More than 60 percent of data breaches in Australia target vulnerable servers, putting countless businesses at risk every year. Staying ahead of these threats depends on a proactive approach to Windows Server security. Understanding the critical steps to assess, configure, and monitor your environment can make a powerful difference in protecting your Brisbane business from costly cyberattacks.
Table of Contents
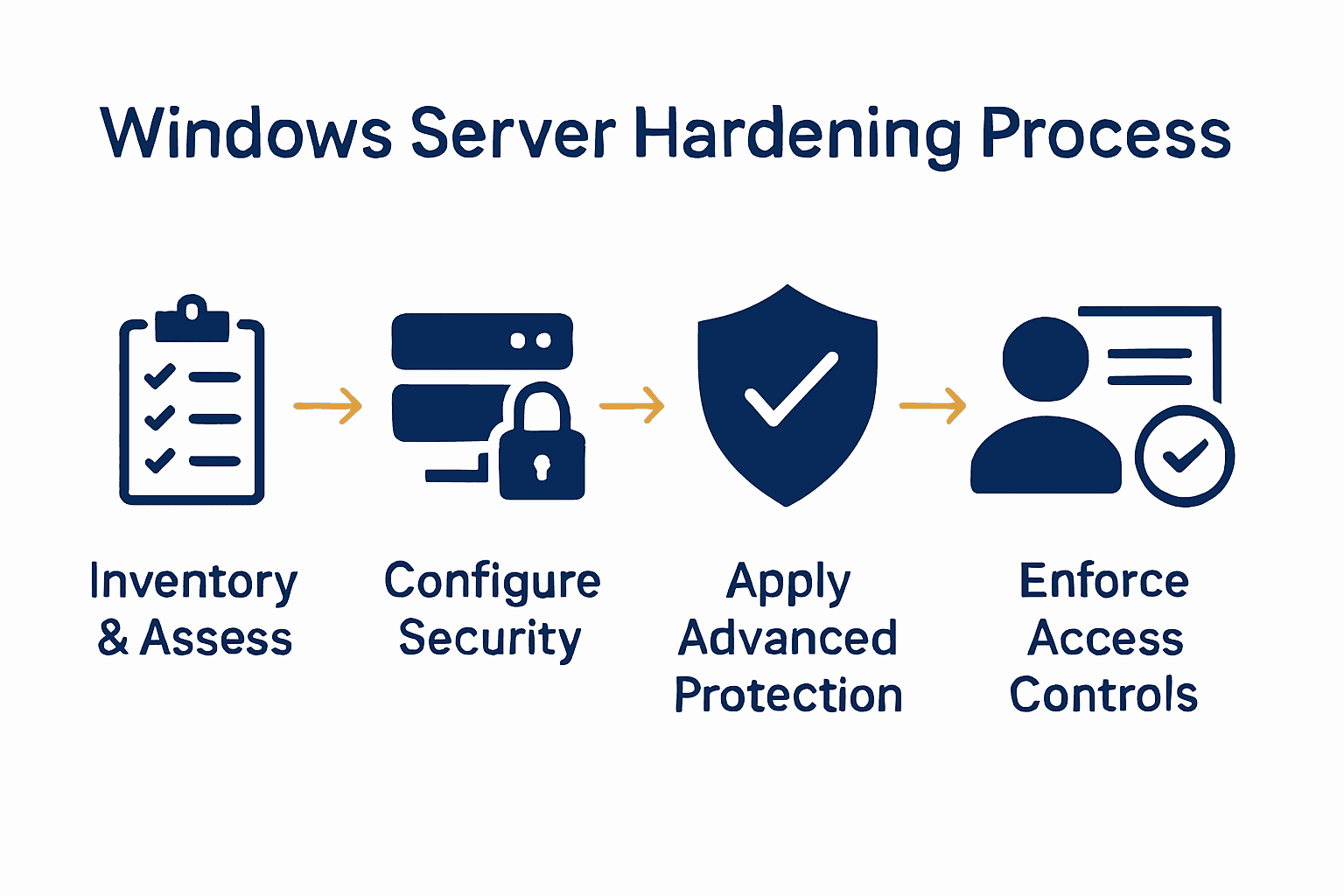
- Step 1: Assess Current Windows Server Environment
- Step 2: Apply Essential Security Configurations
- Step 3: Enable Advanced Threat Protection Features
- Step 4: Enforce Access And Account Controls
- Step 5: Verify Server Security And Compliance
Quick Summary
| Key Point | Explanation |
|---|---|
| 1. Create a comprehensive server inventory | Document all existing Windows Server systems, including OS versions and architectures to identify vulnerabilities. |
| 2. Enforce a secure Standard Operating Environment | Apply a secure-by-default approach, disable unnecessary services, and restrict unapproved applications to minimize risks. |
| 3. Implement multi-factor authentication | Strengthen user verification by requiring multiple forms of authentication to reduce unauthorized access effectively. |
| 4. Enable full disk encryption on servers | Protect sensitive data through encryption, ensuring data remains secure even if hardware is compromised. |
| 5. Develop a System Security Plan | Create a detailed security document that aligns with compliance standards and includes auditing and logging for ongoing security assessment. |
Step 1: Assess current Windows Server environment
Your Windows Server environment assessment starts with a systematic review that protects your Brisbane business from potential cybersecurity vulnerabilities. According to the Australian Signals Directorate’s guidelines for system hardening, you will need to thoroughly examine your current server configurations and operating system versions.
