Access control is more than just locking up your data. Right now, Aussie small businesses face average cyber incident losses of over $39,000 and that number keeps climbing. Most people think hackers target big corporations first but the real shock is just how exposed small businesses are and how quickly things unravel without the right digital gatekeepers in place.
Table of Contents
- Defining Access Control: What It Is And Its Purpose
- The Importance Of Access Control For Small Businesses
- Key Components And Types Of Access Control Systems
- How Access Control Works: Principles And Mechanisms
- Real-World Applications: Access Control In Business Contexts
Quick Summary
| Takeaway | Explanation |
|---|---|
| Implement Access Control to Protect Data | Access control is essential in safeguarding sensitive information from unauthorized access and potential breaches. |
| Utilize Granular Permissions for Security | Assigning specific access rights ensures users only access necessary resources, enhancing overall security. |
| Prioritize Cybersecurity Training for Employees | Providing comprehensive cybersecurity training reduces risks like human error, which is vital for small businesses. |
| Monitor Access for Proactive Risk Management | Continuous access monitoring aids in identifying suspicious activities and ensures compliance with security protocols. |
| Choose the Right Access Control Model | Selecting an appropriate model (DAC, MAC, RBAC) aligns security strategies with organisational needs and operational efficiency. |
Defining Access Control: What It Is and Its Purpose
Access control represents a fundamental security strategy designed to manage and regulate who can interact with specific resources within an organisational infrastructure. At its core, access control determines precisely which users, systems, or applications are permitted to view, modify, or utilise particular digital or physical assets.
The Fundamental Concept of Access Control
In essence, access control functions like a sophisticated digital gatekeeper. Imagine a high security building where only authorised personnel can enter specific areas based on their credentials and clearance levels. Similarly, in digital environments, access control systems verify a user’s identity and permissions before granting entry to sensitive systems, networks, or data repositories.
The primary objectives of access control include:
- Protecting sensitive information from unauthorised access
- Ensuring data integrity and confidentiality
- Maintaining compliance with regulatory requirements
- Minimising potential security risks and vulnerabilities
How Access Control Protects Organisational Resources
Access control mechanisms operate through multiple authentication and authorisation layers. When a user attempts to access a resource, the system first verifies their identity through credentials like usernames, passwords, biometric data, or security tokens. Once authenticated, the system then determines the specific level of access granted based on predefined permissions.
According to NIST Special Publication 800-63B, effective identity and access management requires a comprehensive approach that balances security requirements with user convenience. This means creating granular permission structures that provide employees exactly the access they need to perform their roles without unnecessary security barriers.
By implementing robust access control strategies, businesses can significantly reduce their vulnerability to data breaches, insider threats, and potential cyber attacks. It transforms security from a reactive measure to a proactive, intelligent system that continuously monitors and manages digital interactions.
The Importance of Access Control for Small Businesses
Small businesses represent a critical segment of the Australian economy, making them increasingly attractive targets for cybercriminals seeking vulnerable digital infrastructures. Access control emerges as a powerful strategy to protect these organisations from potential security breaches and operational disruptions.
Mitigating Cybersecurity Risks
In the digital landscape, small businesses face unique challenges that make robust access control mechanisms essential. Unlike large corporations with extensive IT resources, small enterprises often operate with limited cybersecurity infrastructure, making them more susceptible to targeted attacks.
Key vulnerabilities for small businesses include:
The following table summarises common cybersecurity vulnerabilities small businesses face, as described in the article, and explains the risk each poses in the context of access control.
| Vulnerability | Description |
|---|---|
| Limited IT security budgets | Less funding available for comprehensive defence |
| Less sophisticated defences | Fewer advanced controls, increasing exposure |
| Higher probability of human error | Staff more likely to make mistakes without training |
| Greater risk of insider threats | Fewer checks increase the chance of internal misuse |
| Insufficient cybersecurity training | Lack of training leaves staff unaware of risks |
- Limited IT security budgets
- Less sophisticated technological defences
- Higher probability of human error
- Greater risk of insider threats
- Insufficient employee cybersecurity training
Financial and Operational Protection
Implementing comprehensive access control goes beyond mere technical safeguarding. It represents a strategic approach to protecting a business’s most valuable assets financial data, customer information, and proprietary intellectual property. Unauthorized access can lead to devastating consequences, including financial losses, reputational damage, and potential legal liabilities.
According to the Australian Cyber Security Centre, small businesses experiencing significant cyber incidents can face average financial losses exceeding $39,000. These costs encompass not just immediate financial damage but also potential long term business disruption, customer trust erosion, and regulatory compliance challenges.
By establishing granular access permissions, businesses can create multiple layers of security that significantly reduce potential breach risks. This approach ensures that employees access only the specific systems and data necessary for their roles, minimising the potential attack surface and creating a more controlled digital environment.
Key Components and Types of Access Control Systems
Access control systems represent sophisticated security architectures designed to manage and monitor entry to digital and physical resources. These intricate frameworks enable organisations to create precise, granular control mechanisms that protect sensitive information and critical infrastructure.
