Cyber attacks are getting smarter every year and businesses face an uphill battle to keep their data safe. More than 67 percent of Australian organisations experienced a cyber incident last year. Oddly enough, even the most high-tech solutions can miss the mark if you skip one simple security principle. Sometimes a well-trained employee can stop a digital breach faster than the flashiest firewall.
Table of Contents
- What Are Cyber Security Methods And Why Are They Important?
- Key Concepts Behind Cyber Security Methods
- How Cyber Security Methods Protect Your Business
- Real-World Applications Of Cyber Security Methods
- Emerging Trends In Cyber Security Methods
Quick Summary
| Takeaway | Explanation |
|---|---|
| Implement multilayered security | Create multiple defensive barriers to protect infrastructure against digital threats. |
| Prioritise proactive threat detection | Continuously monitor digital environments to identify and mitigate security risks early. |
| Adapt strategies to industry needs | Tailor your cybersecurity methods according to specific sector vulnerabilities and threats. |
| Integrate advanced technologies | Use AI and machine learning for predictive threat analysis and autonomous responses. |
| Focus on employee awareness training | Educate staff on cybersecurity best practices to strengthen overall organisational defense. |
What are Cyber Security Methods and Why Are They Important?
Cyber security methods represent strategic approaches businesses use to protect digital assets, networks, and systems from malicious attacks and potential breaches. These comprehensive techniques aim to safeguard sensitive information, maintain operational integrity, and prevent unauthorized access to critical technological infrastructure.
The Core Purpose of Cyber Security Methods
At its fundamental level, cyber security methods exist to create robust protective barriers around an organisation’s digital ecosystem. Cyber security strategies developed by the Australian Cyber Security Centre emphasise the critical nature of proactively defending against potential digital threats.
Businesses face numerous digital vulnerabilities that can compromise operational stability and financial security. Key risks include:
- Data theft and unauthorized information access
- Financial fraud through system infiltration
- Reputation damage from security breaches
- Potential legal and compliance challenges
Understanding Comprehensive Protection Strategies
Effective cyber security methods integrate multiple layers of protection, combining technological tools, human awareness, and strategic protocols. Read more about our comprehensive security approaches to understand how businesses can create resilient digital defense mechanisms.
These methods typically encompass network security, endpoint protection, encryption technologies, and continuous monitoring systems. The goal is not just preventing attacks but creating an adaptive, responsive security infrastructure that can quickly identify and neutralise potential threats before they cause significant damage.
By implementing robust cyber security methods, businesses in Brisbane and across Queensland can protect their operational integrity, maintain customer trust, and mitigate potentially devastating financial and reputational risks associated with digital vulnerabilities.
Key Concepts Behind Cyber Security Methods
Cyber security methods are built upon fundamental principles designed to create comprehensive digital protection strategies for organisations. Understanding these core concepts helps businesses develop robust and adaptive security frameworks that effectively mitigate potential technological risks.
The Fundamental Principles of Digital Defense
At the heart of cyber security methods lie several critical principles that guide protective strategies. Research from the Australian Signals Directorate highlights the importance of implementing systematic approaches to digital security.
Key foundational concepts include:
Below is a table outlining the core principles of digital defence as described in the article, providing concise definitions to aid understanding of each foundational concept.
| Principle | Definition |
|---|---|
