Cyberattacks now cost Australian businesses over seven billion dollars every year. For Brisbane companies using Microsoft 365, the risk of data breaches continues to grow as threats get more sophisticated and workforces become more mobile. Protecting your organisation requires much more than passwords or antivirus tools. Discover how the latest Microsoft 365 security principles and features work together to defend your business, keep sensitive information safe, and ensure full compliance with Australian regulations.
Table of Contents
- Defining Microsoft 365 Security Principles
- Core Security Features And Protections
- How Threat Detection And Response Works
- Compliance And Data Governance In Australia
- Risks, Common Gaps, And Best Practices
Key Takeaways
| Point | Details |
|---|---|
| Verify Explicitly | Implement advanced authentication methods and continuously validate access to ensure only legitimate users access sensitive resources. |
| Least Privileged Access | Limit user permissions to the necessary minimum, reducing the attack surface and potential damage from compromised accounts. |
| Assume Breach | Maintain a proactive security posture with continuous monitoring and automated threat detection to quickly respond to potential incidents. |
| Compliance and Data Governance | Utilize Microsoft 365’s features for robust data governance and compliance to align with Australian regulations and manage digital records effectively. |
Defining Microsoft 365 Security Principles
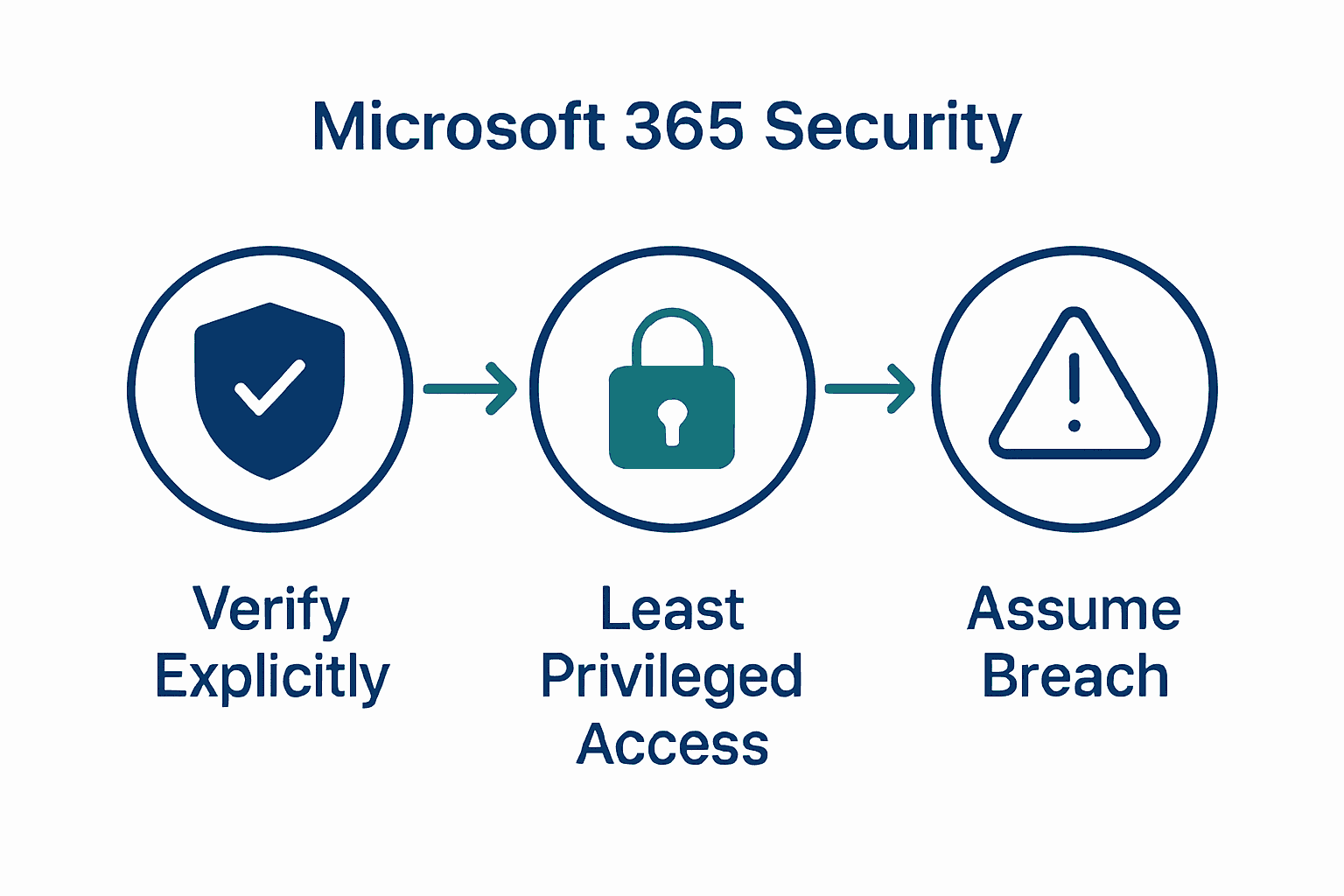
Microsoft 365 security is fundamentally about protecting your organisation’s digital ecosystem through strategic, proactive principles that safeguard data, devices, and user interactions. According to Microsoft, three core security principles guide this comprehensive approach: verify explicitly, use least privileged access, and assume breach.
