Data security might sound like a techy buzzword, but it decides whether sensitive information lands in the right hands or ends up in the headlines for all the wrong reasons. Here is the kicker. Australian businesses reported over 76,000 cybercrime incidents last year alone, with losses hitting record levels. Most people think fancy firewalls and strong passwords are enough, but protecting your data takes a lot more depth, constant effort, and a bit of clever thinking to stay ahead of increasingly cunning threats.
Table of Contents
- What Are Data Security Methods And Their Importance?
- Key Concepts In Data Security: Confidentiality, Integrity, And Availability
- Types Of Data Security Methods: Physical, Technical, And Administrative
- Real-World Applications Of Data Security Methods In Businesses
- The Future Of Data Security Methods: Trends And Innovations
Quick Summary
| Takeaway | Explanation |
|---|---|
| Data security is essential for all businesses | Protecting sensitive information is crucial to maintaining operational integrity and preventing cyber threats. |
| Understand confidentiality, integrity, and availability | These three principles are core to effective data protection strategies, ensuring safe, accurate, and accessible data. |
| Implement physical, technical, and administrative strategies | A combination of these approaches provides a layered defense against unauthorized access and threats. |
| Continuously review and adapt security measures | Data security is an ongoing process requiring regular updates to keep pace with evolving cyber threats. |
| Leverage emerging technologies like AI and blockchain | Innovations can enhance security measures, streamline processes, and boost resilience against future risks. |
What are Data Security Methods and Their Importance?
Data security methods represent strategic approaches organisations use to protect sensitive digital information from unauthorised access, theft, or compromise. These comprehensive techniques form the critical defensive infrastructure for businesses navigating complex technological landscapes.
Understanding Core Data Security Principles
At its fundamental level, data security involves creating multiple protective layers around digital assets. Businesses in Brisbane and across Queensland recognise that these methods are not optional luxuries but essential operational requirements. The primary objective is establishing robust mechanisms that safeguard critical information from potential cyber threats.
Three core principles define effective data security methods:
- Confidentiality: Ensuring only authorised personnel can access specific information
- Integrity: Maintaining data accuracy and preventing unauthorised modifications
- Availability: Guaranteeing authorised users can access necessary information when required
The Business Impact of Robust Data Protection
Companies implementing comprehensive data security methods gain significant strategic advantages. According to the Australian Cyber Security Centre, businesses face increasingly sophisticated cyber threats that can potentially cause substantial financial and reputational damage.
Understanding data security methods becomes crucial because modern organisations handle vast quantities of sensitive information. From customer details to financial records, every digital asset requires protection. Learn more about our data security solutions to comprehend how tailored approaches can mitigate organisational risks.
Businesses must recognise that data security is not a one-time implementation but an ongoing process requiring continuous assessment, updating, and refinement of protective strategies. The dynamic nature of cyber threats demands proactive and adaptive security approaches that evolve alongside technological advancements.
Key Concepts in Data Security: Confidentiality, Integrity, and Availability
Data security fundamentally revolves around three critical pillars: confidentiality, integrity, and availability. These interconnected principles form the foundation of comprehensive cybersecurity strategies for businesses across Queensland and beyond.
