Cyber attacks are hitting Australian businesses harder than ever and the fallout is more than just a tech headache. Small to medium businesses now face potential losses over $276,000 each time a major breach happens. Most people reckon these incidents are rare or only target big companies. That could not be further from the truth for locals in Brisbane and across Queensland as the real danger is thinking it will never happen to you.
Table of Contents
- What Is A Cyber Security Response Plan?
- Why Is A Cyber Security Response Plan Important?
- Key Components Of An Effective Cyber Security Response Plan
- How A Cyber Security Response Plan Works In Real-World Scenarios
- Practical Applications Of A Cyber Security Response Plan For SMEs
Quick Summary
| Takeaway | Explanation |
|---|---|
| Develop a structured response plan | A clear cybersecurity response plan prepares your organisation to handle digital threats systematically and efficiently. |
| Assign specific roles for response teams | Clearly defined responsibilities ensure team members know their functions during security incidents, enhancing effectiveness. |
| Implement advanced threat detection mechanisms | Incorporating automated monitoring and regular assessments helps identify potential breaches rapidly, allowing for swift action. |
| Conduct regular training for your team | Ongoing training ensures your response team remains prepared and adaptable to evolving cyber threats through simulation exercises. |
| Prioritise risk assessments for SMEs | For small and medium enterprises, identifying critical assets and vulnerabilities aids in developing tailored, cost-effective cybersecurity strategies. |
What is a Cyber Security Response Plan?
A cyber security response plan represents a strategic blueprint that guides organisations through managing and mitigating potential digital security incidents. Unlike reactive approaches, this comprehensive framework provides businesses with a structured methodology for addressing cyber threats proactively and systematically.
Defining the Core Components
At its fundamental level, a cyber security response plan outlines precise protocols for detecting, containing, and resolving security breaches. According to the Australian Signals Directorate, an effective plan encompasses multiple critical elements that work cohesively to protect organisational digital infrastructure.
The primary objectives of a cyber security response plan include:
- Establishing clear communication channels during security incidents
- Defining specific roles and responsibilities for response team members
- Creating predefined procedures for threat identification and neutralisation
- Minimising potential damage and operational disruption
The table below provides a concise overview of the core components found in an effective cyber security response plan, helping businesses distinguish their roles and importance at a glance.
| Component | Purpose | Key Activities |
|---|---|---|
| Communication Channels | Facilitate clear information flow during incidents | Notify stakeholders, coordinate internal teams |
| Defined Roles & Responsibilities | Ensure accountability and efficient response | Assign team leads, technical specialists, legal |
| Threat Detection & Neutralisation | Identify and address security incidents quickly | Monitor systems, automate alerts, contain threats |
| Predefined Procedures | Provide step-by-step guidance to streamline response | Stepwise response protocols, escalation paths |
| Damage & Disruption Minimisation | Limit negative outcomes for business and customers | Isolate systems, restore data, manage reputation |
Understanding Strategic Importance
Businesses operating in Brisbane and across Queensland face increasingly sophisticated cyber threats. A well-crafted cyber security response plan serves as a crucial defensive mechanism, enabling organisations to respond swiftly and effectively when digital vulnerabilities are exploited.
While many businesses perceive such plans as optional, they are now considered essential risk management tools. Cybersecurity experts from the Queensland Government recommend that organisations develop comprehensive response strategies that account for various potential scenarios, from minor system breaches to significant data compromise events.
Key considerations when developing a cyber security response plan include understanding your organisation’s unique digital ecosystem, identifying potential vulnerabilities, and creating adaptable protocols that can address emerging threat landscapes. The goal is not just technical protection but also maintaining business continuity and protecting stakeholder trust during potentially challenging security incidents.
Why is a Cyber Security Response Plan Important?
Cyber security response plans transcend mere technical documentation, representing a critical strategic safeguard for modern businesses confronting increasingly complex digital threats. These comprehensive frameworks are not optional luxuries but essential protective mechanisms that determine an organisation’s resilience and survival in a volatile technological landscape.
