Information security sits at the heart of how businesses protect everything from customer data to company secrets. Most people focus on hackers breaking through flashy firewalls or cracking passwords. But here is the shocker. Australian small to medium businesses lose millions every year to digital attacks, often because of simple staff mistakes or forgotten updates. Those digital threats are not just a tech department problem. They can cripple your business in ways you would not expect and sometimes the weakest link is not your software but your team at morning tea.
Table of Contents
- What Is Information Security? A Simple Definition
- Why Is Information Security Essential For Businesses?
- How Information Security Works: Key Principles And Practices
- Understanding Threats: Common Vulnerabilities And Risks
- Real-World Applications Of Information Security In Business
Quick Summary
| Takeaway | Explanation |
|---|---|
| Implement multiple layers of security | Utilize technological, procedural, and human strategies for comprehensive protection against cyber threats. |
| Train staff on security best practices | Regular training fosters a culture of awareness, helping prevent breaches caused by human error. |
| Compliance with data regulations is crucial | Adhering to legal requirements protects organizations from penalties and enhances reputation. |
| Conduct regular security audits | Frequent assessments help identify vulnerabilities and enhance the organization’s defensive measures. |
| Develop an incident response plan | A clear strategy for responding to security breaches ensures minimal disruption and quick recovery. |
What is Information Security? A Simple Definition
Information security represents a comprehensive approach to protecting digital and physical data from unauthorised access, theft, disruption, and potential misuse. At its core, information security aims to safeguard an organisation’s critical information assets by implementing strategic protective measures that ensure confidentiality, integrity, and availability of data.
Understanding the Fundamental Concept
Think of information security like a sophisticated digital fortress protecting your most valuable business resources. It goes beyond simple password protection or basic firewall configurations. Information security encompasses a holistic strategy that involves multiple layers of technological, procedural, and human interventions designed to shield sensitive information from potential cyber threats.
According to the Australian Signals Directorate, information security involves systematically managing risks to protect information throughout its entire lifecycle. This means considering protection mechanisms from the moment data is created through its storage, transmission, and eventual disposal.
Key Components of Information Security
Information security operates through several critical dimensions that work collaboratively to create robust protection:
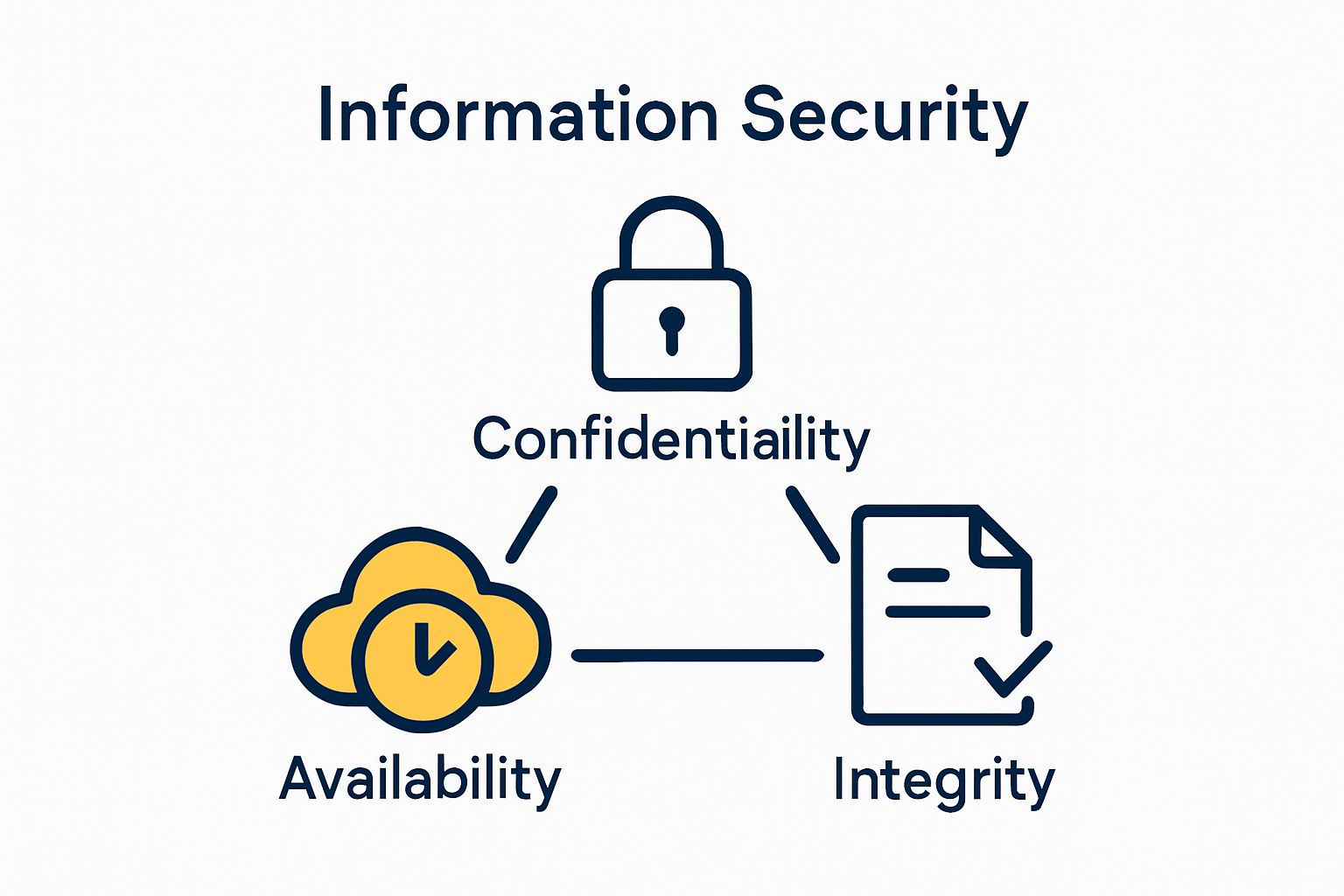
- Confidentiality: Ensuring only authorised personnel can access specific information
- Integrity: Maintaining the accuracy and completeness of data
- Availability: Guaranteeing that information remains accessible to authorised users when required
Practically speaking, this translates to implementing comprehensive security protocols that might include encryption technologies, access control systems, network monitoring tools, and comprehensive staff training programs.