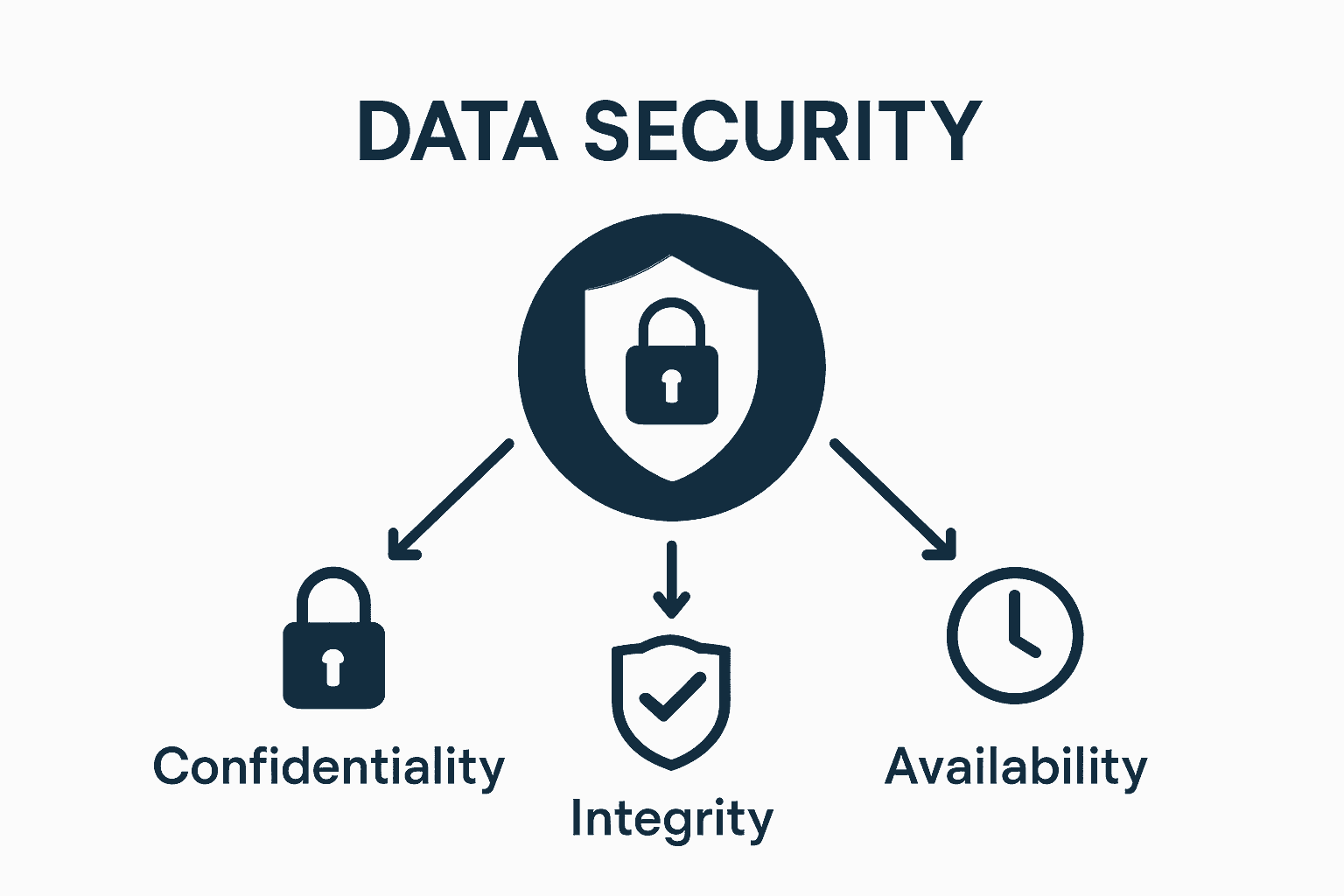
Understanding Confidentiality: Protecting Sensitive Information
Confidentiality ensures that sensitive data remains accessible only to authorised individuals or systems. This principle acts as a digital fortress, preventing unauthorised access and potential misuse of critical information. In practical terms, confidentiality involves implementing robust access controls, encryption technologies, and strict authentication protocols.
Key strategies for maintaining confidentiality include:
- Data Encryption: Converting sensitive information into unreadable code
- Access Management: Implementing role-based permissions
- Multi Factor Authentication: Requiring multiple verification steps
Integrity: Preserving Data Accuracy and Reliability
Data integrity focuses on maintaining the accuracy, consistency, and trustworthiness of information throughout its lifecycle. According to the Australian Signals Directorate, protecting data from unauthorized modifications is crucial for organisational security. This means ensuring that data remains unaltered and can be verified as original and authentic.
Technical mechanisms like checksums, digital signatures, and version control systems help organisations detect and prevent unauthorized data modifications. Learn more about our data protection approaches to understand comprehensive integrity management.
Availability: Ensuring Continuous Access to Critical Information
Availability guarantees that authorized users can access necessary data and systems when required. This principle prevents disruptions that could potentially cripple business operations. Modern businesses require reliable infrastructure that maintains seamless access while protecting against potential service interruptions.
