Every australian financial services firm in Brisbane faces rising cyber threats that put sensitive data and business reputations at risk. Recent reports show over 68 percent of data breaches can be traced back to human error, making targeted defence strategies more crucial than ever. For IT security administrators, staying ahead means mastering the latest risk mitigation tactics and compliance requirements to build resilient systems and foster a proactive security culture.
Table of Contents
- Defining Network Security Administration Today
- Essential Tasks And Technology In 2026
- Australian Laws And Compliance Requirements
- Managing Threats, Incidents, And Human Error
- Key Mistakes, Costs, And Security Culture
Key Takeaways
| Point | Details |
|---|---|
| Evolving Role | Network security administration is now a strategic business function, emphasising proactive risk management and organisational resilience. |
| Technological Integration | Modern security practices require the application of AI, machine learning, and automated systems to anticipate and mitigate cyber threats. |
| Compliance Focus | Administrators must develop compliance roadmaps aligning with Australian laws, emphasising proactive risk and incident management. |
| Cultural Shift | A strong security culture is vital, necessitating continuous education and involvement from all levels of the organisation to mitigate human errors effectively. |
Defining Network Security Administration Today
Network security administration has evolved from a technical specialisation into a strategic business function crucial for protecting organisational assets in the digital landscape. In Brisbane’s competitive business environment, network security administrators are now responsible for comprehensive digital defence strategies that go far beyond traditional IT protection methods. The role demands a holistic approach to safeguarding digital infrastructure, considering national cybersecurity strategic frameworks that emphasise resilience and proactive risk management.
Today’s network security administration involves multiple complex dimensions, including infrastructure protection, threat intelligence, incident response, and continuous vulnerability assessment. Security professionals must develop robust governance frameworks that align technical controls with organisational objectives. This means creating comprehensive security policies, implementing advanced monitoring systems, and establishing clear protocols for responding to potential cyber incidents. Security governance frameworks now require designated security executives to not only manage technological risks but also foster a culture of cybersecurity awareness across entire organisations.
Modern network security administrators in Brisbane must balance technical expertise with strategic thinking. They are expected to understand emerging threats, manage complex technological ecosystems, and translate technical risks into business language that executives can comprehend. This requires skills in areas such as threat modelling, risk assessment, compliance management, and continuous learning about evolving cybersecurity landscapes. Key responsibilities include protecting critical infrastructure, ensuring regulatory compliance, and developing resilient systems that can withstand increasingly sophisticated cyber attacks.
Pro tip:Develop a continuous learning mindset by dedicating at least two hours weekly to studying emerging cybersecurity trends and technologies specific to the Australian business context.
Here’s a high-level comparison of traditional vs. modern network security administration roles:
| Aspect | Traditional Approach | Modern Approach (2026) |
|---|---|---|
| Focus | Technical controls | Business-aligned governance |
| Main Responsibilities | Infrastructure management | Risk assessment and strategy |
| Required Skills | IT troubleshooting | Threat modelling, compliance, AI |
| Communication | Technical teams only | Execs, all staff, external partners |
| Culture Role | Reactive, tech-focused | Proactive, organisation-wide |
Essential Tasks And Technology In 2026
The landscape of network security administration is rapidly transforming, with emerging technologies and sophisticated threat landscapes reshaping how Brisbane businesses approach cybersecurity. Strategic cybersecurity frameworks highlight critical tasks for 2026, emphasising proactive risk management and leveraging advanced technological capabilities. Network security administrators must now integrate artificial intelligence, machine learning, and automated threat intelligence systems to create dynamic, responsive defence mechanisms that can anticipate and neutralise potential cyber risks before they materialise.

Key technological priorities for 2026 include implementing comprehensive security control frameworks that go beyond traditional protection methods. The Australian Signals Directorate’s Essential Eight mitigation strategies provide a robust blueprint for organisations, focusing on critical controls such as application whitelisting, robust patch management, multi-factor authentication, and comprehensive user application hardening. These strategies are no longer optional but fundamental requirements for organisations seeking to maintain resilient digital infrastructures in an increasingly complex cyber ecosystem.
