More than 40 percent of Brisbane businesses face at least one major IT compliance risk each year. With evolving regulations and relentless cyber threats, staying compliant goes far beyond ticking boxes. Clear knowledge of IT compliance helps you strengthen digital security, limit legal risks, and prove your commitment to clients. This guide breaks down the key concepts, requirements, and real-world practices Brisbane companies need to turn compliance from a headache into a strategic advantage.
Table of Contents
- Defining IT Compliance And Core Concepts
- Types Of IT Compliance For Australian Businesses
- How IT Compliance Works In Practice
- Legal And Regulatory Requirements In Australia
- Common IT Compliance Risks And Mistakes
Key Takeaways
| Point | Details |
|---|---|
| Understanding IT Compliance | IT compliance is a structured framework essential for protecting digital infrastructures and meeting regulatory standards, integrating security across all organizational levels. |
| Core Security Goals | Businesses must focus on four critical security areas: secure software environment, software development, traceability, and vulnerability management to mitigate cyber risks. |
| Types of Compliance | Australian businesses face industry-specific compliance requirements, such as financial services and privacy regulations, necessitating a tailored approach for each sector. |
| Common Risks | Proactive measures are required to address common compliance risks, including inadequate documentation and insufficient cybersecurity protocols, to prevent regulatory breaches. |
Defining IT Compliance And Core Concepts
IT compliance represents a structured framework that ensures businesses protect their digital infrastructure, meet regulatory requirements, and maintain robust cybersecurity standards. According to the Software Security Mapping Framework, compliance involves operationalizing security requirements across multiple organizational levels, from high-level regulatory standards to granular technical activities.
At its core, IT compliance encompasses four critical security goals that Brisbane businesses must understand:
- Secure Software Environment: Establishing controlled technological ecosystems
- Secure Software Development: Implementing rigorous development protocols
- Software Traceability: Maintaining comprehensive documentation and tracking
- Vulnerability Management: Proactively identifying and mitigating potential security risks
For small to medium enterprises in Brisbane, understanding these core concepts isn’t just about ticking regulatory boxes. It’s about creating a strategic approach to technology governance that protects your business from potential cyber threats and legal complications. As the ACSC Essential 8 guide for Brisbane SMEs highlights, compliance is an ongoing process of assessment, implementation, and continuous improvement.

Navigating the complex landscape of IT compliance requires a proactive mindset. By integrating robust security frameworks and maintaining clear documentation, Brisbane businesses can transform compliance from a potential burden into a strategic advantage that builds trust with clients and stakeholders.
Types Of IT Compliance For Australian Businesses
Australian businesses face a complex landscape of IT compliance requirements that vary significantly across different industries and regulatory frameworks. Appinventiv’s comprehensive guide reveals that compliance is not a one-size-fits-all approach, but a nuanced strategy tailored to specific sector needs and legal obligations.
The primary types of IT compliance for Australian businesses include:
- Financial Services Compliance: Governed by ASIC and AUSTRAC regulations
- Healthcare Compliance: Adhering to privacy and data protection standards
- Privacy Act Compliance: Protecting personal and sensitive information
- Cybersecurity Standards: Meeting national security and data protection requirements
- Industry-Specific Regulatory Frameworks: Unique compliance demands for sectors like telecommunications and finance
For Brisbane-based small to medium enterprises, understanding these compliance types is crucial. As Understanding IT Security Compliance highlights, each compliance type demands specific technical and procedural implementations. The key is not just meeting minimum requirements, but developing a comprehensive approach that protects your business and builds stakeholder trust.
Navigating these compliance landscapes requires a strategic approach. Brisbane businesses must remain proactive, continuously updating their IT practices to align with evolving regulatory requirements. By investing in robust compliance frameworks, organisations can transform potential regulatory challenges into opportunities for demonstrating professional excellence and commitment to best practices.
How IT Compliance Works In Practice
IT compliance transforms theoretical security standards into actionable business strategies through a systematic, multi-layered approach. Brisbane businesses must implement comprehensive processes that go beyond simple checklist mentality, creating robust frameworks that actively protect digital assets and maintain regulatory integrity.
In practical terms, IT compliance involves several critical implementation stages:
- Risk Assessment: Conducting thorough evaluations of existing technological infrastructure
- Gap Analysis: Identifying potential vulnerabilities and regulatory non-conformities
- Policy Development: Creating detailed, industry-specific compliance guidelines
- Technical Controls: Implementing specific security mechanisms and access restrictions
- Continuous Monitoring: Establishing ongoing surveillance and reporting systems
- Regular Auditing: Performing periodic comprehensive compliance reviews
Small to medium enterprises in Brisbane can streamline their compliance journey by understanding access control mechanisms, which serve as a fundamental component of comprehensive IT security strategies. These mechanisms help organisations systematically manage user permissions, track system interactions, and create transparent accountability trails that satisfy complex regulatory requirements.