The first principle, verify explicitly, means making security decisions using every available data point. This approach goes beyond traditional username and password checks, incorporating advanced authentication methods like multi-factor authentication, device health verification, and real-time risk assessment. Instead of assuming trust, Microsoft 365 security continuously validates each access attempt, ensuring only legitimate users can interact with sensitive organisational resources.
The second principle focuses on least privileged access, which limits user permissions to the absolute minimum required for their specific job functions. This strategic limitation dramatically reduces potential attack surfaces by preventing unnecessary system-wide access. By implementing granular permission controls, organisations can significantly minimise the potential damage if a user account becomes compromised.

The final foundational principle is to assume breach, which represents a proactive mindset of constant vigilance. Microsoft Purview emphasises that security isn’t about preventing every possible intrusion, but preparing robust response mechanisms. This principle drives continuous monitoring, automated threat detection, and rapid incident response strategies. By anticipating potential security incidents, organisations can develop resilient systems that quickly detect, isolate, and mitigate potential cyber threats.
For Brisbane small and medium businesses looking to implement these principles, understanding the nuanced approach of Microsoft 365 Security Best Practises for Brisbane SMBs can provide additional localised insights into practical implementation.
Core Security Features and Protections
Microsoft 365 offers a comprehensive suite of security features designed to protect businesses from evolving digital threats. Microsoft Purview provides robust information governance capabilities that enable organisations to manage their data lifecycle with intelligent and defensible policies.
Key security features include advanced threat protection, data loss prevention, and identity management. The platform integrates multiple layers of security across different domains. Advanced threat protection monitors email, documents, and collaboration platforms for potential security risks, using machine learning and artificial intelligence to detect and prevent sophisticated cyber attacks before they can cause damage.
Data loss prevention mechanisms are particularly critical for Brisbane businesses handling sensitive information. These tools automatically scan and protect confidential data across emails, cloud storage, and collaborative platforms. By implementing granular controls, organisations can prevent accidental or intentional data leaks, ensuring compliance with Australian privacy regulations.
Microsoft Purview Compliance Manager extends security capabilities by offering comprehensive compliance management. This feature helps businesses meet complex regulatory requirements across multiple cloud environments. The system provides scalable assessments, customisable templates, and built-in capabilities that simplify the complex landscape of data governance and regulatory compliance.
For local Brisbane SMBs seeking to enhance their digital security, our Microsoft 365 Security Best Practises for Brisbane SMBs guide offers tailored insights into implementing these advanced security features effectively.
How Threat Detection and Response Works
Threat detection and response in Microsoft 365 represent a sophisticated, multi-layered approach to cybersecurity that goes far beyond traditional defensive strategies. Microsoft Purview dynamically secures data throughout its lifecycle, identifying and mitigating risks across clouds, devices, and platforms with unprecedented precision and speed.
The core of threat detection involves continuous monitoring and intelligent analysis. Advanced machine learning algorithms constantly scan your organisation’s digital environment, tracking user behaviors, network interactions, and potential anomalies. These systems don’t just look for known threat signatures but proactively identify suspicious patterns that might indicate an emerging cybersecurity risk. When unusual activities are detected, such as unexpected login attempts, large data transfers, or access from unfamiliar locations, the system immediately triggers alerts and can automatically initiate protective measures.
Risk mitigation is where Microsoft 365’s threat response truly shines. Microsoft Purview provides sophisticated capabilities to detect potential oversharing risks, protect against data leaks, and dynamically adjust governance policies. The system analyzes interactions with sensitive data, offering real-time alerts about risky activities and automatically implementing predefined response protocols. This might involve temporarily restricting user access, quarantining suspicious files, or initiating comprehensive system scans to prevent potential breach propagation.
For Brisbane small and medium businesses seeking to understand these complex security mechanisms, our Microsoft 365 Security Best Practises for Brisbane SMBs guide offers practical insights into implementing these advanced threat detection strategies effectively.
