Cybercrime is costing small Queensland businesses an average of A$49,600 each year. For every organisation, that risk goes far beyond lost money. With most companies now facing regular cyber incidents, building a strong security culture is not just good practice, it is a critical business need. By understanding your unique risks and designing meaningful training, you can help your team protect assets, reputation, and day-to-day operations.
Quick Summary
| Key Point | Explanation |
|---|---|
| 1. Assess unique cybersecurity risks | Map your digital ecosystem to identify vulnerabilities that your business specifically faces. |
| 2. Develop tailored training content | Create training materials that address role-specific cybersecurity challenges relevant to employees’ daily tasks. |
| 3. Deliver engaging training sessions | Use interactive formats with short sessions to enhance participation and real-world application of cybersecurity knowledge. |
| 4. Test understanding with practical assessments | Implement scenario-based evaluations to gauge knowledge retention and readiness in handling cyber threats. |
| 5. Regularly review and update training | Continuously adapt your training program based on testing results and evolving security threats to maintain effectiveness. |
Table of Contents
- Step 1: Assess Business Security Risks And Needs
- Step 2: Develop Tailored User Training Materials
- Step 3: Deliver Interactive Training Sessions
- Step 4: Test Employee Awareness And Understanding
- Step 5: Review Outcomes And Reinforce Key Practices
Step 1: Assess Business Security Risks and Needs
Brisbane businesses need a systematic approach to understanding their unique cybersecurity landscape. In this critical first step, you’ll learn how to thoroughly evaluate your organisation’s vulnerabilities and design a targeted security awareness training strategy.
Start by mapping out your entire digital ecosystem. Walk through each department and identify the systems, devices, and data pathways that could potentially expose your business to cyber threats. According to Business Queensland, small Queensland businesses face an average cybercrime cost of A$49,600 making comprehensive risk assessment absolutely crucial.
Focus on pinpointing specific risks relevant to your industry. As the Queensland Government’s Cyber Wardens initiative reveals, four in five small businesses experienced a cyber incident in the past year. This means you must pay special attention to potential entry points like email systems, banking platforms, and customer relationship management tools.
Create a risk inventory that categorises potential vulnerabilities. Document everything from outdated software and weak passwords to potential phishing entry points and data storage practices. Consider conducting a preliminary internal audit or engaging a professional IT security consultant who can provide an objective assessment.
Pro Tip: Document every identified risk, no matter how small. Seemingly minor vulnerabilities can become significant security breaches if left unaddressed.
Once you have mapped out your risks, prioritise them based on potential impact and likelihood of occurrence. Some threats will require immediate intervention while others can be managed through gradual improvements in your security awareness training program.
This initial assessment sets the foundation for a robust security strategy. By understanding your specific risks, you can now move forward with designing targeted training modules that address your organisation’s unique cybersecurity challenges.
Step 2: Develop Tailored User Training Materials
Now that you have identified your specific security risks, it is time to transform those insights into engaging and relevant training content. Your goal is to create learning materials that speak directly to your team’s unique challenges and resonate with their daily work experiences.
Begin by segmenting your training approach based on different roles and departments within your organisation. The Queensland Government’s Cyber Wardens program demonstrates the power of sector-specific training, offering tailored webinars for industries like healthcare, construction, and tourism. This targeted method ensures that each team member receives information most relevant to their specific work environment.
Consider leveraging adaptive learning technologies to enhance training effectiveness. Recent academic research suggests using advanced AI technologies to dynamically personalise cybersecurity content. A study from academic research indicates that personalized training experiences can significantly improve engagement and learning outcomes compared to generic approaches.
Structure your materials to include a mix of formats: interactive modules, short video tutorials, practical scenario-based exercises, and quick reference guides. This multi-modal approach caters to different learning styles and helps maintain participant interest. Ensure each resource directly connects to the specific risks you identified during your initial assessment.
Pro Tip: Include real world examples from your own business context. Practical scenarios that employees can immediately relate to will make the training more memorable and impactful.
Prioritise creating content that is concise, visual, and action-oriented. Break complex security concepts into digestible chunks. Use clear language, avoid technical jargon, and focus on practical steps employees can take to protect the business.
