Cyber attacks hit nearly 43 percent of Australian small businesses every year, yet many companies still overlook gaps in their network security. In Brisbane, where digital operations are growing fast, one weak password or missed update can expose your entire system to hackers. Strengthening your defences is not just about technology. Smart planning, regular testing, and a security-minded team give you the upper hand against modern cyber threats.
Table of Contents
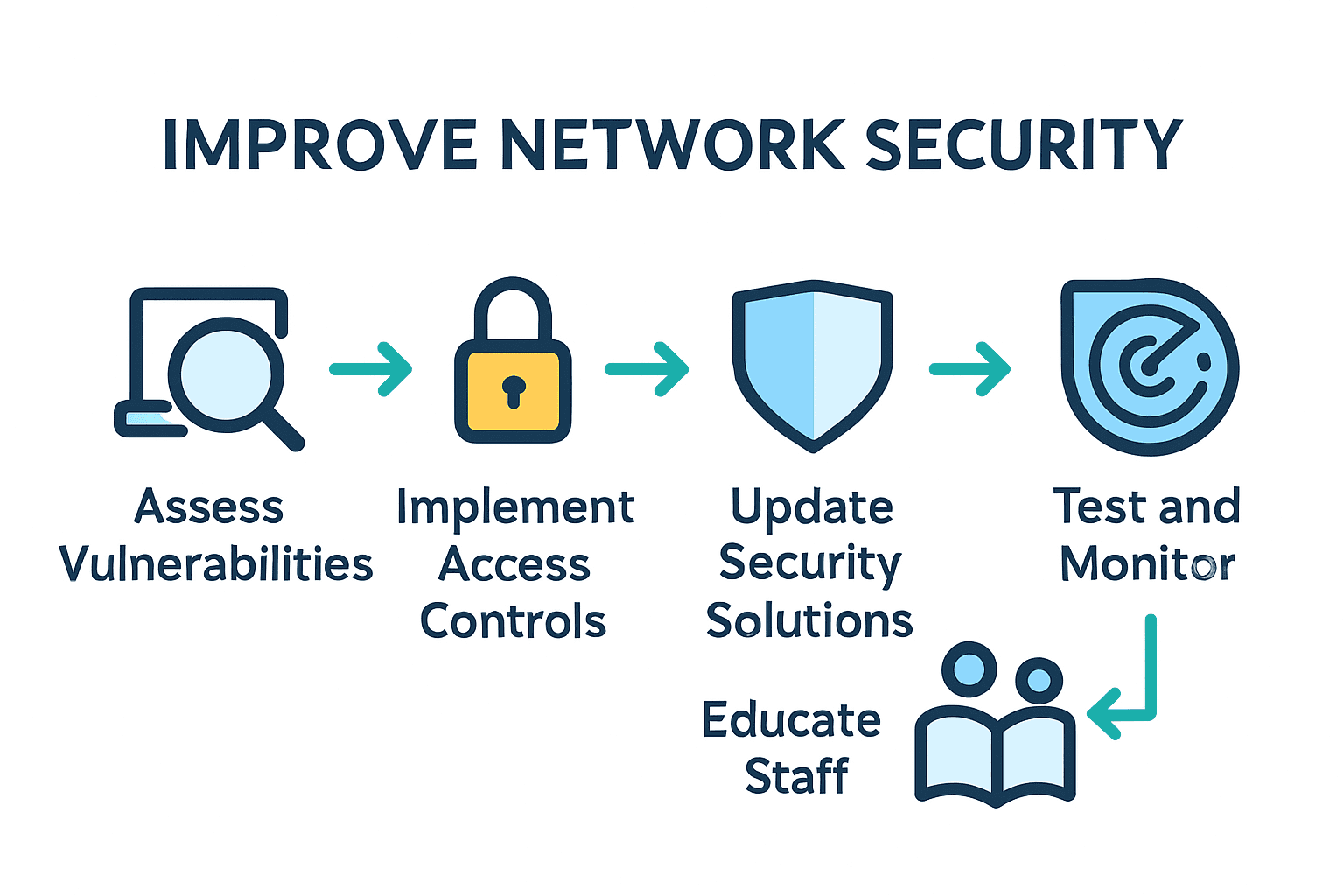
- Step 1: Assess Current Network Vulnerabilities
- Step 2: Implement Robust Access Controls
- Step 3: Install and Update Security Solutions
- Step 4: Educate Staff on Cybersecurity Practices
- Step 5: Test and Monitor Network Defences
Quick Summary
| Key Point | Explanation |
|---|---|
| 1. Identify network vulnerabilities quickly | Conduct a thorough network mapping to discover all devices and potential weaknesses for prompt remediation. |
| 2. Implement strict access controls | Create unique user accounts and enforce multi-factor authentication to enhance security and track user activities effectively. |
| 3. Use advanced security solutions | Invest in comprehensive tools like firewalls and antivirus software with automated patch management to protect against cyber threats. |
| 4. Educate employees on security practices | Develop ongoing training programs to raise awareness about cyber threats and effective responses among staff members. |
| 5. Regularly test and monitor network defences | Perform consistent vulnerability scans and penetration tests, configuring alerts for unusual network activity to preemptive threats. |
 |
|
Step 1: Assess Current Network Vulnerabilities
Knowing your network’s weak points is the first critical step in strengthening your cybersecurity defences. This assessment will help you identify potential entry points that malicious actors might exploit. According to the Australian Cyber Security Centre, understanding where your valuable and sensitive information is located allows you to apply appropriate security measures proportionate to potential risks.
