Cyber attacks on servers have surged by over 50 percent in the past year, putting business data and operations at serious risk. Even a single overlooked vulnerability can open the door to devastating breaches or costly downtime. By taking a structured approach to hardening your Windows Server 2025 environment, you strengthen defenses and protect your most valuable assets from evolving threats.
Table of Contents
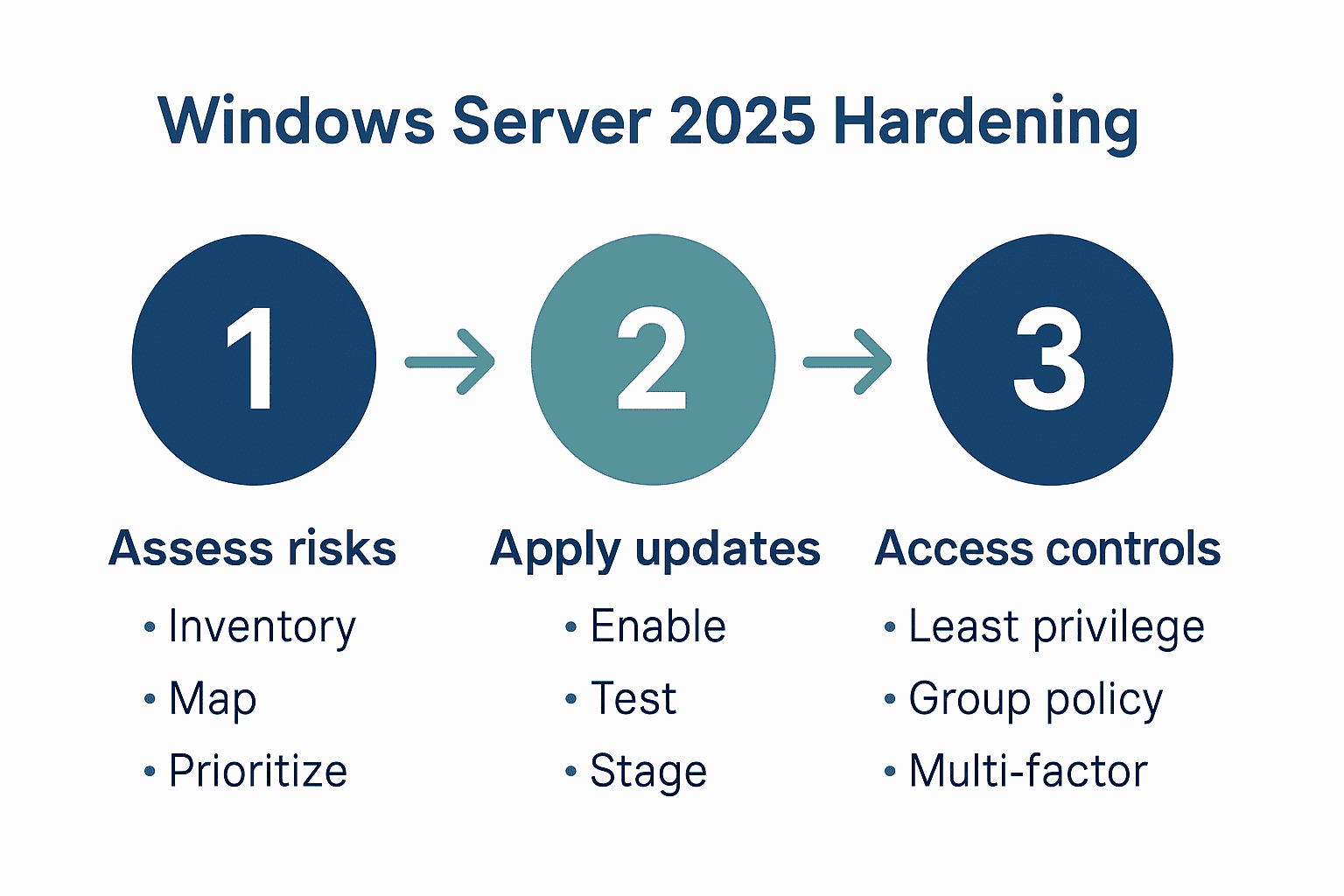
- Step 1: Assess Server Environment And Baseline Risks
- Step 2: Apply Essential Security Updates And Patches
- Step 3: Configure Strong Access Controls And Policies
- Step 4: Implement Advanced Security Features
- Step 5: Verify Server Hardening With Security Audits
Quick Summary
| Key Point | Explanation |
|---|---|
| 1. Conduct a thorough risk assessment | Identify and document security vulnerabilities in your server setup to create a clear baseline for improvements. |
| 2. Apply critical security updates promptly | Enable automatic updates and manually validate patches to protect against known threats affecting your server. |
| 3. Implement least privilege access controls | Assign users the minimum access necessary for their roles to reduce the risk of unauthorized access. |
| 4. Configure advanced security features | Deploy technologies like Measured Boot and application control to strengthen defenses against advanced cyber threats. |
| 5. Perform regular security audits | Conduct vulnerability scans and penetration tests to validate the effectiveness of your security measures and identify gaps. |
Step 1: Assess Server Environment and Baseline Risks
When hardening a Windows Server 2025 environment, your first critical task is understanding the baseline security risks lurking in your current setup. According to the Australian Cyber Security Centre, a systematic six-step risk management process can help you methodically identify and mitigate potential vulnerabilities.