Remember that developing training materials is an iterative process. Plan to regularly review and update your content based on emerging threats, technological changes, and feedback from your team. This approach ensures your security awareness training remains current and effective.
Step 3: Deliver Interactive Training Sessions
With your tailored training materials ready, the next critical step is transforming those resources into dynamic learning experiences that capture your team’s attention and drive meaningful security awareness. Your objective is to create engaging sessions that turn cybersecurity knowledge into practical workplace skills.
Business Queensland recommends leveraging interactive formats like the free Cyber Wardens program which offers flexible self-paced courses and webinars. Follow this approach by designing sessions that blend presentation techniques with hands-on learning opportunities.
Start by scheduling multiple short training segments rather than one lengthy workshop. Aim for 30 to 45 minute sessions that include live demonstrations, real-world scenario discussions, and interactive problem-solving exercises. The Queensland Government’s public sector training model demonstrates how interactive modules can effectively enhance awareness while minimising workflow disruption.
Incorporate practical simulation exercises that mirror actual cybersecurity challenges your business might face. This could include simulated phishing email tests, password strength assessments, or guided incident response scenarios. These interactive elements transform abstract concepts into tangible skills your team can immediately apply.
Pro Tip: Rotate training facilitators to bring diverse perspectives and maintain engagement. Different presenters can share unique experiences and keep the content feeling fresh and dynamic.
Ensure you create opportunities for team members to ask questions and share their own experiences. Open dialogue helps demystify complex security concepts and encourages a collaborative approach to workplace cybersecurity.
Track participation and comprehension through quick post-session assessments. These evaluations help you understand knowledge retention and identify areas where additional training might be necessary. By making your training interactive and responsive, you transform cybersecurity from a boring compliance requirement into an engaging team development opportunity.

Step 4: Test Employee Awareness and Understanding
After delivering your interactive training sessions, the next crucial phase is systematically evaluating how well your team has absorbed and can apply their new cybersecurity knowledge. This assessment will help you understand the effectiveness of your training and identify areas requiring further attention.
The Queensland Government’s user awareness training provides an excellent model through its phishing simulations that directly measure staff ability to identify and respond to potential cyber threats. Implement similar practical testing methods that go beyond traditional multiple-choice quizzes.
Design scenario-based assessments that replicate real-world cybersecurity challenges your business might encounter. These could include simulated email phishing attempts, mock social engineering scenarios, or interactive decision-making exercises that test employees’ ability to recognize and respond to potential security risks.
Recent research on adaptive cybersecurity training suggests using personalized testing approaches that dynamically adjust difficulty based on individual performance. This means creating assessments that can provide nuanced insights into each team member’s understanding and potential knowledge gaps.
Pro Tip: Make testing feel like a learning opportunity, not a punishment. Frame assessments as chances to improve and grow rather than as evaluative exercises.
Consider implementing a scoring system that provides immediate feedback. When employees encounter simulated threats, offer real-time guidance explaining why their response was correct or incorrect. This approach transforms testing from a mere measurement tool into an ongoing learning experience.
Regularly rotate and update your testing scenarios to prevent employees from memorizing responses. Surprise and variety will keep participants engaged and ensure they are developing genuine critical thinking skills rather than simply learning to pass a test.
Use the results to create personalized learning paths. Identify common knowledge gaps across your team and develop targeted refresher training modules that address these specific areas. By treating testing as a continuous improvement process, you create a dynamic and responsive cybersecurity awareness program.
Step 5: Review Outcomes and Reinforce Key Practices
Now that you have completed testing and assessment, it is time to synthesize your findings and transform insights into actionable improvements for your cybersecurity awareness program. This final step focuses on understanding your team’s performance and creating sustainable strategies for ongoing security education.
Academic research on adaptive cybersecurity training highlights the importance of dynamically adjusting learning paths based on user performance. Use your testing results to develop a nuanced understanding of your team’s strengths and potential vulnerabilities.
Business Queensland recommends incorporating cyber security into staff induction processes and scheduling regular refresher training. Conduct a comprehensive review of your testing outcomes, identifying patterns of performance across different team members and departments.