Start by conducting a comprehensive network mapping exercise. This involves creating a detailed inventory of all connected devices including computers, servers, routers, mobile devices, and network infrastructure components. Document the operating systems, software versions, and current patch levels for each device. Pay special attention to legacy systems or equipment running outdated software which can become significant vulnerability points. Look for unpatched systems or those running end of life operating systems that no longer receive security updates.
As the Australian Cyber Security Centre recommends, prioritize patching vulnerabilities within 48 hours of discovery. Malicious actors use automated tools to rapidly exploit known security weaknesses, so swift action is critical. Consider engaging a professional IT security audit team who can perform advanced vulnerability scanning and provide an objective assessment of your network’s current security posture. They can help identify hidden risks and recommend targeted improvements tailored to your specific Brisbane small business infrastructure.
In our network security guide, we provide additional insights into creating a robust security strategy that protects your business from emerging cyber threats.
Step 2: Implement Robust Access Controls
Establishing strong access controls is your critical defence against unauthorized network entry. This step involves creating a structured approach to managing who can access your business systems and what level of permissions they receive. Australian National Audit Office recommendations highlight the importance of carefully managing user access to reduce potential security vulnerabilities.
Begin by implementing a comprehensive user authentication strategy. Create unique user accounts for each team member with specific access levels based on their job responsibilities. Eliminate shared accounts completely as they make tracking individual actions impossible. Implement multi factor authentication which requires additional verification beyond simple passwords. This might include biometric checks fingerprint scans or temporary access codes sent to mobile devices. Password policies should mandate complex passwords with minimum length requirements and regular mandatory changes.
The Australian Cyber Security Centre suggests regularly reviewing and auditing user permissions. Develop a systematic process for granting removing and updating access rights as employees change roles or leave the organization. Privileged accounts with administrative access require extra scrutiny and should be monitored closely.
 Consider implementing automated systems that can track user activities log potential security incidents and provide real time alerts for suspicious access attempts.
Consider implementing automated systems that can track user activities log potential security incidents and provide real time alerts for suspicious access attempts.
Learn more about creating comprehensive access control strategies in our detailed guide about access control to protect your Brisbane small business from potential security breaches.
Step 3: Install and Update Security Solutions
Implementing robust security solutions is your frontline defence against potential cyber threats. This step involves strategically selecting protecting and maintaining critical cybersecurity tools to safeguard your Brisbane small business network. Australian National Audit Office research emphasizes the critical importance of a responsive and effective security patch management strategy.
Start by investing in comprehensive security solutions that provide multi layered protection. This includes installing next generation antivirus software endpoint protection platforms firewalls and intrusion detection systems. Ensure these solutions offer real time monitoring threat detection and automated response capabilities. Configure each solution to provide maximum coverage while minimizing potential system performance impacts. Pay special attention to solutions that offer centralized management allowing you to monitor and control security across multiple devices from a single dashboard.
The Australian Cyber Security Centre strongly recommends implementing a proactive patching strategy. Develop a systematic approach to updating all software and security solutions within 48 hours of a vulnerability being identified. Set up automated patch management systems that can quickly deploy security updates across your entire network. This minimizes the window of opportunity for potential cyber attacks. Regular vulnerability scanning and penetration testing will help you identify and address potential weaknesses before they can be exploited.
For more detailed insights into protecting your business infrastructure, check out our guide on preventing cyber attacks that provides comprehensive strategies tailored for Brisbane businesses.
Step 4: Educate Staff on Cybersecurity Practices
Transforming your team into a human firewall is crucial for comprehensive network security. Staff education represents your most adaptable and responsive defence mechanism against evolving cyber threats. Australian Cyber Security Centre research emphasizes the critical role of organisational awareness in strengthening overall cybersecurity posture.