Financial and Reputational Protection
Breach incidents can inflict devastating financial consequences on businesses. According to Australian Cyber Security Centre, small to medium enterprises can face potential losses exceeding $276,000 per significant security incident. These expenses encompass direct recovery costs, potential legal liabilities, and substantial reputational damage.
Significant financial risks include:
- Immediate incident response and system restoration expenses
- Potential regulatory fines and compliance penalties
- Lost business during operational disruptions
- Customer compensation and trust reconstruction efforts
This table summarises the primary financial and reputational risks businesses face following a cyber attack, offering a quick reference on the varied impacts mentioned in the article.
| Risk Type | Description |
|---|---|
| Incident Response Costs | Direct expenses for resolving the breach and restoring systems |
| Regulatory Penalties | Fines and penalties related to compliance failures |
| Operational Losses | Revenue loss due to downtime or business interruption |
| Customer Compensation | Costs incurred to regain trust and compensate affected customers |
| Reputational Damage | Negative impact on brand and trust in the eyes of clients and partners |
Operational Continuity and Strategic Resilience
A robust cyber security response plan ensures businesses can maintain operational momentum even during challenging digital security scenarios. Read our guide on data security best practices to understand how strategic preparedness minimises potential disruptions.
Businesses without comprehensive response strategies risk extended operational paralysis, potentially compromising competitive positioning and stakeholder confidence. The ability to detect, contain, and rapidly recover from security incidents distinguishes organisations that survive digital threats from those that succumb to them.
Moreover, a well-structured response plan demonstrates professional maturity to clients, investors, and regulatory bodies. It signals a proactive approach to risk management, showcasing the organisation’s commitment to technological governance and stakeholder protection. In an era where digital trust is paramount, a comprehensive cyber security response plan becomes a powerful differentiator in competitive business environments.
Key Components of an Effective Cyber Security Response Plan
Developing a robust cyber security response plan requires strategic integration of multiple critical elements that work synergistically to protect an organisation’s digital infrastructure. These components must be carefully designed to address potential threats comprehensively and enable rapid, coordinated responses.
Incident Identification and Assessment
The initial phase of an effective response plan centres on creating sophisticated mechanisms for threat detection and preliminary evaluation. According to Australian Signals Directorate cybersecurity guidelines, organisations must establish clear protocols for recognising potential security breaches across various digital platforms.
