Cybersecurity sounds like something only big corporations need to worry about, right? Yet small and medium businesses in Brisbane are out front as targets, with the average cyber attack costing between $39,000 and $97,000. Most people think hackers only go after the giants but the real risk is hiding in plain sight for everyday businesses that rely on their digital systems to survive.
Table of Contents
- Defining Cybersecurity: The Basics Of Digital Protection
- The Importance Of Cybersecurity For Small And Medium Businesses
- Understanding Common Cyber Threats And Vulnerabilities
- How Cybersecurity Measures Work To Safeguard Information
- Key Concepts And Practices In Effective Cybersecurity
Quick Summary
| Takeaway | Explanation |
|---|---|
| Cybersecurity safeguards critical information assets | Protects digital systems and data from malicious attacks and unauthorized access. |
| Focus on confidentiality, integrity, and availability | These principles ensure data security and accessibility for authorized users only. |
| Small businesses face significant cyber risks | Cyber attacks can lead to financial losses, data loss, and reputational damage, crucial for SMEs. |
| Invest in employee training and awareness | Ongoing staff education is essential to prevent cyber threats and enhance overall security measures. |
| Adopt a proactive cybersecurity strategy | Develop adaptive systems that can quickly respond to potential digital threats, transforming vulnerabilities into strengths. |
Defining Cybersecurity: The Basics of Digital Protection
Cybersecurity represents a comprehensive approach to protecting digital systems, networks, and data from malicious attacks and unauthorized access. At its core, cybersecurity is about creating robust digital defences that safeguard critical information assets across technological environments.
Understanding Digital Vulnerabilities
Modern businesses operate in an increasingly complex digital landscape where information is both a valuable asset and a potential target. Cybersecurity functions as a critical shield against various digital threats that can compromise organizational data, disrupt operations, and potentially cause significant financial damage.
The fundamental goal of cybersecurity is to maintain three core principles of information protection:
The following table clearly defines the three core principles of cybersecurity discussed within the article for quick reference.
| Principle | Definition |
|---|---|
| Confidentiality | Only authorised individuals can access specific data |
| Integrity | Data remains unchanged by unauthorised modifications |
| Availability | Systems and data are accessible to legitimate users |
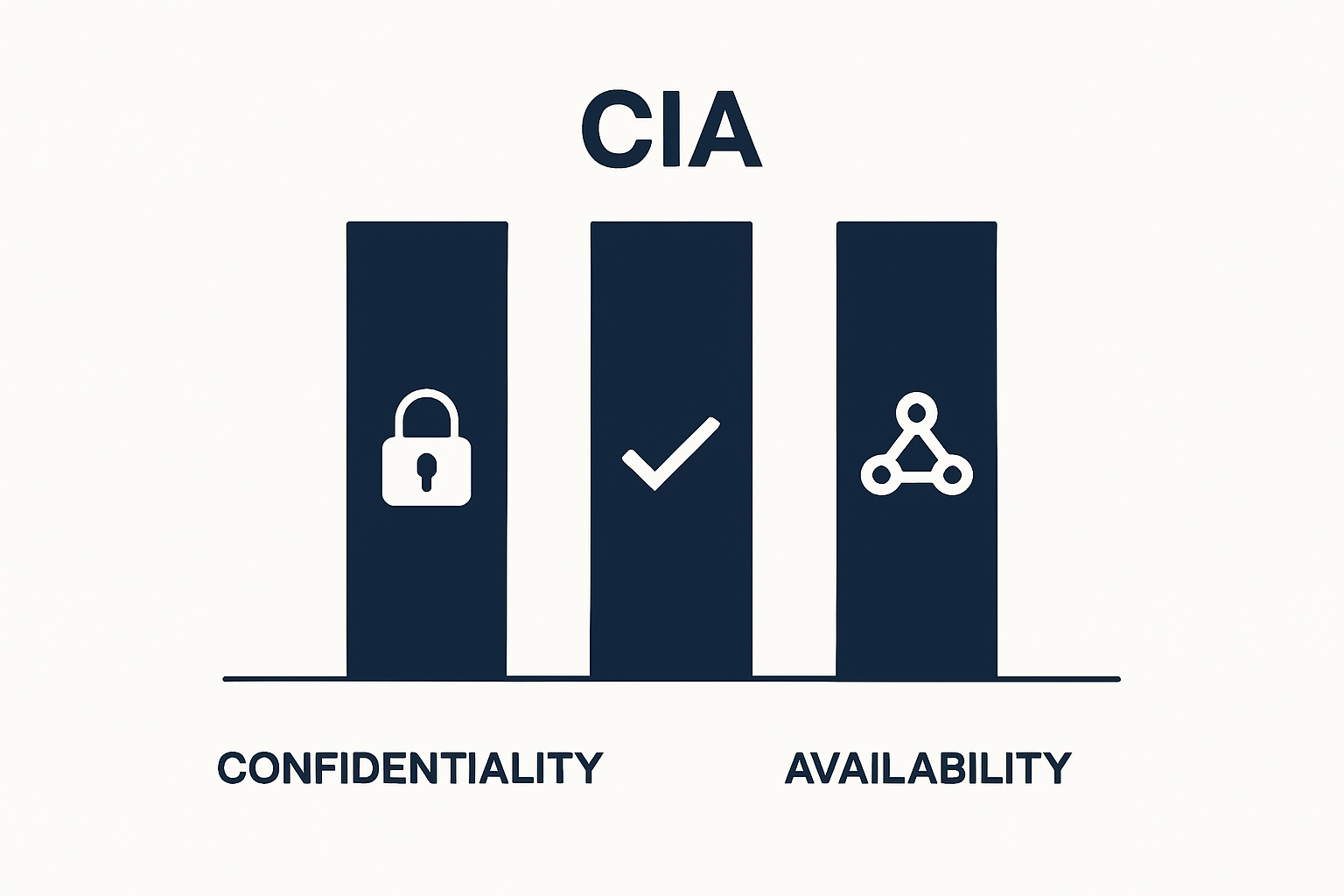
- Confidentiality: Ensuring only authorized individuals can access specific data
- Integrity: Protecting information from unauthorized modifications
- Availability: Guaranteeing that systems and data remain accessible to legitimate users
How Cybersecurity Protects Digital Assets
Cybersecurity strategies involve multiple layers of technological and human interventions. These include advanced technical controls like encryption, multi factor authentication, firewall configurations, and sophisticated monitoring systems. Cybersecurity experts at SANS Institute highlight that effective protection requires a holistic approach combining technological solutions with ongoing staff training and awareness programs.
