian Cyber Security Strategy outlines six critical strategic cyber shields that form the foundation of national cybersecurity compliance. These shields encompass key regulatory requirements for Brisbane businesses:
Primary Regulatory Frameworks:
- Australian Privacy Principles (APPs)
- Privacy Act 1988
- Security of Critical Infrastructure Act
- Telecommunications and Other Legislation Amendment
- Australian Signals Directorate (ASD) Guidelines
- Notifiable Data Breaches (NDB) scheme
For Brisbane small and medium businesses, understanding these frameworks is not just about legal compliance but about developing a proactive approach to cybersecurity. Compliance with IT security regulations involves implementing systematic protection measures, conducting regular risk assessments, and maintaining comprehensive documentation of security protocols.
Each regulatory framework provides specific guidelines for data protection, breach notification, and cybersecurity management. Businesses must stay informed about these evolving requirements, as non-compliance can result in significant financial penalties and reputational damage.
The following table summarises major Australian regulatory frameworks and what businesses must do to comply:
| Framework | Main Focus | Key Business Obligation |
|---|---|---|
| Privacy Act 1988 | Data privacy | Protect personal information |
| ASD Guidelines | Cybersecurity controls | Apply approved protective measures |
| Notifiable Data Breaches (NDB) | Breach notification | Inform clients and OAIC about breaches |
| CPS 234 | Information security | Maintain robust risk management |
Pro Tip: Regulatory Mapping Strategy: Conduct an annual comprehensive review of your current cybersecurity practices against the latest Australian regulatory frameworks, identifying and addressing any potential compliance gaps before they become critical issues.
Core requirements and compliance obligations
Compliance obligations in network security represent a complex landscape of legal and technical requirements that Brisbane businesses must navigate carefully. These obligations extend beyond simple checklist items and demand a comprehensive, proactive approach to protecting digital assets and maintaining organisational integrity.
Prudential Standard CPS 234 provides a critical framework for understanding core compliance requirements, particularly for regulated entities in financial services. The standard emphasises several key compliance dimensions:
Core Compliance Requirements:
- Comprehensive risk management processes
- Clearly defined security roles and responsibilities
- Regular independent testing of security controls
- Robust incident response mechanisms
- Systematic documentation of security practices
- Continuous monitoring of technological vulnerabilities
IT compliance guidelines for Brisbane businesses highlight that meeting these obligations requires more than technical implementation. Businesses must develop a culture of security awareness, ensuring that every team member understands their role in maintaining network protection.
Regulatory compliance is an ongoing process that demands constant vigilance. Small to medium enterprises must invest in regular training, conduct periodic security assessments, and maintain flexible frameworks that can adapt to emerging technological and regulatory landscapes. Failure to meet these obligations can result in significant financial penalties, reputational damage, and potential legal consequences.
Pro Tip: Compliance Mapping Strategy: Create a dynamic compliance roadmap that reviews and updates your security protocols quarterly, ensuring alignment with the latest regulatory requirements and technological best practices.
Risks and consequences of poor security
Network security vulnerabilities represent a critical threat to Brisbane businesses, with potentially devastating financial and operational consequences. Small and medium enterprises are particularly susceptible to cyber attacks that can rapidly destabilise their entire operational infrastructure.

Export Finance Australia’s research reveals the stark reality of cybersecurity risks for Australian businesses. The potential consequences of inadequate network security are multifaceted and profound:
Key Risks of Poor Network Security:
- Substantial financial losses
- Operational disruption and downtime
- Customer data compromise
- Reputational damage
- Increased insurance premiums
- Potential legal liability
- Loss of business trust
Cyber security vulnerabilities for Brisbane businesses demonstrate that the impact extends far beyond immediate financial damage. A single security breach can erode years of carefully built business reputation, undermining customer confidence and potentially leading to long-term market position deterioration.
Statistically, small businesses face exponentially higher risks, with many struggling to recover from significant cyber incidents. The financial implications can range from direct monetary losses to indirect costs such as forensic investigations, system repairs, and potential regulatory fines. Comprehensive network security is not an optional extra but a fundamental business survival strategy in today’s digital landscape.
Pro Tip: Risk Assessment Strategy: Conduct a comprehensive cybersecurity vulnerability assessment every six months, identifying potential weaknesses and implementing targeted improvements before they can be exploited by malicious actors.
Common mistakes and how to avoid them
Network security is a complex landscape where seemingly minor oversights can lead to catastrophic vulnerabilities. Brisbane businesses frequently encounter predictable pitfalls that can compromise their entire digital infrastructure if left unaddressed.
AUSCERT’s professional guidance highlights several recurring security errors that small to medium enterprises consistently make:
Critical Network Security Mistakes:
- Neglecting regular software updates
- Failing to implement multi-factor authentication
- Using weak or recycled passwords
- Overlooking third-party vendor security risks
- Insufficient employee cybersecurity training
- Lack of comprehensive backup strategies
- Ignoring network segmentation
Each mistake represents a potential entry point for cybercriminals. Weak password protocols, for instance, can be systematically exploited through automated attacks that rapidly test multiple credential combinations. Third-party risks are particularly dangerous, as external vendors often represent the most vulnerable access points in an organisation’s network.
Cyber security risks for Brisbane businesses demonstrate that comprehensive prevention requires a holistic approach. Businesses must develop a proactive security culture that goes beyond technological solutions, embedding awareness and vigilance into every level of organisational operation. This means continuous education, regular security assessments, and a commitment to adapting security practices as threats evolve.
Pro Tip: Mistake Prevention Protocol: Implement a quarterly comprehensive security review that systematically audits your network’s vulnerabilities, tests existing protocols, and updates your defence mechanisms based on emerging threat intelligence.
Strengthen Your Brisbane Business with Expert Network Security Support
The challenges highlighted in this article show how Brisbane SMBs face complex cybersecurity risks such as poor network controls, regulatory compliance gaps, and vulnerability to costly breaches. IT Start understands these critical pain points and is committed to providing tailored managed IT support, advanced cybersecurity services, and proactive risk mitigation strategies designed specifically for small to medium enterprises in Queensland.
By partnering with IT Start, you gain access to expert guidance on integrating preventative, detective, and corrective security controls, ensuring compliance with Australian frameworks like the Privacy Act and CPS 234. Our local Brisbane team brings trusted expertise to help you reduce financial losses, prevent operational disruptions, and protect your reputation from cyber threats.
Are you ready to fortify your business against evolving cyber risks? Take the first step to secure your network and compliance framework today. Book a complimentary security assessment or consultation with IT Start now by visiting our Contact Us page. Let us customise a strategic cybersecurity solution that safeguards your operations and supports your business growth.
Frequently Asked Questions
What is network security, and why is it important for SMBs?
Network security is a collection of technologies, processes, and practices that protect an organisation’s digital infrastructure and data from unauthorised access and cyber attacks. For small to medium businesses, it is crucial for safeguarding sensitive information and ensuring business continuity.
What are the key components of effective network security for businesses?
Key components include firewall protection, intrusion detection systems, access control mechanisms, encryption protocols, and regular security updates and patch management. These elements work together to create a robust security posture.
How often should businesses conduct network security audits?
Businesses should conduct comprehensive network security audits every six months to identify potential vulnerabilities and ensure that their security measures are effective against emerging cyber threats.
What are some common mistakes businesses make in network security?
Common mistakes include neglecting regular software updates, failing to use multi-factor authentication, using weak passwords, and insufficient employee training on cybersecurity practices. Addressing these issues is vital to maintaining a secure network.



