Ransomware attacks have surged by more than 20 percent against australian financial firms, leaving sensitive client data increasingly at risk. For Brisbane IT managers, staying ahead means more than just basic antivirus updates. Adopting australian cybersecurity standards and a stepwise approach to risk assessment, access control, endpoint security, and rigorous staff training helps build a defense that meets growing compliance needs and protects your reputation where it matters most.
Table of Contents
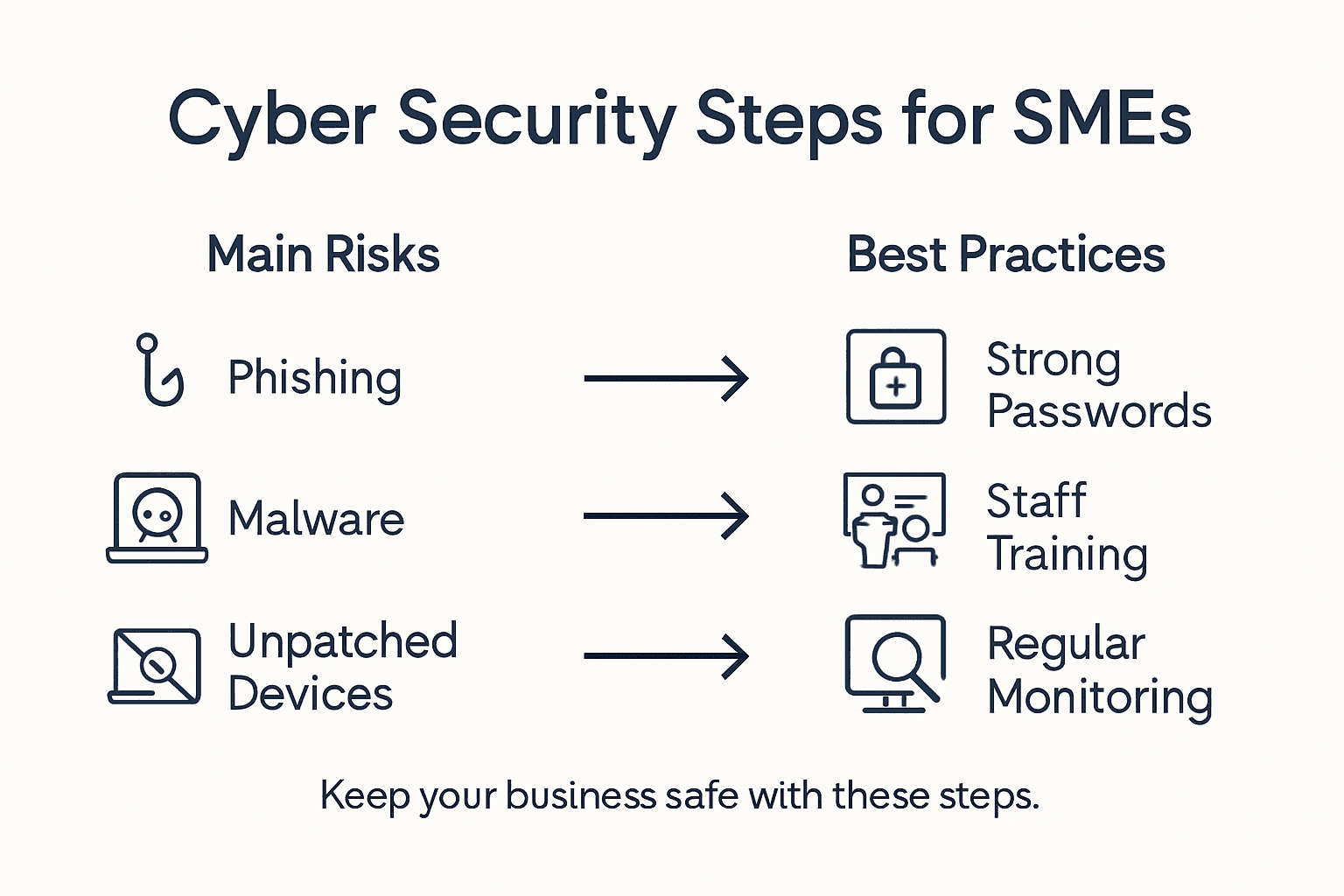
- Step 1: Assess Current Risks And Compliance Requirements
- Step 2: Implement Robust Password And Access Controls
- Step 3: Deploy Effective Endpoint Protection Measures
- Step 4: Educate Staff On Phishing And Social Engineering
- Step 5: Monitor Systems And Verify Ongoing Security
Quick Summary
| Key Insight | Explanation |
|---|---|
| 1. Assess Cyber Risks Thoroughly | Conduct a comprehensive risk assessment to identify vulnerabilities in your IT infrastructure and ensure compliance with Australian standards. |
| 2. Implement Strong Password Policies | Enforce a mandatory password policy and use multi-factor authentication to enhance access security and reduce the risk of unauthorised access. |
| 3. Enhance Endpoint Protection | Deploy advanced endpoint security measures, including real-time monitoring and automated responses, to protect devices from threats. |
| 4. Train Staff on Cybersecurity | Provide structured training and regular simulations to empower employees in recognising and defending against phishing and social engineering attacks. |
| 5. Conduct Ongoing Security Monitoring | Regularly audit systems and set up alerts for unusual activities to maintain a proactive stance against evolving cyber threats. |
Step 1: Assess current risks and compliance requirements
Assessing cyber risks and compliance requirements forms the critical foundation for your Brisbane business’s security strategy. This initial step helps you understand potential vulnerabilities and align your practices with Australian cybersecurity standards.