Start by conducting a comprehensive inventory of your server infrastructure. Document every single server, its current configuration, network connections, installed software, and active user accounts. This baseline assessment gives you a clear snapshot of your existing environment and helps pinpoint potential security weak spots.
Next, map out your network topology and identify all potential entry points. Look for open ports, unnecessary services running in the background, and outdated software versions that could create security gaps. Pay special attention to default configurations that might expose your systems to unnecessary risks.
Pro Tip: Use automated scanning tools to help identify misconfigurations and potential vulnerabilities more efficiently than manual processes.
As you assess your environment, categorise risks based on their potential impact. High-risk items might include unpatched systems, weak authentication mechanisms, or unnecessarily broad user permissions. Create a prioritised list that will guide your hardening strategy, focusing first on the most critical vulnerabilities that could compromise your server’s security.
By the end of this assessment, you will have a clear roadmap for strengthening your Windows Server 2025 environment. The next step involves selecting and implementing targeted security controls to address the risks you’ve identified.
Step 2: Apply Essential Security Updates and Patches
In this critical stage of server hardening, you will systematically update and patch your Windows Server 2025 environment to protect against known vulnerabilities. According to the Australian Signals Directorate, tracking end-of-support dates and applying patches promptly is fundamental to maintaining robust cybersecurity.
Begin by configuring automatic update settings in Windows Server 2025. Enable Windows Update to download and install critical security patches immediately after they become available. Pay special attention to patches rated as high severity or those addressing potential remote code execution vulnerabilities.
Manually review and validate each patch before full deployment. While automatic updates are convenient, your specific server environment might require custom testing to ensure patches do not disrupt critical services. Create a staged rollout process where patches are first tested in a controlled environment before broad implementation.
Warning: Always maintain a complete system backup before applying major updates to ensure quick recovery if unexpected issues arise.
The Australian Cyber Security Centre recommends prioritising patches based on vulnerability severity. Focus first on updates that address critical security flaws, particularly those potentially exposing remote access or administrative controls.
By methodically applying these security updates, you significantly reduce your server’s attack surface and protect your business infrastructure from known exploits.
 Your next step will involve configuring advanced security controls to further fortify your server environment.
Your next step will involve configuring advanced security controls to further fortify your server environment.
Step 3: Configure Strong Access Controls and Policies
In this crucial stage of server hardening, you will design and implement robust access control mechanisms that protect your Windows Server 2025 environment from unauthorized access. Understanding access control is fundamental to creating a secure and manageable server infrastructure.
Start by implementing the principle of least privilege across your entire server environment. This means every user account should have the minimum level of access required to perform their specific job functions. Review each user role carefully and assign permissions that are strictly necessary for their work responsibilities.
Create granular user groups that reflect different organizational roles and responsibilities. Instead of assigning individual permissions, build comprehensive group policies that can be easily managed and updated. This approach simplifies access management and reduces the risk of accidental permission escalation.
Pro Tip: Regularly audit and review user access rights at least quarterly to ensure they remain appropriate and aligned with current job functions.
Implement multi factor authentication for all administrative accounts. This adds an extra layer of security beyond traditional username and password combinations. Consider using hardware tokens or authenticator applications that generate time sensitive access codes.
Configure detailed logging and monitoring for all access attempts. Set up alerts for suspicious activities such as multiple failed login attempts or access from unusual geographic locations. These monitoring mechanisms will help you quickly detect and respond to potential security breaches.
By methodically establishing these access controls, you create a robust security framework that significantly reduces the risk of unauthorized system access.
Your next step will involve implementing advanced network segmentation to further enhance your server environment’s security posture.
Step 4: Implement Advanced Security Features
In this critical stage of server hardening, you will deploy sophisticated security mechanisms that significantly enhance your Windows Server 2025 environment’s resilience against advanced cyber threats. According to Australian Cyber Security Centre guidance, implementing targeted security features can dramatically reduce your attack surface.
Begin by configuring Measured Boot via UEFI and Trusted Platform Module (TPM) technologies. These advanced features validate your server hardware and software integrity during startup, preventing unauthorized modifications to critical boot components. Enable TPM 2.0 in your server BIOS settings and configure secure boot options to ensure only authenticated firmware and operating system components can load.
Implement robust application control rules that strictly define which software can execute within your server environment. Create comprehensive whitelisting policies that permit only approved applications and prevent unauthorized executable files from running. This approach provides granular control over software execution and minimizes potential malware infiltration risks.
Warning: Test application control rules extensively in a staging environment to prevent accidental system lockouts.
Activate Windows Defender Exploit Guard and configure its attack surface reduction rules. These advanced protection mechanisms block suspicious script activities, prevent credential theft techniques, and limit potential exploit pathways. Customize the rules to match your specific server workload and organizational security requirements.