Develop a structured cybersecurity training program that covers key risk areas. Focus on practical skills like identifying phishing emails recognizing social engineering tactics and understanding proper password management. Create interactive workshops that simulate real world cyber attack scenarios helping employees develop muscle memory for responding to potential threats. Include specific modules on mobile device security email safety web browsing protocols and the risks associated with public WiFi networks. Conduct regular simulated phishing tests to measure and improve employee awareness providing immediate feedback and additional training for those who need support.
Implement a continuous learning approach to cybersecurity education. Schedule quarterly training sessions to keep staff updated on emerging threats and new protection strategies. Develop clear communication channels where employees can quickly report suspicious activities without fear of reprimand. Consider creating a reward system that recognizes and incentivizes proactive security behaviour. Remember that cybersecurity is a shared responsibility where every team member plays a critical role in protecting your business infrastructure.
For more comprehensive insights into building a robust security awareness culture, explore our user security awareness training guide designed specifically for Brisbane businesses.
Step 5: Test and Monitor Network Defences
Proactively testing and monitoring your network defences is crucial for identifying and addressing potential security vulnerabilities before they can be exploited. This ongoing process helps you stay one step ahead of potential cyber threats targeting Brisbane small businesses. Australian National Audit Office recommendations emphasize the importance of conducting regular threat assessments and comprehensive security reviews.
Implement a comprehensive network monitoring strategy that includes multiple layers of testing and surveillance. Conduct regular vulnerability scans using advanced security tools that can detect potential weaknesses across your entire network infrastructure. Schedule periodic penetration testing where ethical hackers attempt to breach your systems using real world attack techniques. These simulated attacks will help you understand and address potential security gaps. Set up real time monitoring systems that track network traffic user activities and potential suspicious behaviours. Configure alerts that immediately notify your IT team about unusual access attempts unauthorized login attempts or potential security breaches.
The Australian Cyber Security Centre recommends adopting a proactive approach to network defence monitoring. Develop a robust incident response plan that outlines clear steps for addressing and mitigating potential security threats. Maintain detailed logs of all network activities and conduct quarterly comprehensive security audits. Use automated tools that provide detailed insights into your network security posture and generate actionable recommendations for improvement. Remember that network defence is an ongoing process requiring continuous attention and adaptation to emerging cyber threats.
For more insights into strengthening your business network security, explore our guide on improving network security tailored specifically for Brisbane businesses.
Strengthen Your Brisbane Business Network Security with IT Start
Improving network security is vital for any Brisbane SME facing challenges like patching vulnerabilities swiftly, controlling access effectively, and educating staff on cyber threats. You might feel overwhelmed managing these complex tasks alone while staying focused on growing your business. IT Start understands these pain points and offers tailored managed IT support and proactive cybersecurity services built for local Brisbane businesses just like yours.
Take control of your network defence with expert solutions that include real-time monitoring, multi-factor authentication setup, and ongoing staff security training. Don’t wait until a costly breach disrupts your operations. Discover how our certified team can help you improve operational efficiency, ensure compliance, and significantly reduce cybersecurity risks today. Start your journey by requesting a free security assessment and connect with Brisbane’s trusted IT partner. Learn more about creating a safer business environment through our network security guidance and begin protecting what matters most now.
Frequently Asked Questions
How can I assess my current network vulnerabilities in my small business?
Start by conducting a thorough network mapping exercise to inventory all connected devices. Document their operating systems and software versions and prioritize patching any identified vulnerabilities within 48 hours.
What steps should I take to implement robust access controls for my team?
Create unique user accounts tailored to job responsibilities and eliminate shared accounts. Implement multi-factor authentication and regularly review user permissions to ensure proper access levels are maintained throughout your organization.
Which security solutions should I install to protect my network?
Invest in comprehensive multi-layered security solutions, including antivirus software, firewalls, and intrusion detection systems. Ensure these are updated promptly—ideally within 48 hours following a discovered vulnerability—to maintain a strong defense against cyber threats.
How can I effectively educate my staff on cybersecurity practices?
Develop a structured training program that includes practical skills like recognizing phishing attempts and proper password management. Schedule regular training sessions quarterly to keep your team informed about emerging threats and reinforce good security habits.
What is the best approach for testing and monitoring my network defenses?
Implement a multi-layered network monitoring strategy, including regular vulnerability scans and periodic penetration testing. Set up real-time alerts for unusual activities to proactively identify and address potential security weaknesses in your systems.
How often should I review and update my cybersecurity measures?
Conduct comprehensive security reviews and audits at least quarterly to assess your current defenses. Establish a system for continuous monitoring to adapt to new cyber threats as they emerge, ensuring your security posture remains strong.