Beyond technological implementations, network security administrators in 2026 will need to cultivate advanced skill sets that blend technical expertise with strategic thinking. This includes developing capabilities in threat modelling, risk assessment, cloud security architecture, and understanding the intricate relationships between technological systems and organisational risk profiles. The role will demand continuous learning, with professionals required to stay ahead of emerging threat vectors, understand evolving regulatory landscapes, and translate complex technological risks into actionable business strategies that protect organisational assets and maintain operational continuity.
Pro tip:Invest in quarterly cybersecurity skills assessments and allocate dedicated professional development budgets to ensure your technical capabilities remain cutting-edge and aligned with the rapidly evolving threat landscape.
Australian Laws And Compliance Requirements
Network security administrators in Brisbane must navigate a complex landscape of cybersecurity legislation that demands rigorous compliance and strategic risk management. The Independent Review of the Security of Critical Infrastructure Act 2018 provides critical insights into how small and medium enterprises must approach regulatory requirements, emphasising proportional obligations that balance national security needs with economic practicality. This means SMEs are not expected to implement identical security measures as large corporations, but must still demonstrate a comprehensive understanding of their specific cybersecurity risks and mitigation strategies.
Australian regulatory frameworks increasingly focus on proactive risk management and transparent incident reporting. Industry standards issued by the eSafety Commissioner now mandate detailed risk assessments, comprehensive incident response protocols, and robust user safety management practices. Network security administrators must develop compliance roadmaps that not only meet legal requirements but also demonstrate a commitment to protecting organisational and customer data. This involves creating documented policies, conducting regular security audits, maintaining detailed incident response plans, and ensuring transparent communication channels for reporting potential breaches.
The evolving cybersecurity legal landscape requires network security administrators to adopt a holistic approach that integrates technological solutions with strategic governance. Compliance is no longer a checkbox exercise but a continuous process of risk assessment, adaptation, and improvement. Administrators must stay informed about emerging regulations, understand the nuanced requirements specific to their industry, and develop flexible security frameworks that can quickly adapt to changing legislative expectations. This demands ongoing education, participation in industry forums, and a proactive approach to understanding the intersection of technology, law, and organisational risk management.
Pro tip:Develop a dedicated compliance tracking system that maps your current security practices against existing and emerging Australian cybersecurity regulations, allowing for real-time updates and strategic adjustments.
Managing Threats, Incidents, And Human Error
Network security administrators face an increasingly complex challenge in protecting Brisbane businesses, with human factors emerging as the most significant vulnerability in cybersecurity infrastructure. Comprehensive digital transformation research reveals that human error accounts for approximately 68% of data breaches, highlighting the critical need for robust training and systemic risk mitigation strategies. These errors range from inadvertent data mishandling to configuration mistakes that can compromise entire organisational networks, underscoring the importance of developing comprehensive threat management approaches that address both technological and human elements.
Effective incident response requires a multifaceted approach that integrates technological safeguards with human-centric risk management. Security risk management reviews from Australian government agencies emphasise the importance of implementing procedural controls that combine technical solutions with targeted employee training. This includes developing clear incident reporting protocols, creating structured response mechanisms, and establishing ongoing cybersecurity awareness programs that transform employees from potential vulnerabilities into active defenders of organisational security. Network security administrators must design systems that not only detect and respond to threats but also proactively prevent human-related security incidents through education and strategic intervention.
The most sophisticated threat management strategies recognise that human error is not simply a technical problem but a complex organisational challenge. This requires network security administrators to develop holistic approaches that combine technological solutions with psychological understanding. Implementing multi-factor authentication, creating intuitive security protocols, developing clear communication channels for reporting potential threats, and designing user-friendly security systems can significantly reduce the likelihood of human-related security incidents. Regular simulated phishing exercises, personalised security training, and creating a culture of security awareness are crucial components of a comprehensive approach to managing human-related cybersecurity risks.
Pro tip:Develop a monthly micro-learning cybersecurity awareness program that delivers short, engaging security training modules directly to employees’ devices, making continuous education both accessible and compelling.
Key Mistakes, Costs, And Security Culture
Network security administrators in Brisbane face significant challenges in preventing cybersecurity mistakes that can result in catastrophic financial and reputational damages. The Australian Cyber Security Strategy highlights the profound impact of poor cyber hygiene and inadequate incident preparedness, revealing that seemingly minor oversights can lead to substantial organisational vulnerabilities. These mistakes often stem from a lack of comprehensive security awareness and insufficient investment in proactive risk management strategies, which can exponentially increase the potential costs of cyber incidents.