Begin by conducting a comprehensive risk assessment that maps out your current IT infrastructure, data storage systems, and potential entry points for cyber threats. Understanding the national cyber security compliance framework is essential for identifying specific obligations relevant to your organisation. Review your existing security protocols and compare them against the mandatory reporting requirements outlined in the Australian Cyber Security Strategy 2023-2030.
Focus on evaluating key risk areas such as data protection, network access controls, employee training gaps, and incident response capabilities. Pay close attention to ransomware threats, which have become increasingly prevalent in the Australian small business landscape. Document each identified risk with specific details about potential impact and likelihood of occurrence.
Hot Tip:Create a risk register that not only identifies vulnerabilities but also assigns clear ownership and prioritisation for addressing each potential cyber threat.
Here’s a summary of common cyber risks for Brisbane businesses and their potential impact:
| Risk Area | Likely Impact | Example Scenario |
|---|---|---|
| Data protection | Sensitive information leakage | Client data breached |
| Network access control | Unauthorised internal or external access | Hacker exploits aged credentials |
| Employee training gaps | Increased phishing success rate | Staff clicks on fake email link |
| Incident response | Delayed reaction increases damages | Ransomware spreads unimpeded |
Step 2: Implement robust password and access controls
Strengthening password and access controls represents a critical defense mechanism against potential cyber intrusions for Brisbane businesses. This step focuses on creating a comprehensive security strategy that limits unauthorised system access and protects sensitive organisational data.
Implementing secure by design principles for access management requires a multifaceted approach. Start by establishing a mandatory password policy that enforces complex credentials with minimum requirements such as 12 character length, a mix of uppercase and lowercase letters, numbers, and special symbols. Mandate regular password rotation every 60 to 90 days and prohibit password reuse across different systems. Deploy multi-factor authentication across all critical business platforms, requiring additional verification beyond simple username and password combinations.

Consider implementing role based access controls that restrict system permissions according to specific job functions. This means employees only access the digital resources necessary for their immediate work responsibilities. Regularly audit and update these access permissions, removing credentials for staff who have changed roles or left the organisation. Utilise centralised identity management systems that provide comprehensive visibility and control over user access across your entire digital infrastructure.
Hot Tip:Conduct periodic simulated phishing tests to evaluate and improve your team’s password security awareness and response to potential social engineering attempts.
Step 3: Deploy effective endpoint protection measures
Protecting your digital endpoints is crucial for safeguarding your Brisbane business against emerging cyber threats. This step focuses on implementing comprehensive security measures that shield your organisation’s devices and networks from potential vulnerabilities.
Comprehensive endpoint protection strategies require a multilayered approach that goes beyond traditional antivirus software. Begin by selecting a robust endpoint detection and response system that offers real time monitoring, threat detection, and automated response capabilities. Install advanced antimalware solutions that use artificial intelligence and machine learning to identify and neutralise sophisticated cyber threats before they can penetrate your network.
Implement a rigorous patch management process that ensures all business devices receive timely software updates and security fixes. This includes not just computers and servers, but also mobile devices, tablets, and any other network connected equipment. Configure your endpoint protection tools to automatically update and scan systems, creating a proactive defense mechanism. Establish clear protocols for device management, including mandatory encryption for all business devices, remote wipe capabilities for lost or stolen equipment, and strict controls on personal device usage within your corporate network.
Hot Tip:Configure your endpoint protection systems to generate detailed logs and alerts, enabling your IT team to quickly identify and respond to potential security incidents.
To help you choose appropriate endpoint protection, consider this feature comparison:
| Protection Feature | Basic Antivirus | Advanced Endpoint Security |
|---|---|---|
| Real-time monitoring | Limited | Continuous |
| AI threat detection | Not included | Integrated |
| Automated response | Manual only | Automated |
| Device encryption | Rarely supported | Standard feature |
Step 4: Educate staff on phishing and social engineering
Cybersecurity education is a critical defence mechanism for protecting your Brisbane business from sophisticated digital threats. This step focuses on transforming your employees from potential security vulnerabilities into active defenders of your organisational data.
Comprehensive staff cybersecurity awareness training requires a structured and engaging approach that goes beyond traditional lecture formats. Develop interactive training modules that simulate real world phishing scenarios, helping staff recognise subtle indicators of social engineering attempts. Create practical workshops that demonstrate how cybercriminals manipulate human psychology to gain unauthorised access to sensitive information. Cover key topics such as identifying suspicious email patterns, understanding the risks of sharing confidential information, and recognising sophisticated impersonation techniques.