Successful IT compliance is not a destination but a continuous evolution. Brisbane businesses must remain agile, adapting their technological frameworks to emerging threats, changing regulatory landscapes, and evolving best practices. By treating compliance as a dynamic, strategic process rather than a static requirement, organisations can transform potential regulatory challenges into opportunities for demonstrating technological maturity and professional excellence.
Legal And Regulatory Requirements In Australia
Australian businesses navigate a complex legal landscape that demands rigorous compliance across multiple regulatory domains. Law Compliance Australia highlights critical legal requirements that encompass various critical risk areas, including cybersecurity, privacy protection, and financial accountability.
The key legal and regulatory requirements for Australian businesses include:
- Criminal Code Compliance: Preventing bribery and false accounting practices
- Privacy Act 1988 Obligations: Protecting personal and sensitive information
- Cybersecurity Regulations: Implementing robust digital protection mechanisms
- Critical Infrastructure Protection: Securing essential business systems and data
- Financial Record-Keeping: Maintaining accurate and transparent financial documentation
Cyber Security Support resources emphasise that legal compliance is not just about avoiding penalties, but creating a comprehensive framework that protects both business interests and stakeholder trust. As Business Savers highlights, ongoing compliance monitoring is crucial for maintaining regulatory integrity and demonstrating professional accountability.
For Brisbane businesses, understanding these requirements means developing a proactive approach to legal compliance. This involves continuous education, regular internal audits, and creating a culture of transparency and ethical practice. By treating legal requirements as strategic opportunities rather than bureaucratic obstacles, organisations can transform compliance from a challenge into a competitive advantage that builds credibility and trust in the marketplace.
Common IT Compliance Risks And Mistakes
Law Compliance Australia reveals that Brisbane businesses frequently encounter significant compliance risks that can lead to substantial legal and financial consequences. Understanding these risks is crucial for developing proactive mitigation strategies that protect organisational integrity and prevent potentially devastating regulatory breaches.
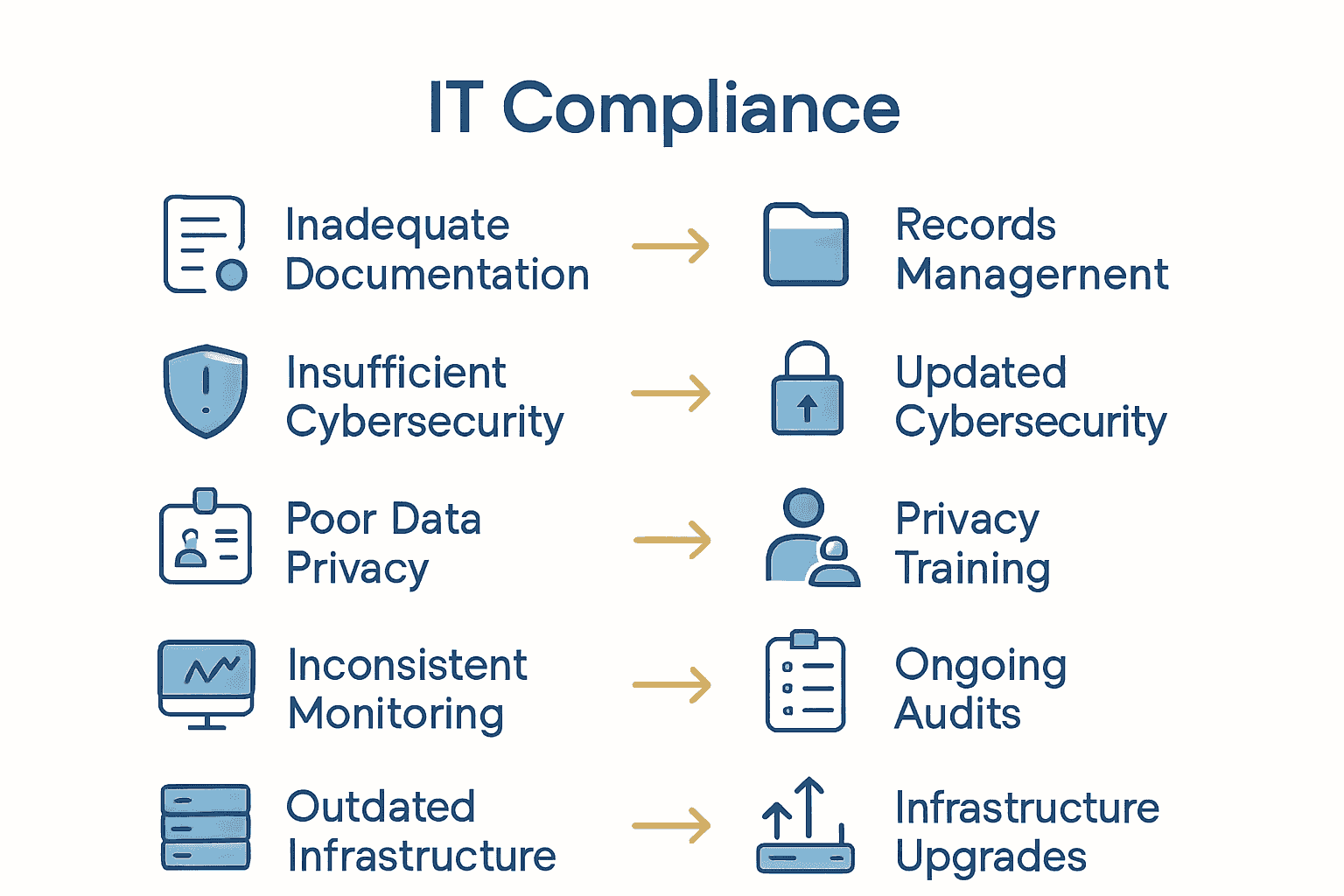
The most common IT compliance risks and mistakes include:
- Inadequate Documentation: Failing to maintain comprehensive and accurate records
- Insufficient Cybersecurity Protocols: Leaving critical systems vulnerable to digital threats
- Poor Data Privacy Management: Mishandling sensitive personal and business information
- Inconsistent Compliance Monitoring: Neglecting ongoing regulatory assessment
- Outdated Security Infrastructure: Using legacy systems with known vulnerabilities
- Limited Staff Training: Failing to educate employees about compliance requirements