Begin by creating an inventory of all existing Windows Server systems in your organisation. Document each server’s current version, including whether it runs a 64-bit architecture as recommended by cybersecurity experts. Focus on identifying any servers running unsupported or legacy Windows versions, which cyber.gov.au warns can introduce significant security risks.
Next, review each server’s installed services and roles. Disable any unnecessary services that are not critical to your business operations. This approach aligns with the Australian Signals Directorate’s recommendation of maintaining a lean, secure Standard Operating Environment (SOE).
Pro Tip: Document everything meticulously. Your server inventory will become a crucial reference for future hardening and upgrade processes.
As you complete this assessment, prepare to transition into a comprehensive server hardening strategy. The insights you gather now will directly inform your security improvements and help protect your organisation’s digital infrastructure.
Here’s a summary of each server hardening step and its key actions:
| Step | Focus Area | Key Actions |
|---|---|---|
| Assess Environment | Inventory & Audit | List servers Check OS versions Identify legacy systems |
| Apply Security Configurations | System Hardening | Enforce SOE Disable unnecessary services Secure authentication |
| Enable Advanced Threat Protection | Risk Mitigation | Enable encryption Application control Secure boot and devices |
| Enforce Access Controls | Account Security | Multi-factor authentication Account lockout Role-based access |
| Verify Security & Compliance | Ongoing Assurance | Create security plan Audit logs Isolate legacy systems |
Step 2: Apply essential security configurations
Applying essential security configurations is your critical next step in protecting your Brisbane business’s Windows Server infrastructure. According to the Australian Signals Directorate (ASD), this involves implementing strategic hardening measures that significantly reduce potential security vulnerabilities.
Start by enforcing a secure Standard Operating Environment (SOE). This means configuring your servers with a secure-by-default approach. Learn how to secure business laptops can provide additional context for broader endpoint security strategies. Disable user installation of unapproved applications and implement robust application control mechanisms to prevent unauthorized software deployment.
Next, focus on network authentication settings. As recommended in the ASD Blueprint for Secure Cloud, enforce NTLMv2 authentication, disable legacy LM hashes, and implement strong cryptography protocols. Configure PowerShell to only allow signed scripts and restrict registry editing tools to prevent potential manipulation.
Pro Tip: Always document your configuration changes and maintain a baseline security configuration that can be quickly restored if needed.
Remote access requires special attention. Disable unnecessary remote desktop and remote assistance features. Enable SMB signing to protect against network-level attacks and ensure all communication channels are securely configured.
As you complete these configurations, you are building a resilient server environment that meets Australian cybersecurity best practices.
 Your next step will involve continuous monitoring and periodic security reviews to maintain this hardened infrastructure.
Your next step will involve continuous monitoring and periodic security reviews to maintain this hardened infrastructure.
Step 3: Enable advanced threat protection features
Advanced threat protection is your strategic defence against sophisticated cybersecurity risks targeting Windows Server environments. According to cyber.gov.au, implementing robust security features can dramatically reduce your organisation’s vulnerability to complex digital threats.
Begin by enabling full disk encryption across all Windows Server systems. This critical protection ensures that even if physical hardware is compromised, your data remains secure. Learn how to secure business laptops can provide complementary insights into endpoint encryption strategies.
As recommended by the Australian Signals Directorate, implement comprehensive application control mechanisms. This involves creating strict rules using cryptographic or publisher verification to prevent unauthorized software installation. Configure your systems to block unprivileged users from installing applications or tampering with security tools.
Pro Tip: Regularly update your application control policies to maintain a dynamic and responsive security posture.
Next, focus on device access control. Limit removable media interfaces and disable direct memory access (DMA) for external devices. Enable Windows Secure Boot to prevent unauthorized firmware or bootloader modifications. Implement Smart App Control to add an additional layer of protection against potential malware and unauthorized software execution.
These advanced threat protection features transform your Windows Server from a potential vulnerability into a robust security fortress.
Your next phase will involve continuous monitoring and fine-tuning of these protective measures to ensure optimal defence against emerging cyber threats.
