Over 60 percent of Australian small businesses have faced a cyber incident in the past year, putting critical data and reputation on the line. With attacks on the rise, understanding how to conduct a step-by-step IT security assessment can mean the difference between safety and costly setbacks. This guide breaks the process into clear stages, giving Brisbane businesses a practical way to protect assets and minimise risk without drowning in jargon or technical confusion.
Table of Contents
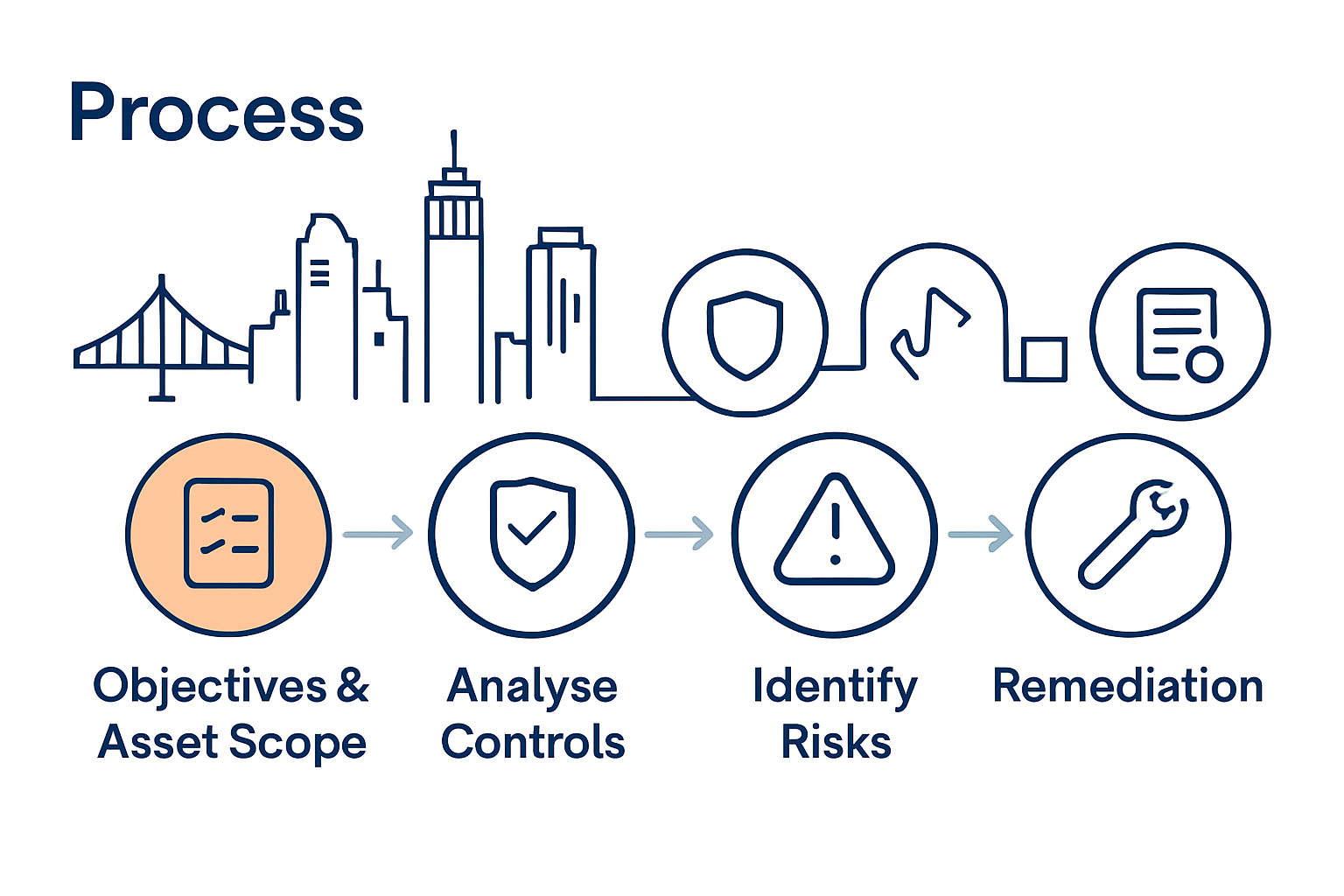
- Stage 1: Define Assessment Objectives And Asset Scope
- Stage 2: Gather And Analyse Existing Security Controls
- Stage 3: Identify Vulnerabilities And Assess Risks
- Stage 4: Implement Targeted Remediation Actions
- Stage 5: Verify Improvements And Document Outcomes
Quick Summary
| Key Point | Explanation |
|---|---|
| 1. Define clear assessment goals | Outline what systems to protect and evaluate to focus your resources effectively during the security assessment. |
| 2. Create a comprehensive asset inventory | List all hardware, software, and digital resources to identify critical assets needing protection, prioritising those handling sensitive data. |
| 3. Assess existing security measures | Review your current physical and digital security controls to identify gaps and ensure adequate protection for critical systems. |
| 4. Identify vulnerabilities and risks | Analyse potential threats, evaluating their likelihood and impact to understand the security landscape related to your business operations. |
| 5. Document and verify security improvements | Validate the effectiveness of remediation actions through testing and create detailed records for ongoing cybersecurity management and compliance. |
Stage 1: Define assessment objectives and asset scope
When launching an IT security assessment for your Brisbane small business, the first critical step involves precisely mapping out what you want to evaluate and protect. Defining the scope sets clear boundaries for your entire security investigation, ensuring you focus resources strategically and avoid wasting time on irrelevant areas.