Compliance and Data Governance in Australia
Data governance in Australia demands meticulous attention to regulatory requirements, and Microsoft 365 provides comprehensive tools to help organisations navigate this complex landscape. National Archives of Australia emphasises the critical responsibility of managing digital records across various platforms, including office applications, email, file hosting, and collaborative environments.
For Australian businesses, compliance is not just a checkbox but a strategic imperative. The Microsoft 365 ecosystem offers robust information management capabilities that align with local regulatory standards. This includes granular control over data retention, precise access management, and comprehensive audit trails that meet the stringent requirements of Australian privacy and data protection regulations. These features enable organisations to demonstrate accountability and maintain transparency in their digital information management practices.
Microsoft and Objective Corporation have developed sophisticated solutions that help organisations balance digital communication with rigorous information governance. Their collaborative approach ensures that information shared in hybrid digital environments remains subject to strict control, maintaining compliance with record-keeping and reporting requirements. This is particularly crucial for industries handling sensitive data, such as finance, healthcare, and government services.
For Brisbane businesses seeking to understand the nuanced landscape of IT security compliance, our Understanding What is IT Security Compliance guide provides deeper insights into navigating these complex regulatory requirements effectively.
Risks, Common Gaps, and Best Practices
Navigating the complex landscape of Microsoft 365 security requires a strategic approach to identifying and mitigating potential vulnerabilities. Affinity Data emphasises the critical importance of comprehensive data management solutions that address the multifaceted challenges of modern digital environments.
Common security gaps often emerge from overlooked aspects of data governance and user management. These typically include inadequate access controls, inconsistent data classification, and limited visibility into data movements across organisational systems. Key risks involve unauthorized data sharing, insufficient user authentication mechanisms, and blind spots in monitoring potential security breaches. Organizations must implement multi-layered security strategies that go beyond basic perimeter defenses, focusing on granular control and continuous monitoring of digital interactions.
Agile Insights highlights several best practices for mitigating these risks through Microsoft Purview’s advanced capabilities. These include comprehensive data cataloging, precise data mapping, intelligent data classification, and complete data lineage tracking. By implementing these strategies, businesses can:
- Discover and map sensitive information across their entire digital ecosystem
- Establish granular access controls
- Create automated governance policies
- Continuously monitor and classify data risks
- Develop proactive threat detection mechanisms
For Brisbane businesses looking to dive deeper into understanding and implementing these critical security strategies, our Understanding Essential Data Security Methods for Businesses guide provides practical, actionable insights tailored to local business needs.
Secure Your Brisbane Business with Expert Microsoft 365 Support
The article highlights the crucial challenge of protecting your organisation against advanced cyber threats through principles like verify explicitly, least privileged access and assume breach. Many Brisbane SMBs face pain points such as limited visibility into data movements, managing compliance risks, and responding swiftly to security incidents. These concerns can feel overwhelming without the right expertise and tools in place.
At IT Start, we understand the importance of implementing comprehensive security strategies that align perfectly with Microsoft 365’s core principles. Our managed IT support and cybersecurity solutions for Brisbane businesses give you:
- Proactive threat detection and continuous monitoring
- Tailored access controls that enforce least privilege policies
- Compliance management aligned with Australian regulations
If you want to confidently protect your data and keep your business running without disruptions, explore how our local experts can help. Start your journey with a free assessment by visiting Contact IT Start today. Don’t leave your security to chance. Secure your future with trusted Microsoft 365 security support designed for Brisbane SMBs in mind.
Learn more about strengthening your digital defences in our comprehensive Microsoft 365 Security Best Practises for Brisbane SMBs guide and take the first step to protect your organisation with confidence.
Frequently Asked Questions
What are the core security principles of Microsoft 365?
The core security principles of Microsoft 365 are verify explicitly, use least privileged access, and assume breach. These principles focus on continuous validation of user access, limiting user permissions, and maintaining a proactive mindset against potential breaches.
How does Microsoft 365 protect against data loss?
Microsoft 365 implements data loss prevention mechanisms that automatically scan and protect sensitive information across emails, cloud storage, and collaboration platforms. This helps prevent accidental or intentional data leaks and ensures compliance with privacy regulations.
What is the role of threat detection and response in Microsoft 365?
Threat detection and response involve continuous monitoring and intelligent analysis of user behaviors and network interactions. Microsoft 365 uses advanced machine learning algorithms to detect anomalies and proactively identify emerging cybersecurity risks, triggering alerts and response protocols when necessary.
How does Microsoft 365 assist with compliance and data governance?
Microsoft 365 offers robust information management capabilities that help organisations meet regulatory requirements by providing granular control over data retention, precise access management, and comprehensive audit trails. This ensures accountability and transparency in digital information management practices.