Critical elements for incident identification include:
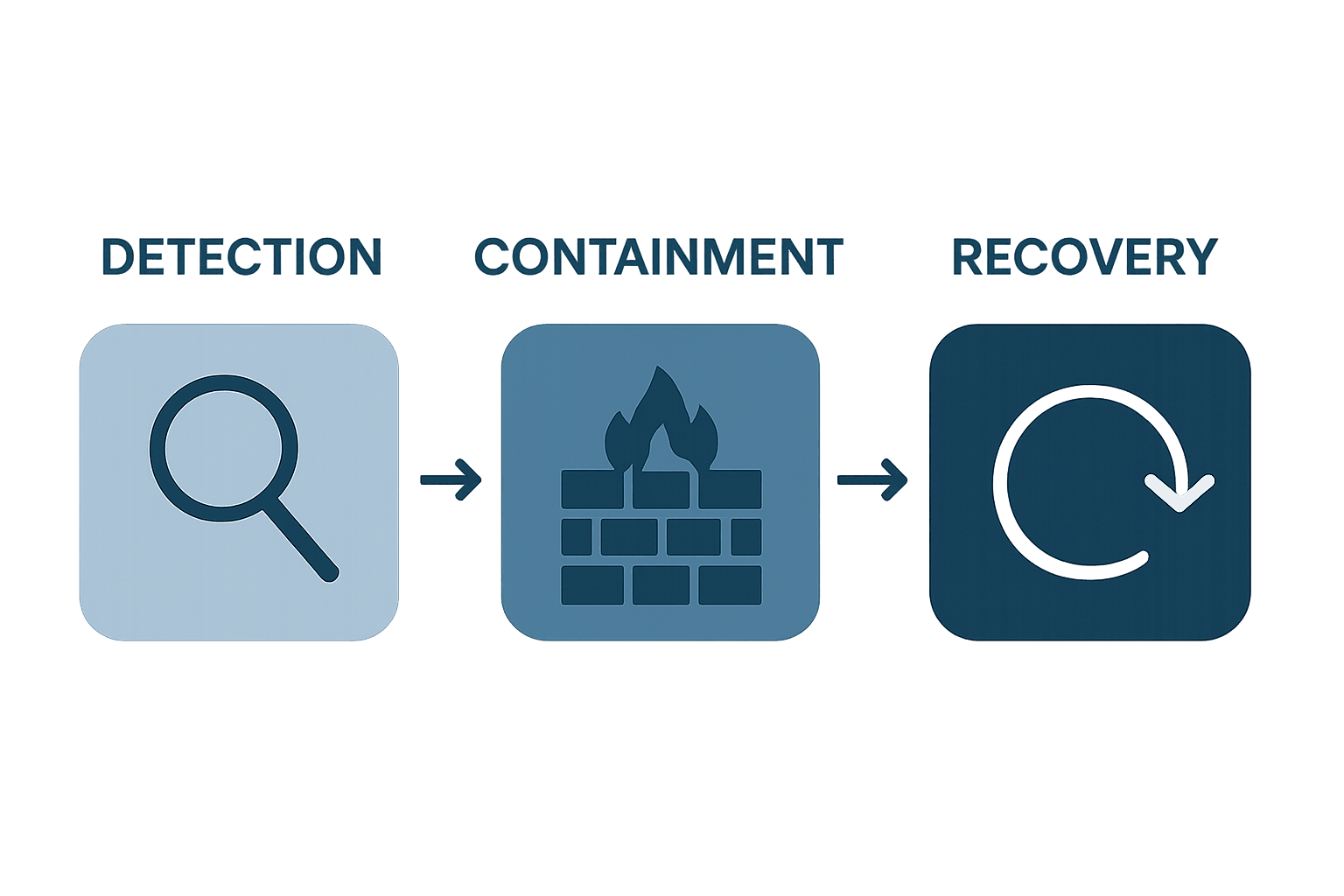
- Advanced monitoring systems tracking network traffic anomalies
- Automated threat detection mechanisms
- Regular vulnerability assessments
- Comprehensive logging of digital interactions
Response Team Structure and Responsibilities
A well-defined response team represents the backbone of any cyber security strategy. Learn more about improving business security practices to understand the importance of structured incident management.
Organisations must carefully delineate roles and responsibilities, ensuring each team member understands their specific function during a potential security event. This includes designating clear leadership, technical specialists, communication coordinators, and legal representatives who can collaborate seamlessly during high-pressure scenarios.
The response team should possess a comprehensive understanding of the organisation’s technological ecosystem, enabling them to make swift, informed decisions that minimise potential damage and accelerate recovery processes.
Regular training and simulation exercises are crucial for maintaining the team’s readiness and adaptability in confronting evolving cyber threats.
How a Cyber Security Response Plan Works in Real-World Scenarios
Cyber security response plans transform theoretical strategies into practical, actionable protocols that guide organisations through complex digital threat landscapes. These frameworks are not static documents but dynamic mechanisms designed to adapt and respond to evolving security challenges in real-time.
Detection and Initial Assessment
The initial phase of a cyber security response involves rapid threat identification and comprehensive evaluation. Australian Cyber Security Centre emphasises the critical importance of swift, systematic incident recognition and classification.
Key detection mechanisms typically include:
- Automated monitoring systems that track network anomalies
- Intrusion detection software scanning for suspicious activities
- Continuous log analysis identifying potential security breaches
- Machine learning algorithms recognising unusual digital behavioural patterns
Containment and Mitigation Strategies
Once a potential security incident is identified, response teams must implement immediate containment protocols to prevent further potential damage. Learn more about cybersecurity threats facing small businesses to understand the complexity of modern digital risks.
Containment strategies often involve isolating affected systems, temporarily disabling network access points, and implementing emergency security protocols. These actions are designed to limit the potential spread of digital threats and prevent additional compromise of organisational infrastructure.