Common cybersecurity mistakes plague many small to medium enterprises, creating significant exposure to potential breaches. Comprehensive research identifies critical vulnerabilities including weak password practices, neglecting software updates, insufficient employee training, and inadequate backup systems. These errors are not merely technical shortcomings but reflect deeper organisational challenges in developing a robust security culture. The financial implications are substantial, with potential breach remediation costs far exceeding the investment required for preventative measures. Network security administrators must therefore focus on transforming organisational attitudes towards cybersecurity, moving beyond technical solutions to create holistic, engagement-driven security strategies.
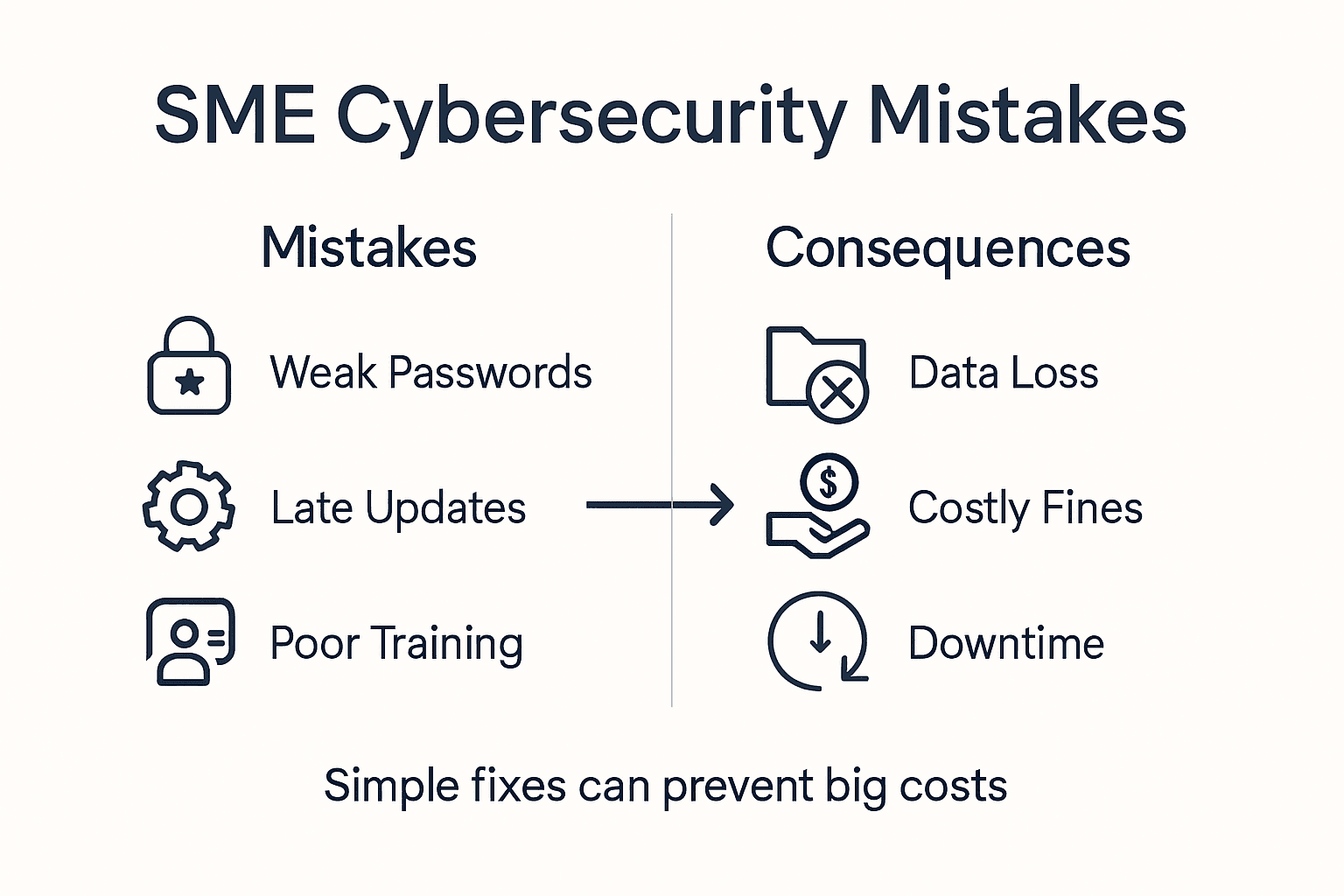
The following table summarises common cybersecurity mistakes and their potential impacts for Brisbane businesses:
| Mistake | Typical Consequence | Example Cost to Business |
|---|---|---|
| Weak password practices | Unauthorised account breaches | Data loss, financial theft |
| Delayed software updates | Exposure to known vulnerabilities | Ransomware downtime expenses |
| Inadequate staff training | Increased risk of social engineering | Reputation damage post-breach |
| Insufficient backups | Loss of data after incidents | Recovery costs, customer trust |
| Poor incident preparedness | Slow breach detection, larger impacts | Fines, extended recovery time |
Cultivating an effective security culture requires a multifaceted approach that goes beyond traditional training programs. This involves creating an environment where every employee understands their role in maintaining organisational cybersecurity, from frontline staff to executive leadership. Successful strategies include regular simulated security scenarios, transparent communication about potential risks, recognising and rewarding security-conscious behaviour, and developing clear, accessible policies that empower employees to make informed security decisions. Leadership must demonstrate a genuine commitment to cybersecurity, integrating security considerations into everyday business processes and decision-making frameworks.
Pro tip:Implement a quarterly security awareness competition that rewards teams or individuals who demonstrate exceptional understanding and application of cybersecurity best practices, transforming security education into an engaging and motivational experience.
Secure Your Brisbane SME With Expert Network Security Administration
The article highlights the growing complexity of network security administration and the urgent need for Brisbane SMEs to bridge technical cybersecurity with strategic business governance. Common challenges such as managing human error, meeting evolving Australian compliance requirements, and adopting proactive risk management can feel overwhelming. If your business struggles with understanding how to align threat modelling, incident response, and security culture with operational goals then you are not alone.