For Brisbane businesses, understanding cybersecurity is not just about implementing technical solutions but creating a comprehensive risk management strategy that adapts to evolving digital threats. By recognizing potential vulnerabilities and proactively addressing them, organizations can significantly reduce their exposure to cyber risks and protect their most valuable digital assets.
The Importance of Cybersecurity for Small and Medium Businesses
Small and medium businesses in Brisbane represent a critical segment of the local economy, yet they are often the most vulnerable to sophisticated cyber threats. Understanding the strategic importance of cybersecurity is not just a technical consideration but a fundamental business survival strategy.
Financial and Operational Risks of Cyber Vulnerabilities
Cyber attacks can create devastating consequences for small businesses. Research from the Australian Cyber Security Centre indicates that the average financial impact of a cybersecurity incident can range from $39,000 to $97,000, a potentially catastrophic expense for many SMEs.
The potential damages extend beyond immediate financial loss and include:
This table summarises the potential consequences Brisbane small and medium businesses may face due to cyber vulnerabilities, as highlighted in the content.
| Consequence | Explanation |
|---|---|
| Financial Loss | Direct costs ranging from $39,000 to $97,000 due to breaches |
| Business Disruption | Interruptions to daily operations and loss of productivity |
| Data Loss | Permanent loss of sensitive customer or business information |
| Reputational Damage | Diminished trust from customers and partners |
| Legal and Compliance Penalties | Fines or actions due to breaches of data regulations |
| Long-term Customer Trust Issues | Ongoing impact on client relationships and business reputation |
- Disruption of business operations
- Permanent loss of critical customer and business data
- Significant reputational damage
- Potential legal and compliance penalties
- Long term loss of customer trust
Strategic Cybersecurity as a Competitive Advantage
Cybersecurity is no longer just a defensive measure but a strategic business differentiator. Companies that demonstrate robust digital protection can build stronger client confidence and distinguish themselves in competitive markets. This approach transforms cybersecurity from a cost centre into a value-generating business capability.
For Brisbane businesses, investing in comprehensive cybersecurity means creating a proactive shield that protects digital assets, maintains operational continuity, and demonstrates professional risk management. By treating cybersecurity as an integral part of business strategy, organisations can turn potential vulnerabilities into opportunities for building trust and demonstrating technological competence.

Understanding Common Cyber Threats and Vulnerabilities
Cybersecurity threats are constantly evolving, presenting complex challenges for businesses of all sizes. Understanding these digital risks is crucial for developing effective defensive strategies that protect organizational assets and maintain operational integrity.
Types of Cybersecurity Threats
Cyber threats represent sophisticated methods designed to exploit technological vulnerabilities and compromise digital systems.
These malicious strategies can target various entry points within an organization’s technological infrastructure.
Below is a table outlining the most common types of cyber threats mentioned in the article and their key characteristics for easy comparison.
| Threat Type | Description |
|---|---|
| Phishing Attacks | Deceptive communications that trick recipients into giving up data |
| Ransomware | Malicious software that locks data, demanding payment for its return |
| Malware | Harmful programs designed to damage or gain unauthorised access |
| Social Engineering | Psychological tactics to manipulate staff to breach protocols |
The most prevalent cyber threats include:
- Phishing Attacks: Deceptive communications designed to trick individuals into revealing sensitive information
- Ransomware: Malicious software that encrypts critical data and demands payment for restoration
- Malware: Harmful programs intended to damage or gain unauthorized access to computer systems
- Social Engineering: Psychological manipulation techniques used to deceive employees into compromising security protocols
Identifying Technological Vulnerabilities
Research from the Australian Cyber Security Centre reveals that small businesses are increasingly targeted due to perceived weaker security infrastructures. Technological vulnerabilities often emerge from outdated software, insufficient security configurations, and inadequate staff training.