Fundamental Access Control Components
Every access control system comprises several essential elements that work together to authenticate, authorise, and track user interactions. The core components include:
- Authentication mechanisms
- Authorisation protocols
- Access management interfaces
- Logging and monitoring systems
- Security credential management
Authentication serves as the initial verification stage, confirming a user’s identity through various methods such as passwords, biometric data, security tokens, or multi factor authentication techniques. This initial screening prevents unauthorized individuals from gaining initial system entry.
Types of Access Control Models
Access control systems typically operate through different architectural models, each offering unique approaches to managing user permissions and resource access. The primary models include:
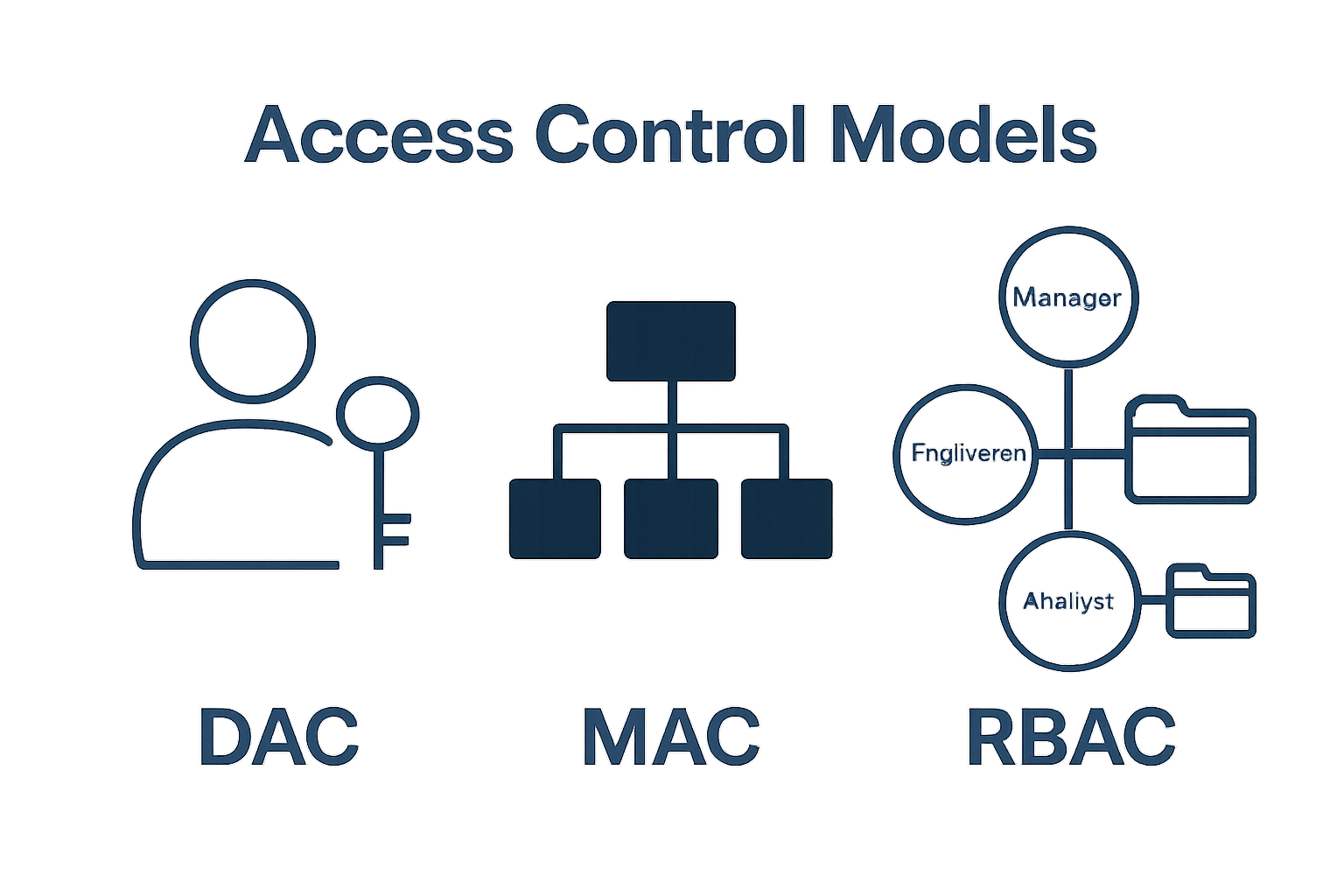
- Discretionary Access Control (DAC): Allows resource owners to determine access permissions
- Mandatory Access Control (MAC): Implements strict, hierarchical access rules managed centrally
- Role Based Access Control (RBAC): Assigns permissions according to organisational roles and responsibilities
According to the Commonwealth Fraud Prevention Centre, implementing robust access control systems requires a comprehensive strategy that addresses both digital and physical security domains. This holistic approach ensures that businesses can effectively manage and mitigate potential security risks across multiple operational environments.
By understanding and strategically implementing these access control components, organisations can create intelligent, adaptive security frameworks that protect critical assets while maintaining operational efficiency and user productivity.