Step 4: Enforce access and account controls
Enforcing robust access and account controls is fundamental to protecting your Windows Server environment from unauthorized access and potential security breaches. Understanding access control provides a critical foundation for implementing comprehensive security measures.
Begin by documenting and implementing multi-factor authentication across all server systems. As recommended by the Australian Signals Directorate (ASD) Blueprint, this approach significantly strengthens user authentication and reduces the risk of unauthorized access. Configure strict authentication policies that require complex passwords and regular password rotations.
Implement aggressive account lockout policies to prevent brute force attacks. The ASD guidelines suggest implementing mechanisms that lock accounts after a specific number of failed login attempts. This means configuring your Windows Server to temporarily disable account access after multiple incorrect password entries, creating a powerful deterrent against potential intrusions.
Pro Tip: Create a formal process for account recovery and management to ensure legitimate users can regain access while maintaining security protocols.
Restrict unprivileged accounts from performing critical system actions. This includes preventing standard users from installing or uninstalling applications, modifying system configurations, or accessing sensitive server resources. Implement role based access controls that provide minimal necessary permissions for each user role.
Your final step involves continuous monitoring and periodic review of access control mechanisms. This ensures your security posture remains adaptive and responsive to emerging threats, maintaining a robust defense for your Brisbane business infrastructure.
Step 5: Verify server security and compliance
Verifying server security and compliance is the critical final stage in hardening your Windows Server infrastructure. Understanding IT security compliance provides the foundational framework for this comprehensive assessment.
Begin by developing a detailed System Security Plan as recommended by the Australian Signals Directorate (ASD) Secure Cloud Blueprint. This document should meticulously capture your server configurations, security policies, and implemented control measures. Align your documentation with the Information Security Manual (ISM) controls to ensure a robust compliance framework.
Implement centralised logging and comprehensive auditing mechanisms. According to cyber.gov.au, this approach enables continuous monitoring of system activities, helping you track potential security incidents and maintain an accurate record of server interactions. Configure detailed audit logs that capture user activities, system changes, and access attempts.
Pro Tip: Establish a regular review schedule for your security logs to identify potential vulnerabilities before they can be exploited.
Create isolation strategies for any legacy or unsupported systems. This involves segmenting these servers from critical network infrastructure and implementing additional protective measures to mitigate potential security risks. Develop a clear plan for eventual replacement or upgrades to ensure ongoing system security.
Your final objective is to create a dynamic security verification process that adapts to emerging threats and maintains the highest standards of server protection for your Brisbane business infrastructure.
Secure Your Brisbane Business with Expert Windows Server Hardening Support
Hardening your Windows Server environment is essential to safeguard your business against evolving cyber threats as outlined in the Windows Server 2025 Hardening Guide for Brisbane SMEs. Challenges like managing legacy systems, enforcing strict access controls, and enabling advanced threat protection can feel overwhelming without local IT expertise. Effectively applying security configurations and maintaining ongoing compliance are crucial to protect your data and maintain business continuity.
At IT Start, we understand these pain points and specialise in helping Brisbane businesses implement comprehensive server security measures tailored for SMEs. Our proactive managed IT support includes detailed environment assessments, configuration hardening, and continuous monitoring aligned with Australian cybersecurity standards. Don’t leave your critical infrastructure exposed or risk operational disruption.
Take control now by booking your free security assessment with us to start strengthening your server defence. Visit Contact IT Start to arrange your personalised consultation. Protect your business and build resilient IT systems today with trusted local partners who understand the unique cybersecurity challenges Brisbane businesses face.
Frequently Asked Questions
How do I start assessing my Windows Server 2025 environment for security?
Begin by creating an inventory of all existing Windows Server systems in your organization. Document each server’s current version and configuration to identify any unsupported or legacy versions that may pose security risks.
What are the essential security configurations I should apply to Windows Server 2025?
Enforce a secure Standard Operating Environment (SOE) by configuring your servers with a secure-by-default approach. Disable unnecessary services and establish strong authentication settings to reduce vulnerabilities immediately.
How can I enable advanced threat protection on Windows Server 2025?
Enable full disk encryption and comprehensive application control mechanisms across your Windows Server systems. Implement policies to block unauthorized software installation and regularly update these controls to adapt to new threats.
What account controls should I enforce for enhanced server security?
Implement multi-factor authentication and aggressive account lockout policies to significantly reduce the risk of unauthorized access. Restrict unprivileged accounts from performing critical actions, creating a more secure environment.
How do I verify server security and compliance after hardening?
Develop a detailed System Security Plan that captures your server configurations and security measures. Implement centralized logging and regularly review security logs to identify and address any potential vulnerabilities promptly.
What steps should I take to isolate legacy systems during the hardening process?
Create isolation strategies by segmenting legacy or unsupported systems from critical network infrastructure. Schedule a plan for eventual replacement or upgrades to mitigate security risks and maintain overall system integrity.