For Brisbane businesses, understanding these fundamental principles is crucial in developing a proactive approach to cybersecurity that protects against evolving digital risks.
The ultimate goal of information security is not just preventing breaches but creating a resilient digital environment where data remains protected, trustworthy, and strategically manageable.
Below is a summary table comparing the three key principles of information security, providing a clear definition and practical example for each.
| Principle | Definition | Practical Example |
|---|---|---|
| Confidentiality | Ensuring that only authorised personnel can access specific information | Limiting patient data access to doctors and authorised staff in healthcare |
| Integrity | Maintaining the accuracy and completeness of data | Using error-checking on financial transactions to prevent unauthorised changes |
| Availability | Guaranteeing that information remains accessible when required | Preventing downtime of online services by using backup internet connections |
Why is Information Security Essential for Businesses?
Information security has transformed from an optional IT consideration to a critical business survival strategy. For organisations in Brisbane and across Queensland, robust information security is not just a technological necessity but a fundamental business risk management approach that protects financial stability, reputation, and operational continuity.
Financial and Reputational Protection
Cybersecurity breaches can inflict devastating financial consequences on businesses. According to Australian Cyber Security Centre, small to medium enterprises lose millions annually due to digital attacks. The potential damages extend far beyond immediate financial loss, encompassing:
- Direct Financial Costs: Expenses related to breach recovery, system restoration, and potential legal liabilities
- Reputation Damage: Loss of customer trust and potential long term brand reputation erosion
- Operational Disruption: Potential business downtime and productivity losses
Compliance and Legal Requirements
Australian businesses are increasingly subject to stringent data protection regulations. Information security is no longer optional but a legal requirement. Our guide on data security methods highlights that organisations must implement comprehensive protective measures to comply with national privacy principles and industry specific regulations.
Businesses that fail to implement adequate information security measures risk significant penalties, including substantial financial fines and potential legal actions. This regulatory landscape makes information security a critical component of responsible business management, transforming it from a technical consideration to a strategic business imperative.
The digital landscape continues to evolve, with cyber threats becoming increasingly sophisticated. For Queensland businesses, investing in robust information security is not just about preventing immediate risks but about creating a resilient, future proof operational environment that can adapt to emerging technological challenges.
How Information Security Works: Key Principles and Practices
Information security operates through a sophisticated, multilayered approach that integrates technological solutions, strategic processes, and human awareness to create a comprehensive protective ecosystem. It is not a singular tool or technique but a dynamic, adaptive framework designed to anticipate, detect, and respond to evolving digital threats.
Technological Defense Mechanisms
At the technological core of information security are advanced protective technologies that work in concert to shield digital assets. These include robust network security systems, encryption protocols, and sophisticated monitoring tools. According to the Australian Cyber Security Centre, organisations should implement comprehensive technological defences that create multiple barriers against potential cyber intrusions.
Key technological defense strategies encompass:
- Firewalls: Creating digital perimeters that filter and block potentially malicious network traffic
- Encryption: Transforming sensitive data into unreadable formats that cannot be easily compromised
- Multi Factor Authentication: Requiring multiple verification steps to access critical systems
Human and Procedural Safeguards
Technology alone cannot guarantee complete security. Human factors play a crucial role in maintaining robust information security. Our guide on computer security best practices emphasises the importance of ongoing staff training, clear security protocols, and cultivating a culture of digital awareness.
Procedural safeguards involve developing comprehensive security policies, conducting regular risk assessments, and establishing clear incident response protocols. This approach transforms information security from a purely technical challenge into a strategic organisational capability that adapts to changing threat landscapes.