To create an effective assessment scope, start by conducting a comprehensive asset inventory that categorises all your business technology systems. This means listing every hardware device, software application, network connection, and digital resource your organisation relies on. Break down each asset by its function and criticality level important for your business operations. Pay special attention to systems handling sensitive information like customer data, financial records, or operational workflows.
A pro tip for Brisbane SMEs: don’t try to boil the ocean. Select a manageable subset of your technology ecosystem for your initial assessment. Start with your most critical systems and gradually expand your review. This approach allows you to build a methodical security assessment strategy without overwhelming your team or budget.
With your objectives and asset scope clearly defined, you are now ready to move into the next stage of identifying potential vulnerabilities across your selected systems.
Stage 2: Gather and analyse existing security controls
In this crucial stage of your IT security assessment, you’ll systematically evaluate your current security infrastructure to understand existing protection mechanisms and potential vulnerabilities. Comprehensive security assessments require a meticulous review of both physical and digital security controls, covering everything from access management to system configurations.
Begin by creating a detailed inventory of your current security mechanisms. This includes mapping out physical security elements like CCTV systems, access control points, and network perimeters. For digital infrastructure, document your existing firewalls, antivirus software, user authentication protocols, and data encryption methods. Pay special attention to how these controls interact and identify any potential gaps or overlapping protections.

A practical tip for Brisbane SMEs: recognise that security assessments can be complex and resource intensive for smaller organisations. Don’t aim for perfection in your first review. Instead, focus on understanding your most critical systems and their current protection levels. Prioritise systems handling sensitive customer data, financial information, and core business operations.
With your security controls thoroughly documented and analysed, you are now prepared to move into the next phase of identifying specific vulnerabilities across your technology ecosystem.
Stage 3: Identify vulnerabilities and assess risks
This critical stage involves systematically uncovering potential security weaknesses across your business technology infrastructure. You will investigate and categorise potential threats that could compromise your organisation’s digital ecosystem, focusing on understanding both the likelihood and potential impact of various security risks.
Identifying potential threats requires a comprehensive approach that considers multiple threat categories. These include external threats like cybercriminals planning ransomware attacks, data theft attempts, and financial fraud schemes, as well as more sophisticated risks from hacktivists and potentially nation-state actors conducting advanced persistent threats. Evaluate each identified vulnerability by assessing its potential damage, likelihood of occurrence, and the specific systems or data at risk.
A strategic tip for Brisbane businesses: recognise that operational security and compliance challenges often outweigh technical complexities. Focus not just on technical vulnerabilities, but also on how your existing processes and human factors might create security gaps. Consider aspects like employee training, access management protocols, and data handling procedures when assessing your overall risk landscape.
With a clear understanding of your vulnerabilities and associated risks, you are now prepared to develop a targeted strategy for addressing and mitigating these potential security challenges.
Stage 4: Implement targeted remediation actions
With your vulnerabilities identified, you are now ready to develop and execute a strategic plan to address and mitigate the security risks discovered during your assessment. This stage transforms your insights into concrete, actionable improvements that will strengthen your organisation’s cybersecurity posture.