How Access Control Works: Principles and Mechanisms
Access control operates through a complex, multi layered system designed to verify user identities, validate permissions, and protect sensitive organisational resources from unauthorized interactions. This intricate process involves sophisticated technological and procedural mechanisms that work seamlessly to maintain digital security.
Identity Verification and Authentication
The initial stage of access control focuses on comprehensive identity confirmation. This process goes far beyond simple username and password checks, incorporating multiple verification methods to ensure robust security:
- Multifactor authentication techniques
- Biometric verification systems
- Digital security tokens
- Behavioural pattern recognition
- Geographic location tracking
Each verification method adds an additional layer of security, making it exponentially more challenging for unauthorized individuals to gain system access. Sophisticated authentication mechanisms transform traditional security approaches by creating dynamic, intelligent screening processes that adapt to potential threat environments.
Permission Management and Authorization
Once a user’s identity is confirmed, the access control system transitions into permission management. This critical phase determines the precise level of system access granted based on predefined roles, responsibilities, and organizational hierarchies.
The authorization process evaluates multiple contextual factors:
- User role and job function
- Security clearance levels
- Time of access request
- Specific resource being accessed
- Current system security status
According to the Australian Cyber Security Centre, implementing robust access control requires a comprehensive approach that balances security requirements with operational efficiency. This means creating granular permission structures that provide users exactly the access they need without unnecessary complexity.
By integrating advanced technological mechanisms with strategic security protocols, access control systems transform from passive barriers into intelligent, proactive guardians of organizational digital infrastructure.

Real-World Applications: Access Control in Business Contexts
Access control transcends theoretical concepts, emerging as a critical operational strategy for businesses across diverse industries. By implementing sophisticated access management systems, organisations can protect sensitive information, ensure regulatory compliance, and maintain robust security infrastructures.
Sector Specific Access Control Strategies
Different business sectors require tailored access control approaches that address their unique operational challenges and regulatory requirements. Financial services, healthcare, and professional services represent prime examples of industries with complex access management needs.
Key sector considerations include:
- Strict compliance with industry specific regulations
- Protection of confidential client information
- Managing hierarchical permission structures
- Tracking and auditing system interactions
- Preventing unauthorized data modifications
Practical Implementation Scenarios
Business access control manifests through multiple practical applications. For instance, a legal firm might implement role based access control that restricts junior associates from viewing sensitive client documents, while allowing senior partners comprehensive system access.
In financial organisations, access control becomes crucial for preventing internal fraud and maintaining audit trails. Granular permission settings enable businesses to:
- Limit financial transaction authorizations
- Monitor critical system interactions
- Create comprehensive user activity logs
- Restrict access to sensitive financial records
- Implement automatic access revocation for departing employees
According to the Australian Cyber Security Centre, effective access control requires continuous monitoring and adaptive security frameworks that evolve with changing organizational structures and technological landscapes.
By recognizing access control as a dynamic, strategic business tool, organisations can transform their security approach from reactive defence to proactive risk management.
Protect Your Business with Smart Access Control and Local IT Experts
Struggling to manage who can access your sensitive business data? As highlighted in our guide to access control, many small and medium businesses worry about unauthorised access, regulatory compliance, and the risk of data breaches. Gaps in authentication, unclear permission management, and lack of proactive monitoring can leave your most valuable assets exposed. When every decision impacts your reputation and bottom line, you need a partner that treats your security as a priority, not an afterthought.
IT Start specialises in helping Brisbane businesses strengthen their access control systems. Our local team delivers trusted managed IT support, comprehensive cybersecurity solutions, and ongoing risk assessments customised for your industry. Do not wait until a breach disrupts your operations or causes costly fines. Request your free consultation today and let us show how we can safeguard your business, meet compliance goals, and give you peace of mind. Take the next step to protected growth with IT Start.
Frequently Asked Questions
What is access control?
Access control is a security strategy that manages and regulates who can interact with specific resources within an organisation, determining which users, systems, or applications have permission to view, modify, or utilise particular assets.
Why is access control important for businesses?
Access control is important for businesses as it protects sensitive information from unauthorised access, ensures data integrity and confidentiality, helps maintain compliance with regulatory requirements, and minimises potential security risks and vulnerabilities.
What are the different types of access control models?
The primary types of access control models include Discretionary Access Control (DAC), which allows resource owners to set permissions; Mandatory Access Control (MAC), which implements strict access rules managed centrally; and Role-Based Access Control (RBAC), which assigns permissions based on organisational roles and responsibilities.
Below is a comparison table outlining the three primary types of access control models discussed in the article, highlighting their defining features and management approach.
| Access Control Model | Defining Feature | Who Manages Permissions |
|---|---|---|
| Discretionary Access Control (DAC) | Resource owners set access permissions | Individual resource owners |
| Mandatory Access Control (MAC) | Strict central rules and hierarchical structure | Central authority |
| Role-Based Access Control (RBAC) | Permissions assigned based on organisational roles | System administrators |
How can access control mitigate cybersecurity risks for small businesses?
Access control can mitigate cybersecurity risks for small businesses by implementing layered security permissions, ensuring individuals only access the information necessary for their jobs, thereby reducing the potential attack surface and protecting critical assets from breaches.