Configure advanced user access controls that go beyond traditional permission settings. Implement just-in-time administrative access, which provides temporary elevated permissions only when necessary. This approach minimizes the potential window of vulnerability associated with standing administrative privileges.
By methodically implementing these advanced security features, you create multiple layers of protection that significantly enhance your server’s resilience. Your next step involves establishing comprehensive monitoring and logging mechanisms to maintain ongoing visibility into your server environment.
Step 5: Verify Server Hardening with Security Audits
In this critical verification phase, you will systematically assess the effectiveness of your Windows Server 2025 security hardening efforts. According to the Information Security Registered Assessors Program (IRAP), an independent assessment process helps identify potential security gaps and validate implemented controls.
Begin by conducting a comprehensive vulnerability scanning across your server infrastructure. Use professional security assessment tools that can perform detailed network and system scans, identifying potential misconfigurations, unpatched vulnerabilities, and potential entry points for cyber attackers. These tools will generate detailed reports highlighting areas requiring immediate attention.
Implement penetration testing methodologies to simulate real world attack scenarios. Engage either internal security experts or external professional services to conduct controlled simulated attacks. These tests will help you understand how an actual threat actor might attempt to compromise your server environment and reveal any remaining weaknesses in your security architecture.
Pro Tip: Rotate your penetration testing team and methodology regularly to ensure you get diverse perspectives on potential vulnerabilities.
Following ISO/IEC 27007 guidance, develop a structured audit checklist that systematically reviews your implemented security controls. This checklist should cover aspects like access management, patch levels, network segmentation, encryption standards, and logging mechanisms. Ensure each control is not just implemented but functioning as intended.
Conduct a thorough review of all system logs and access records. Look for unusual patterns, unauthorized access attempts, or potential security anomalies. Cross reference these logs with your implemented security controls to validate their effectiveness and identify any potential blind spots in your monitoring strategy.
By rigorously verifying your server hardening through these comprehensive audit processes, you create a robust feedback loop that continuously improves your security posture. Your final step involves developing an ongoing maintenance and monitoring strategy to sustain these high security standards.
Here’s an overview of each server hardening step and its core focus:
| Step | Main Goal | Key Actions |
|---|---|---|
| 1: Assess Environment | Identify risks & baseline | Inventory servers Map topology Prioritise vulnerabilities |
| 2: Apply Updates | Patch known vulnerabilities | Enable automatic updates Test patches Stage rollouts |
| 3: Access Controls | Restrict unauthorised access | Least privilege Group policies Multi factor authentication |
| 4: Advanced Features | Strengthen technical defences | Measured Boot Application control Exploit Guard |
| 5: Security Audits | Validate hardening effectiveness | Vulnerability scans Penetration tests Audit checklists |
Secure Your Windows Server 2025 with Expert IT Support from IT Start
Hardening your Windows Server 2025 environment is essential to protect your business from cyber threats and compliance pitfalls. If you are feeling overwhelmed by managing risks like unpatched vulnerabilities, weak access controls, or configuring advanced security features such as Measured Boot and Exploit Guard, you are not alone. These challenges demand specialised knowledge and constant vigilance to keep your Brisbane-based business safe and operational.
At IT Start, we understand the pain points of small to medium-sized enterprises striving to create a secure and resilient server infrastructure. Our managed IT support and cybersecurity services are tailored to help you implement effective risk assessments, enforce strong access policies, and verify your security posture through comprehensive audits. With our local expertise and proven processes, we deliver proactive protection so you can focus on growing your business without worrying about hidden threats.
Ready to take the next step towards a fully secured Windows Server 2025 environment? Discover how our Brisbane team can provide transparent, reliable IT management customised for your industry by booking a free consultation today at IT Start Contact Us. Don’t leave your server security to chance act now and partner with IT Start to build a powerful defence against cyber risks.
Frequently Asked Questions
How do I assess the security risks in my Windows Server 2025 environment?
Begin by conducting a comprehensive inventory of all servers, documenting their configurations, software, and user accounts. This will help you identify vulnerabilities that need addressing, which should be prioritized based on potential impact.
What steps should I take to ensure my Windows Server 2025 is updated and secure?
Enable automatic updates to apply security patches as they become available. Review and test each patch in a controlled environment before deploying it widely to minimize disruption while ensuring your system is protected against known vulnerabilities.
How can I implement strong access controls on Windows Server 2025?
Apply the principle of least privilege by assigning the minimum necessary permissions to each user account. Regularly review and adjust these permissions, ensuring they align with current job responsibilities, ideally on a quarterly basis.
What advanced security features should I configure for my Windows Server 2025?
Activate Measured Boot and configure application control rules to only allow approved software to run. These measures help protect against unauthorized changes and minimize the risk of malware infections.
How do I validate that my Windows Server 2025 hardening efforts are effective?
Conduct regular security audits that include vulnerability scans and penetration testing. Create a structured audit checklist to assess implemented controls, ensuring they are functioning properly and identifying any areas for improvement.
What ongoing maintenance should I perform to sustain high security standards on Windows Server 2025?
Establish a continual monitoring strategy that involves regularly checking system logs for unusual activity and reassessing security controls. Aim to review and update your security measures at least every six months to keep your server environment secure.