Effective response plans also incorporate comprehensive documentation processes, ensuring every action is meticulously recorded for later forensic analysis and potential legal requirements. By maintaining detailed incident logs, organisations can improve future response capabilities and demonstrate professional accountability during challenging security scenarios.
Practical Applications of a Cyber Security Response Plan for SMEs
Small and medium enterprises (SMEs) face unique cybersecurity challenges that demand tailored, pragmatic response strategies. Unlike large corporations with extensive resources, SMEs must develop nimble, cost-effective approaches that maximise protection while maintaining operational efficiency.
Risk Assessment and Prioritisation
Effective cyber security response plans for SMEs begin with comprehensive risk assessments that identify the most critical digital assets and potential vulnerabilities. According to Australian Cyber Security Centre, businesses must systematically evaluate their technological ecosystem and prioritise protective measures.
Key risk assessment considerations include:
- Identifying mission-critical digital infrastructure
- Evaluating potential financial and operational impact of potential breaches
- Mapping interconnected digital systems and potential vulnerability points
- Understanding industry-specific regulatory compliance requirements
Resource-Efficient Implementation Strategies
Understand more about cybersecurity fundamentals to develop a strategic approach that matches your business capabilities. SMEs can implement cost-effective response strategies by leveraging scalable technologies, developing clear communication protocols, and creating adaptable incident management frameworks.
Practical implementation often involves selecting modular security solutions that can grow alongside the business, investing in staff training, and establishing partnerships with specialised cybersecurity providers. The goal is creating a flexible response mechanism that provides robust protection without overwhelming limited organisational resources.
By developing targeted, proportionate cyber security response plans, SMEs can transform potential vulnerabilities into strategic advantages, demonstrating professional resilience and building stakeholder confidence in an increasingly complex digital landscape.

Is Your Business Ready to Act When a Cyber Threat Strikes?
Building a strong cyber security response plan is not just for big corporations. As covered in the article, Brisbane businesses are now more vulnerable than ever to digital attacks that can stop operations, cause serious financial loss and damage reputations. Many small and medium enterprises find themselves unprepared to identify threats early and respond quickly. Without a local partner skilled in business-first, tailored solutions, even the best internal teams risk missing vital steps in detection, containment and recovery. Delaying a proper response plan can leave your systems exposed and your customers’ trust at risk.
Now is the time to protect your business and meet compliance needs with a proactive approach. Want a response plan designed for your unique risks? Reach out today for a free assessment. Improve your ability to detect breaches, recover faster and show your clients you take security seriously. Visit https://itstart.com.au/contact-us to connect with IT Start – Brisbane’s trusted IT partner, focused on managed security, local expertise and real business results. Secure your future now so you are never caught off guard.
Frequently Asked Questions
What is a Cyber Security Response Plan?
A Cyber Security Response Plan is a strategic framework that helps organisations manage and mitigate potential digital security incidents proactively and systematically. It outlines protocols for detecting, containing, and resolving security breaches.
Why is a Cyber Security Response Plan important for businesses?
A Cyber Security Response Plan is essential for protecting businesses from financial losses, reputational damage, and operational disruptions caused by cyber incidents. It enables companies to respond swiftly to threats and maintain business continuity.
What are the key components of an effective Cyber Security Response Plan?
Key components include incident identification and assessment protocols, a well-defined response team structure, clear roles and responsibilities, and strategies for containment and mitigation of potential threats.
How can small and medium enterprises (SMEs) develop a Cyber Security Response Plan?
SMEs can develop a Cyber Security Response Plan by conducting comprehensive risk assessments, identifying critical digital assets, prioritising vulnerabilities, and adopting resource-efficient strategies to implement protective measures.
Recommended
- What is Cybersecurity? Understanding Its Importance and Function – IT Start
- 7 Top SMB Cybersecurity Threats Every Business Should Know – IT Start
- What to Know About Cyber Security: Understanding Its Importance – IT Start
- How to Improve Security: Essential Steps for Businesses – IT Start
- Cybersecurity for Insurers, tools and best practices – Digital Insurance Platform | IBSuite Insurance Software | Modern Insurance System
- 9 Tips to Secure Your Business in 2023 – Voipcom