For Brisbane businesses, understanding information security is about creating a holistic, proactive strategy that integrates technological solutions with human intelligence, ensuring that every layer of the organisation contributes to maintaining digital resilience.
Understanding Threats: Common Vulnerabilities and Risks
Information security threats are constantly evolving, presenting increasingly sophisticated challenges for businesses across Queensland. Understanding these potential vulnerabilities is crucial for developing effective defensive strategies that protect digital assets and organisational integrity.
Types of Cybersecurity Threats
Cybercriminals employ diverse tactics designed to exploit technological and human weaknesses. According to Australian Cyber Security Centre, modern cyber threats range from automated malware attacks to sophisticated social engineering techniques that manipulate human psychology.
The most prevalent digital vulnerabilities include:
- Phishing Attacks: Deceptive communications designed to trick individuals into revealing sensitive information
- Ransomware: Malicious software that encrypts critical data and demands financial payment for restoration
- Password Compromise: Unauthorized access through weak or stolen authentication credentials
Emerging Digital Risk Landscape
Our guide on top SMB cybersecurity threats highlights that small to medium businesses are particularly vulnerable. Cybercriminals often target organisations with perceived weaker security infrastructures, recognising that these businesses may lack comprehensive protective mechanisms.
The risk landscape is dynamic, with threats continuously adapting to technological advancements. Remote work environments, cloud migrations, and increased digital interconnectivity have expanded potential attack surfaces, making robust information security more critical than ever for Brisbane businesses.
Understanding these threats is not about generating fear but empowering organisations to develop proactive, intelligent defensive strategies that anticipate and mitigate potential digital risks before they can cause significant damage.
The following table outlines common cybersecurity threats faced by businesses, along with a brief description and the potential impact on an organisation.
| Threat | Description | Potential Impact |
|---|---|---|
| Phishing Attacks | Deceptive communications tricking individuals into revealing sensitive info | Loss of data, financial fraud |
| Ransomware | Malicious software encrypting data and demanding payment for restoration | Operational disruption, financial loss |
| Password Compromise | Unauthorised access via weak or stolen credentials | Data breach, reputational damage |

Real-World Applications of Information Security in Business
Information security transcends theoretical concepts, becoming a critical operational strategy that directly impacts business performance, customer trust, and organisational resilience. For Queensland businesses, practical implementation of information security principles means creating comprehensive protective frameworks that safeguard digital and physical assets.
Industry Specific Security Implementations
Different industries require tailored information security approaches that address unique operational challenges. According to Australian Cyber Security Centre, sector specific security strategies are essential for effectively managing digital risks.
Key industry security applications include:
- Financial Services: Implementing robust encryption for transaction data and client information
- Healthcare: Protecting patient records through stringent access controls and compliance mechanisms
- Professional Services: Securing client communications and confidential document management systems
Practical Business Protection Strategies
Our guide on data security problems and solutions emphasises that effective information security requires a holistic approach. This means integrating technological solutions, procedural guidelines, and continuous staff training to create a comprehensive defensive ecosystem.
For Brisbane businesses, real-world information security applications involve developing adaptive strategies that can respond quickly to emerging digital threats. This includes regular security audits, implementing multi factor authentication, creating incident response protocols, and maintaining up-to-date technological defences.
Ultimately, information security is not just about preventing breaches but about building a resilient organisational culture that views digital protection as a fundamental business priority.
Strengthen Your Information Security with Brisbane’s Leading Experts
Reading about the complexity of information security can feel overwhelming, especially when you realise that a single breach could threaten your data, financial stability, and reputation. If you recognise how essential confidentiality, integrity, and real-world resilience are for your business, now is the moment to take proactive action. Whether your concerns are about phishing, ransomware, or the need for industry-specific solutions, IT Start’s team understands what is at stake for Brisbane-based organisations.
Why let uncertainty leave your business exposed? Connect with specialists who turn industry concepts into simple, effective protection strategies for your workplace. Reach out for a free assessment through our contact page and see how our local expertise can take your data security to the next level. The right time to secure your business is today.
Frequently Asked Questions
What is information security?
Information security is a comprehensive approach to protecting digital and physical data from unauthorized access, theft, disruption, and potential misuse. It aims to safeguard an organisation’s critical information assets by ensuring confidentiality, integrity, and availability of data.
Why is information security important for businesses?
Information security is essential for businesses as it protects financial stability, reputation, and operational continuity. Cybersecurity breaches can lead to significant financial losses, damage to reputation, and operational disruptions.
What are the key principles of information security?
The key principles of information security include confidentiality, integrity, and availability. These principles guide the implementation of protective measures such as access controls, data encryption, and regular risk assessments.
What common threats should businesses be aware of in terms of information security?
Common threats to information security include phishing attacks, ransomware, and password compromises. Understanding these threats allows businesses to develop effective protective strategies.