Business owners must recognize that cybersecurity is not just about technological solutions but also about creating a comprehensive risk management approach. This involves understanding potential weak points in digital systems, implementing robust protective measures, and maintaining ongoing vigilance against emerging threats. By adopting a proactive stance, Brisbane businesses can significantly reduce their exposure to potential cyber incidents and protect their most valuable digital assets.
How Cybersecurity Measures Work to Safeguard Information
Cybersecurity measures function as sophisticated digital protection systems designed to create multiple layers of defence against potential technological breaches. These comprehensive strategies work systematically to identify, prevent, and mitigate potential security risks across digital environments.
Multilayered Defence Strategies
Effective cybersecurity operates through interconnected protective mechanisms that work simultaneously to secure digital assets. These layers create a robust shield that prevents unauthorized access and monitors potential vulnerabilities in real time.
Key components of multilayered defence include:
- Firewall Protection: Monitoring and controlling network traffic
- Encryption Technologies: Transforming sensitive data into unreadable formats
- Authentication Protocols: Verifying user identities before granting system access
- Intrusion Detection Systems: Identifying and responding to potential security threats
Technical and Human Protection Mechanisms
Research from the Australian Signals Directorate demonstrates that effective cybersecurity requires a holistic approach combining technological solutions with human awareness. Technical measures like advanced software and hardware configurations work in tandem with employee training programs to create comprehensive protection strategies.
For Brisbane businesses, understanding cybersecurity is about recognizing that protection is not a static concept but a dynamic process. By implementing adaptive security measures that evolve with emerging technological landscapes, organizations can develop resilient digital defence systems that protect their most critical information assets and maintain operational continuity.
Key Concepts and Practices in Effective Cybersecurity
Cybersecurity represents a complex ecosystem of strategic principles and practical interventions designed to protect digital infrastructure. Successfully navigating this landscape requires a comprehensive understanding of foundational concepts and adaptive methodologies that respond to evolving technological challenges.
Core Cybersecurity Principles
Effective cybersecurity is built upon a framework of fundamental principles that guide organizational protection strategies. These principles provide a structured approach to understanding and managing digital risks across technological environments.
Key foundational concepts include:
- Risk Assessment: Systematically identifying and evaluating potential vulnerabilities
- Continuous Monitoring: Implementing real-time tracking of digital systems
- Incident Response Planning: Developing strategic protocols for addressing security breaches
- User Education: Training personnel to recognize and mitigate potential security threats
Strategic Cybersecurity Implementation
Research from the Australian Cyber Security Centre highlights six critical cybersecurity functions that guide comprehensive protection strategies. These functions create a holistic approach to digital defence, moving beyond traditional reactive measures.
For Brisbane businesses, effective cybersecurity is not about achieving absolute protection but developing resilient, adaptive systems that can quickly identify, respond to, and recover from potential digital threats. By embracing a proactive and dynamic approach to cybersecurity, organizations can transform potential vulnerabilities into opportunities for technological strength and strategic innovation.
Secure Your Brisbane Business with IT Start’s Cybersecurity Expertise
If reading about digital vulnerabilities and the rising risk of attacks has you concerned about your company’s safety, you are not alone. Many Brisbane business owners face the same challenge. Cyber incidents can disrupt operations, drain finances, and damage your reputation—especially for small and medium enterprises where every asset counts. As highlighted in the article, multilayered defence, risk management, and proactive security are all essential. But even with the right knowledge, taking action is critical to actually protect your data and systems.
IT Start is your local partner for managed IT support, cloud solutions, and comprehensive cybersecurity services. Our team uses the same core principles of confidentiality, integrity, and availability discussed in the article. We combine decades of expertise with transparent, business-first support delivered right here in Brisbane. Do not wait for a cyber incident to threaten your business. Take the first step towards robust cybersecurity by talking to us today. Book your free assessment at IT Start and get local experts on your side now. Secure your data. Protect your reputation. Act now before the next threat arrives.
Frequently Asked Questions
What is cybersecurity?
Cybersecurity refers to the comprehensive measures taken to protect digital systems, networks, and data from malicious attacks and unauthorized access, ensuring the confidentiality, integrity, and availability of information.
Why is cybersecurity important for small and medium businesses?
Cybersecurity is crucial for small and medium businesses as they are often the most vulnerable to cyber threats. A single cyber attack can lead to significant financial loss, disruption of operations, and damage to reputation, making robust cybersecurity a fundamental aspect of business survival.
What are common types of cyber threats?
Common types of cyber threats include phishing attacks, ransomware, malware, and social engineering tactics. Each of these threats exploits different vulnerabilities within an organization’s digital infrastructure.
How can businesses enhance their cybersecurity measures?
Businesses can enhance their cybersecurity by implementing multilayered defence strategies, conducting regular risk assessments, providing ongoing employee training, and employing advanced technologies like encryption and intrusion detection systems.