Establish a clear reporting mechanism that empowers employees to quickly alert your IT security team about potential threats without fear of reprisal. Implement regular simulated phishing tests to measure staff awareness and provide immediate feedback and additional training for those who might be vulnerable. Develop a continuous learning program that keeps staff updated on emerging social engineering tactics, ensuring your team remains adaptable and vigilant against evolving cyber risks.
Hot Tip:Create a monthly cybersecurity newsletter with real world examples of recent phishing attempts to keep your team engaged and informed about the latest digital threats.
Step 5: Monitor systems and verify ongoing security
Ongoing system monitoring represents a critical defense strategy for protecting your Brisbane business against evolving cyber threats. This step focuses on implementing continuous surveillance and verification mechanisms that proactively identify and mitigate potential security risks.
Comprehensive security monitoring frameworks require a multifaceted approach that integrates advanced technological tools with strategic human oversight. Deploy security information and event management systems that provide real time insights into network activities, tracking unusual login patterns, unexpected data transfers, and potential unauthorized access attempts. Configure automated alerts that instantly notify your IT security team about suspicious activities, enabling rapid response and minimising potential damage.
Establish a regular audit schedule that systematically reviews system logs, access permissions, and security configurations. Conduct quarterly vulnerability assessments that test your network defenses using ethical hacking techniques and penetration testing. Maintain detailed documentation of all monitoring activities, creating a comprehensive record that supports compliance requirements and helps identify long term security trends. Develop a continuous improvement process that adapts your security strategies based on insights gained from ongoing monitoring and verification activities.
Hot Tip:Schedule monthly security review meetings where your IT team discusses monitoring insights and collaboratively develops strategies to address emerging cyber risks.
Strengthen Your Brisbane Business Cybersecurity with IT Start
The step-by-step guide highlights critical challenges Brisbane SMEs face such as managing risks, enforcing strong password and access controls, deploying endpoint protection, and ongoing staff education. These pain points not only expose your business to costly data breaches but also risk non-compliance with Australian cybersecurity standards. IT Start understands that navigating these complex security demands while maintaining operational efficiency can feel overwhelming and risky.
With our proactive managed IT support and specialised cybersecurity services tailored for Brisbane businesses, IT Start becomes your trusted strategic partner. We help you assess vulnerabilities, implement robust access controls, deploy advanced endpoint protection, and deliver ongoing staff training to transform your organisation’s cyber posture. Our local expertise and high industry standards mean you gain clear, actionable insights and fast incident responses that minimise damage and safeguard your reputation.
Ready to protect your Brisbane SME from evolving cyber threats and ensure compliance? Discover how IT Start’s cybersecurity solutions can secure your critical systems today. Don’t wait until risks become emergencies. Contact us now for a free assessment and consultation tailored specifically to your business needs.
Frequently Asked Questions
How can I conduct a comprehensive risk assessment for my SME?
To conduct a comprehensive risk assessment, map out your current IT infrastructure, data storage systems, and potential entry points for cyber threats. Document identified risks and evaluate their potential impacts and likelihoods, and consider doing this every 6-12 months to keep your assessment up-to-date.
What password policies should my SME implement for better security?
Your SME should establish a mandatory password policy requiring complex credentials, such as passwords that are at least 12 characters long and include uppercase letters, lowercase letters, numbers, and special symbols. Rotate these passwords every 60 to 90 days and ensure that your employees do not reuse passwords across different systems.
What key endpoint protection measures should I implement for my business?
Implement comprehensive endpoint protection by selecting advanced security solutions that include real-time monitoring, AI threat detection, and automated response capabilities. Ensure that you also maintain a strict patch management process for all business devices, updating them promptly, ideally as soon as updates are available.
How can I train my staff to recognise phishing and social engineering attacks?
Develop interactive training modules that simulate real-life phishing scenarios so staff can learn to identify signs of social engineering. Supplement this with regular simulated phishing tests to reinforce their learning and measure their awareness regularly.
What ongoing monitoring practices should my SME adopt for cyber security?
Establish continuous system monitoring by deploying security information and event management systems to track unusual network activities. Conduct quarterly vulnerability assessments and maintain detailed documentation of all monitoring activities to support compliance and inform future security strategies.
How often should I review and update my cyber security practices?
Review and update your cyber security practices at least quarterly, ensuring your strategies adapt to emerging threats. Schedule regular meetings to discuss insights from your ongoing monitoring efforts and adjust your practices based on these discussions.
Recommended
- Cyber Security Actions for Brisbane Businesses – IT Start
- What Is Cyber Security and Why Brisbane SMEs Rely On It – IT Start
- Cyber Security Vulnerabilities – Why Brisbane SMEs Need Protection – IT Start
- How to Enforce Cybersecurity for Brisbane Businesses – IT Start
- 7 Essential Steps for a Digital Skills Checklist Success – BizDev Strategy
- Business Social Media Training for Regional Success