Consider using the Australian Cyber Security Centre’s Essential Eight maturity model as a benchmark for evaluating your organisation’s security practices. This framework provides a structured approach to understanding and improving your cybersecurity posture. Map your team’s performance against these standards to highlight areas requiring additional focus.
Pro Tip: Create a recognition program that celebrates employees who demonstrate exceptional security awareness. Positive reinforcement can significantly boost engagement and motivation.
Develop targeted follow-up training modules that address specific knowledge gaps revealed during your testing phase. These modules should be concise, practical, and directly linked to real-world scenarios your team might encounter.
Establish a regular review cycle where you reassess and refine your security awareness training. Cybersecurity threats evolve rapidly, so your training program must remain adaptive and responsive. Plan to review and update your materials at least twice annually, incorporating the latest threat intelligence and learning insights.
Here’s an overview of key steps in building a security awareness training program:
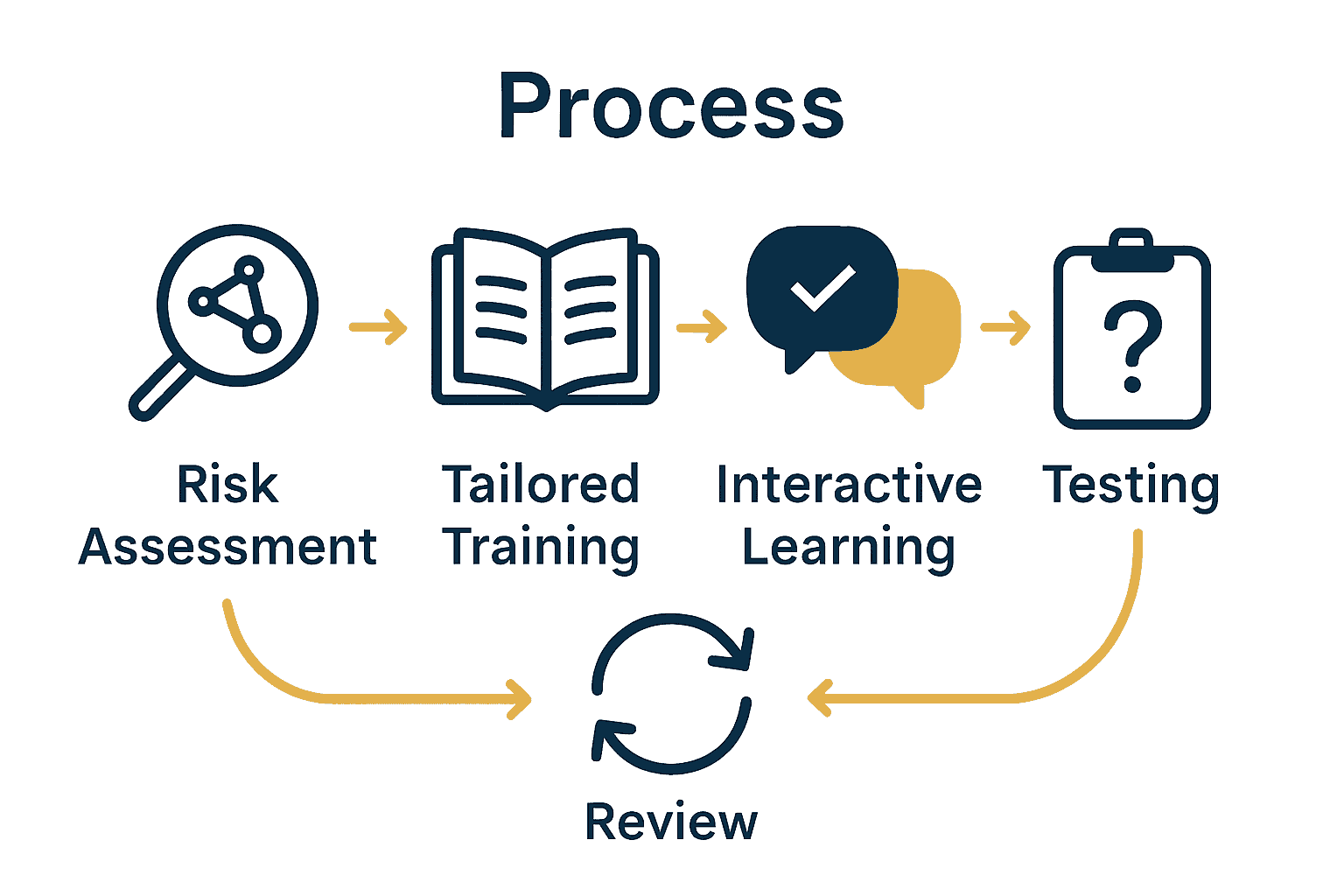
| Step | Main Objective | Key Activities |
|---|---|---|
| Assess Security Risks | Identify vulnerabilities | Map digital ecosystem Create risk inventory Prioritise threats |
| Develop User Training | Tailor training content | Segment by role Use adaptive learning Multi-format materials |
| Deliver Interactive Training | Engage team members | Short sessions Simulations Discussion & feedback |
| Test Awareness | Measure understanding | Scenario assessments Phishing simulations Adaptive quizzes |
| Review & Reinforce | Continuous improvement | Benchmark performance Targeted refreshers Regular reviews |
Remember that building a strong security culture is an ongoing journey. By continuously learning, adapting, and reinforcing best practices, you create a resilient workforce capable of protecting your business from emerging cyber threats.