At IT Start, we specialise in helping Brisbane businesses transform these challenges into strengths. Our managed IT support and tailored cybersecurity services focus on building resilient, compliant, and user-aware environments that protect your critical assets while supporting your company growth. We emphasise continuous improvement with services designed around frameworks like the ASD Essential Eight and compliance roadmaps tailored to Australian laws. Our local expertise ensures that your network security administration is business-aligned and future-ready.
Take control of your cybersecurity strategy today. Discover how our proactive, transparent approach can reduce human error risks and boost your organisation’s resilience. Contact us for a free consultation at IT Start Contact and start building a security culture that empowers every employee. Don’t wait until an incident forces costly damage — partner with us now to safeguard your Brisbane SME with trusted network security administration.
Frequently Asked Questions
What is the role of a network security administrator?
A network security administrator is responsible for protecting an organisation’s digital assets by developing and implementing comprehensive security strategies, managing technological risks, and ensuring compliance with cybersecurity laws.
How can small to medium enterprises improve their network security?
Small to medium enterprises can improve their network security by implementing strong password policies, conducting regular software updates, providing comprehensive employee training, and maintaining robust backup systems.
What are common cybersecurity mistakes SMEs should avoid?
Common cybersecurity mistakes include weak password practices, delayed software updates, inadequate staff training, insufficient backups, and poor incident preparedness, all of which can lead to significant vulnerabilities and financial losses.
Why is human error a significant factor in cybersecurity breaches?
Human error is a major factor in cybersecurity breaches as it accounts for a significant percentage of data incidents. Lack of training and awareness can lead to mishandling data or falling prey to social engineering attacks.
Recommended
- Network Security Practices – Safeguarding Brisbane Firms – IT Start
- What Cyber Security Protects for Brisbane Businesses – IT Start
- How to Secure Business WiFi for Brisbane SMEs Effectively – IT Start
- What is Network Security? Understanding Its Importance – IT Start
- Web Security Explained: Protecting Your Business Online – ResponsiveWebsiteDesign