Top SMB Cybersecurity Threats highlights that many compliance mistakes stem from a reactive rather than proactive approach. As Business Savers emphasises, regular internal reviews and continuous staff education are fundamental to maintaining robust compliance frameworks.
Brisbane businesses must view compliance not as a burden, but as a strategic opportunity for building organisational resilience. By investing in comprehensive risk assessment, implementing systematic monitoring processes, and fostering a culture of continuous learning, companies can transform potential compliance challenges into competitive advantages that demonstrate professional excellence and build stakeholder trust.
Strengthen Your IT Compliance with IT Start
Brisbane businesses face ongoing challenges in securing their digital environments and maintaining compliance with complex regulations. Your goals include establishing a secure software environment, managing vulnerabilities proactively, and ensuring clear traceability and robust access controls. Understanding that IT compliance is a continuous process means you need a strategic partner who can help you navigate risk assessments, policy development, and regular audits with local expertise.
IT Start specialises in managed IT support, cloud solutions, and cybersecurity services tailored specifically for Brisbane small to medium enterprises. We provide transparent, proactive support that helps you turn compliance requirements into strengths by protecting your business from cyber threats and meeting all legal obligations. Take the next step today by booking a free assessment and consultation through our Contact Us page. Discover how our tailored solutions align with your compliance needs by learning more about access control strategies and cybersecurity essentials for Brisbane SMEs.
Don’t wait until risks become realities. Partner with IT Start and transform IT compliance into a competitive edge that safeguards your business and builds trust with your clients.
Frequently Asked Questions
What is IT compliance?
IT compliance refers to a structured framework that ensures businesses protect their digital infrastructure, meet regulatory requirements, and maintain strong cybersecurity standards.
Why is IT compliance important for businesses?
IT compliance is crucial as it not only helps businesses avoid legal penalties but also protects their digital assets, ensures data privacy, and builds trust with clients and stakeholders.
What are the common types of IT compliance?
Common types of IT compliance include financial services compliance, healthcare compliance, privacy act compliance, cybersecurity standards, and industry-specific regulatory frameworks.
What are typical risks associated with IT compliance?
Typical risks include inadequate documentation, insufficient cybersecurity protocols, poor data privacy management, inconsistent compliance monitoring, outdated security infrastructure, and limited staff training.
Recommended
- Understanding What is IT Security Compliance – IT Start
- How to Secure Business Data for Brisbane SMEs – IT Start
- How to Enforce Cybersecurity for Brisbane Businesses – IT Start
- What Is Cyber Hygiene? Complete Guide for Brisbane SMEs – IT Start
- Understanding Public Health Regulations Canada for Businesses – Probe IT
- What Does Incident Response Mean in A Legal Context?