Effective availability strategies involve:
- Redundant Systems: Creating backup infrastructure
- Disaster Recovery Planning: Developing comprehensive response protocols
- Regular System Maintenance: Proactively managing technological resources
Businesses in Brisbane must recognize that these three principles are interconnected. A weakness in one area can compromise the entire data security framework, highlighting the importance of a holistic approach to information protection.
The following table outlines the core principles of data security—confidentiality, integrity, and availability—alongside their main objectives and typical strategies.
| Principle | Objective | Typical Strategies/Mechanisms |
|---|---|---|
| Confidentiality | Restrict access to authorised users | Data encryption, access management, multi-factor authentication |
| Integrity | Ensure data accuracy and reliability | Checksums, digital signatures, version control |
| Availability | Maintain accessibility for authorised users | Redundant systems, disaster recovery, system maintenance |
Types of Data Security Methods: Physical, Technical, and Administrative
Data security encompasses three fundamental approaches: physical, technical, and administrative methods. These interconnected strategies form a comprehensive framework for protecting organisational information assets across diverse technological environments.
Physical Security: Protecting Tangible Information Infrastructure
Physical security methods focus on safeguarding physical hardware, infrastructure, and access points that store or transmit sensitive data. For Brisbane businesses, this involves creating controlled environments that prevent unauthorized physical access to critical technological resources.
Key physical security strategies include:
- Secure Data Centres: Implementing restricted access zones
- Hardware Protection: Using locks, surveillance, and environmental controls
- Device Management: Tracking and securing portable technological equipment
Technical Security: Digital Protection Mechanisms
Technical security represents the digital layer of data protection, utilizing advanced technological tools to secure information systems. According to the Australian Signals Directorate, organisations must deploy sophisticated digital defence mechanisms to counter evolving cyber threats.
Critical technical security approaches involve:

- Network Encryption: Protecting data transmission channels
- Firewall Implementation: Creating digital barriers against unauthorized access
- Intrusion Detection Systems: Monitoring and responding to potential security breaches
Administrative Security: Governance and Human Factors
Administrative security methods address the human and procedural aspects of data protection. Learn more about access control strategies to understand how organisational policies complement technological defences.
Essential administrative security components include:
- Security Policies: Establishing clear organisational guidelines
- Employee Training: Educating staff about cybersecurity best practices
- Risk Management: Continuously assessing and mitigating potential security vulnerabilities
Businesses in Queensland must recognize that effective data security requires a holistic approach.
To help clarify the differences and roles each type of data security method plays, the table below compares physical, technical, and administrative security based on their focus and key strategies.
| Security Method | Focus Area | Key Strategies/Examples |
|---|---|---|
| Physical Security | Tangible infrastructure | Secure data centres, hardware protection, device management |
| Technical Security | Digital protection mechanisms | Network encryption, firewalls, intrusion detection systems |
| Administrative Security | Human factors, governance | Security policies, employee training, risk management |
Real-World Applications of Data Security Methods in Businesses
Data security methods transition from theoretical concepts to critical operational strategies when implemented across diverse business environments. Understanding practical applications helps organisations develop robust protection frameworks tailored to their specific technological landscapes.
Financial Sector: Protecting Sensitive Transaction Data
Financial institutions require exceptional data security due to the highly sensitive nature of monetary transactions. Banks and financial services in Brisbane must implement comprehensive security protocols that safeguard customer financial information against sophisticated cyber threats.
Key implementation strategies include:
- Encryption of Transaction Records: Securing all financial data transfers
- Multi Layer Authentication: Verifying user identities through multiple checkpoints
- Real Time Fraud Detection: Monitoring transactions for suspicious activities
Healthcare: Maintaining Patient Confidentiality
Healthcare organisations handle extremely sensitive personal and medical information, necessitating rigorous data protection approaches. According to the Office of the Australian Information Commissioner, medical institutions must ensure comprehensive protection of patient data across digital platforms.
Learn more about cybersecurity threats facing small businesses to understand the complex landscape of digital risks across different industry sectors.