Strengthen Your Business Cyber Defences with IT Start
Is your Brisbane business feeling the pressure to stay ahead of rising cyber threats? The article highlights how easy it is for local companies to fall behind on security awareness, leaving critical gaps in risk assessment, training, and real-world testing. If you are worried about overlooked vulnerabilities, outdated training materials, or compliance headaches, you are not alone. Many teams struggle to keep security knowledge practical and engaging, while threats get more sophisticated every day.
You do not have to tackle this challenge alone. IT Start is here in Brisbane to help you turn insights from your security awareness process into a concrete advantage. Our team brings deep local expertise, certified support and a proactive approach tailored for busy businesses in sectors like healthcare, finance, legal and beyond. If you want personalised solutions that reinforce best practices, fill knowledge gaps, and give your team the tools to respond, reach out for clear advice today. Take control of your cyber safety now by starting a conversation through our contact page. IT Start is ready to transform your security culture and keep your business a step ahead.
Frequently Asked Questions
What are the first steps in implementing user security awareness training for my Brisbane business?
Start by assessing your business’s specific cybersecurity risks. Map out your digital ecosystem, identify vulnerabilities, and create a corresponding training strategy tailored to address those risks within 30 days.
How can I create engaging training content for my team?
Develop tailored user training materials by segmenting content based on different roles within your organisation. Utilize various formats, such as interactive modules and real-world scenarios, to improve engagement and relevance. Aim to complete this step within 4-6 weeks.
What types of assessments should I include to test my employees’ awareness of cybersecurity?
Incorporate scenario-based assessments that mimic real cybersecurity challenges such as phishing simulations and interactive decision-making exercises. Plan to evaluate your team’s performance regularly, ideally every quarter, to identify knowledge gaps and reinforce learning.
How often should I update my security awareness training materials?
Review and update your training content at least twice a year to reflect new cybersecurity threats and technological changes. This ongoing process will help keep your training relevant and effective in adapting to evolving security challenges.
How can I measure the effectiveness of my cybersecurity training program?
Track participation and comprehension through post-session assessments and scenario-based tests. Use the results to adjust training focuses and provide targeted refreshers for areas where employees show knowledge gaps, ideally within a month after each training session.
What should I do if I find significant knowledge gaps during testing?
Develop targeted follow-up training modules to address specific areas of weakness identified in your assessments. Aim to roll out these refresher sessions within one month following your evaluation to ensure ongoing improvement in your team’s cybersecurity awareness.
Recommended
- How to Prevent Cyber Attacks: A Step-by-Step Guide – IT Start
- 7 Essential Cybersecurity Tips for Small Businesses – IT Start
- How to Improve Security: Essential Steps for Businesses – IT Start
- 7 Essential Cybersecurity Layers List for SMEs in Brisbane – IT Start
- 8 Essential Website Security Best Practices for Businesses
- 5 Ways to Secure Your Small Business and Prevent Data Breach-Bista