The Essential 8 framework provides an excellent roadmap for prioritising cybersecurity efforts, emphasising a defence in depth approach. This methodology recognises that no single security measure can provide complete protection, but a comprehensive set of strategies can significantly reduce your risk of cyber incidents. Prioritise your remediation actions by addressing the most critical vulnerabilities first, focusing on potential entry points and systemic weaknesses that could compromise your digital infrastructure.
A forward thinking strategy for Brisbane SMEs involves exploring transformative technologies like Artificial Intelligence and Machine Learning to enhance your cybersecurity policies. While these technologies are still emerging for smaller organisations, they offer promising capabilities for more intelligent and adaptive security approaches. Start by implementing fundamental improvements, and gradually integrate more advanced technological solutions as your security maturity evolves.
With targeted remediation actions underway, you are now positioned to develop a continuous monitoring and improvement strategy that will help protect your business from evolving cyber threats.
Stage 5: Verify improvements and document outcomes
The final stage of your IT security assessment focuses on validating the effectiveness of your implemented remediation actions and creating a comprehensive record of your cybersecurity journey. This critical phase ensures that your security improvements are not only implemented but also thoroughly tested and documented.
Begin by conducting rigorous testing of your newly implemented security controls. Run comprehensive vulnerability scans, perform penetration testing, and simulate potential attack scenarios to confirm that your remediation efforts have genuinely strengthened your organisation’s defences. Compare the results against your initial assessment to quantify the improvements and identify any remaining areas that might require further attention.
Small businesses are increasingly attractive targets for cybercriminals, making it crucial to develop a systematic approach to documenting your security improvements. Create a detailed report that outlines the vulnerabilities discovered, specific remediation actions taken, testing methodologies used, and measurable outcomes achieved. This documentation serves multiple purposes: it provides a clear audit trail, helps track your security maturity over time, and can be valuable for demonstrating your commitment to cybersecurity to stakeholders, clients, and potential investors.
With your improvements verified and outcomes documented, you have established a robust foundation for ongoing cybersecurity management and continuous improvement.
Strengthen Your Brisbane SME with Expert IT Security Support
If you have identified the crucial need to protect your business assets and manage cybersecurity risks as outlined in the article Essential IT Security Assessment Steps for Brisbane SMEs you understand how challenging assessing and addressing vulnerabilities can be. From defining clear scopes to implementing targeted remediation actions every stage requires expertise and a strategic approach that many small to medium businesses find difficult to manage alone. Key pain points like resource limitations complexity of security controls and the urgency to defend sensitive customer and financial data highlight the importance of partnering with a knowledgeable local provider.
At IT Start we specialise in helping Brisbane-based SMEs like yours navigate these security challenges with confidence. Our managed IT support and cybersecurity services are designed to handle the entire assessment and remediation journey so you can focus on growing your business. By leveraging our proactive support and industry-approved methodologies we ensure your business systems remain resilient against evolving threats. Act now to protect your operations enhance compliance and reduce risk by booking a free consultation with our security experts. Don’t wait until a breach disrupts your business contact IT Start today to start your tailored IT security assessment and safeguard your future.
Frequently Asked Questions
What are the first steps in an IT security assessment for small businesses?
To begin an IT security assessment, define your assessment objectives and asset scope. Create an inventory of all business technology systems and prioritize your most critical assets.
How can I identify vulnerabilities in my business technology?
You can identify vulnerabilities by systematically investigating potential security weaknesses in your infrastructure. Focus on evaluating the likelihood and impact of different threats, such as cyberattacks or data breaches.
What types of security controls should I review during my assessment?
In your assessment, review both physical and digital security controls, including firewalls, access management systems, and antivirus software. Create an inventory that documents how these controls interact and identify any gaps.
How do I prioritise remediation actions after identifying vulnerabilities?
Prioritise remediation actions by addressing the critical vulnerabilities first, focusing on entry points and systemic weaknesses. For example, tackle vulnerabilities that could lead to the loss of sensitive customer data.
How can I verify that my security improvements are effective?
To verify your security improvements, conduct testing such as vulnerability scans and penetration tests. Document the outcomes and compare them to your initial assessment results to ensure your improvements have made a measurable impact.
Why is documentation important in the IT security assessment process?
Documentation is crucial as it provides an audit trail of the vulnerabilities discovered and remediation actions taken. This clear record can help track your security progress and communicate your commitment to cybersecurity to stakeholders.