Professional Services: Managing Confidential Client Information
Legal firms, consulting agencies, and professional service providers manage extensive confidential client documentation. These organisations require nuanced data security methods that protect intellectual property and maintain client trust.
Essential protective measures involve:
- Secure Document Management Systems: Controlling access to sensitive files
- Communication Encryption: Protecting client correspondence
- Access Logging: Tracking and recording all information interactions
Businesses across Queensland must recognize that data security is not a universal solution but a customised approach requiring continuous adaptation. Each industry presents unique challenges demanding specific security methodologies aligned with regulatory requirements and technological infrastructure.
The Future of Data Security Methods: Trends and Innovations
The landscape of data security continues to evolve rapidly, driven by technological advancements and increasingly sophisticated cyber threats. Businesses must anticipate and adapt to emerging trends that reshape how organisations protect their digital assets and maintain operational resilience.
Artificial Intelligence and Machine Learning in Security
Artificial intelligence represents a transformative force in data security methodologies. AI driven systems can analyse massive datasets, identify complex patterns, and predict potential security vulnerabilities with unprecedented speed and accuracy. For Brisbane businesses, this means developing more proactive and intelligent defence mechanisms.
Key AI security innovations include:
- Predictive Threat Detection: Identifying potential security risks before they emerge
- Automated Response Mechanisms: Instantly mitigating identified cyber threats
- Intelligent Access Management: Dynamic user authentication based on behavioural analysis
Quantum Computing and Enhanced Encryption
Quantum computing promises revolutionary approaches to data protection. According to the Australian Signals Directorate, organisations must prepare for quantum technologies that can both enhance and potentially compromise existing encryption strategies.
Learn more about emerging cybersecurity technologies to understand the complex future of digital protection mechanisms.
Decentralised Security Architectures
Traditional centralised security models are giving way to more distributed and resilient approaches. Blockchain and zero trust architectures are emerging as powerful frameworks that fundamentally reimagine how organisations secure their digital environments.
Emerging decentralised security strategies involve:
- Zero Trust Networks: Continuously verifying every access request
- Blockchain Based Authentication: Creating immutable security logs
- Distributed Identity Management: Empowering individual data control
Businesses across Queensland must remain agile, recognising that data security is an ongoing journey of adaptation and innovation. The future demands not just technological solutions, but strategic thinking that anticipates and neutralises emerging digital risks.
Secure Your Business Future with Proactive Data Security Solutions
You have just explored how vital data security methods are to protect your business in today’s rapidly changing digital landscape. If you are feeling the pressure of complex cyber threats or the need to keep sensitive information safe, you are not alone. Many Brisbane businesses share concerns about unauthorised access, data breaches, and managing confidentiality, integrity, and availability of their most valuable assets. Achieving compliant and resilient protection can feel overwhelming, especially with evolving technology and regulatory demands.
This is where IT Start becomes your strategic partner. We specialise in tailored data security solutions for businesses across Queensland, building multi-layer defences with proactive managed IT support and local expertise. Take control of your data security now with our transparent, industry-proven process. Receive a free assessment or consultation and discover how your organisation can achieve stronger compliance and business continuity. Do not wait until a security incident disrupts your operations. Contact IT Start today to safeguard your future and gain the confidence that your business deserves.
Frequently Asked Questions
What are the core principles of data security methods?
The core principles of data security methods are confidentiality, integrity, and availability. These principles work together to ensure that sensitive information is protected from unauthorized access, remains accurate and reliable, and is accessible to authorized users when needed.
How can businesses ensure the confidentiality of their data?
Businesses can ensure the confidentiality of their data by implementing measures such as data encryption, access management with role-based permissions, and multi-factor authentication. These strategies help prevent unauthorized access to sensitive information.
What are the key types of data security methods?
The key types of data security methods include physical security, which focuses on protecting tangible infrastructure; technical security, which utilises digital tools; and administrative security, which addresses human factors and governance through policies and employee training.
Why is it important for businesses to implement robust data security methods?
Implementing robust data security methods is crucial for businesses as it protects sensitive digital information from cyber threats, safeguarding the organization’s reputation and financial stability while ensuring compliance with legal and regulatory requirements.