| Confidentiality | Ensuring sensitive information remains accessible only to authorised personnel |
| Integrity | Maintaining the accuracy and consistency of data throughout its lifecycle |
| Availability | Guaranteeing that systems and information remain accessible when required |
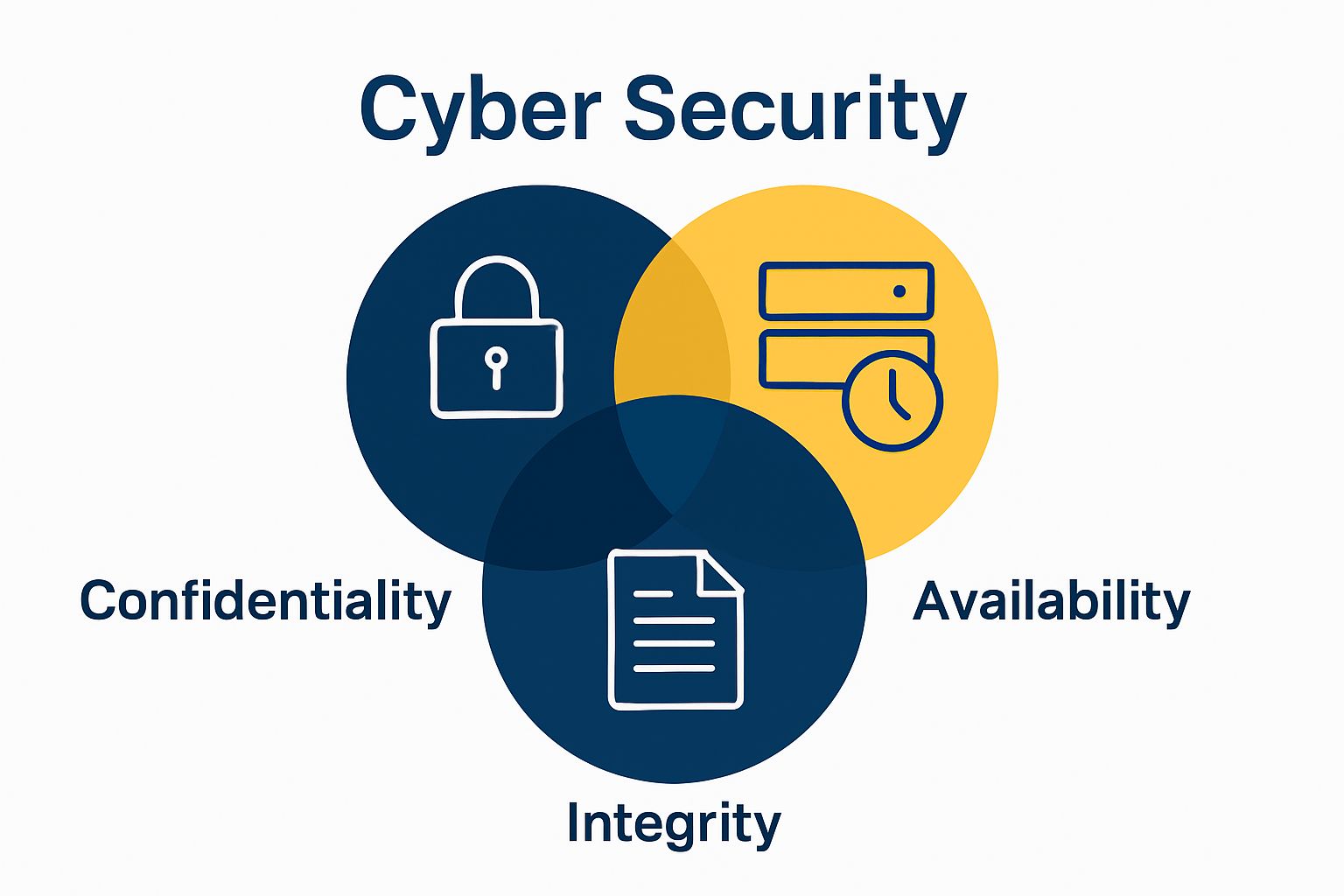
- Confidentiality: Ensuring sensitive information remains accessible only to authorised personnel
- Integrity: Maintaining the accuracy and consistency of data throughout its lifecycle
- Availability: Guaranteeing that systems and information remain accessible when required
Multilayered Security Architecture
Effective cyber security methods operate through a multilayered approach, creating multiple defensive barriers that work in concert to protect digital infrastructure. Learn more about our comprehensive security strategies to understand how these layers interact and provide holistic protection.
This architectural strategy involves implementing protection mechanisms across different technological domains including network security, application security, operational security, and disaster recovery planning. Each layer provides additional complexity that makes penetrating the system increasingly difficult for potential attackers.
By comprehensively understanding and implementing these key cyber security concepts, Brisbane businesses can create sophisticated digital defense mechanisms that adapt to evolving technological threats and protect their critical organisational assets.
How Cyber Security Methods Protect Your Business
Cyber security methods function as comprehensive protective shields, actively defending businesses against increasingly sophisticated digital threats. These strategic approaches work systematically to identify, prevent, and neutralise potential security vulnerabilities across an organisation’s technological infrastructure.
Proactive Threat Detection and Prevention
The Australian Cyber Security Centre guidelines emphasise the importance of anticipating and mitigating potential security risks before they escalate. Businesses can protect themselves by implementing robust mechanisms that continuously monitor and analyse digital environments.
Key protective strategies include:
- Real-time network traffic monitoring
- Automated threat identification systems
- Continuous vulnerability assessment
- Rapid incident response protocols
Comprehensive Digital Infrastructure Protection
Explore our advanced security approaches to understand how businesses can create multi-layered defense mechanisms. Cyber security methods protect businesses by establishing comprehensive barriers across multiple technological domains.
These protective strategies encompass technological tools, human awareness training, and strategic protocols designed to create adaptive security ecosystems. By integrating advanced encryption technologies, firewall systems, and intelligent monitoring tools, businesses can significantly reduce their exposure to potential digital risks.

For Brisbane businesses, implementing sophisticated cyber security methods means creating resilient digital environments that can withstand evolving technological threats, safeguard sensitive information, and maintain operational continuity in an increasingly complex digital landscape.
Real-World Applications of Cyber Security Methods
Cyber security methods translate theoretical protection strategies into practical, actionable implementations that businesses can deploy to safeguard their digital assets. These real-world applications provide tangible solutions for addressing complex technological vulnerabilities across various organisational contexts.
Industry-Specific Security Implementations
Research from the Australian Signals Directorate demonstrates that cyber security methods must be tailored to specific industry requirements. Different sectors experience unique digital threat landscapes that demand customised protective approaches.
Industries requiring specialised cyber security applications include:
- Financial services with sensitive transaction data
- Healthcare organisations managing confidential patient information
- Legal firms protecting privileged communication records
- Professional services managing client intellectual property
Practical Technological Defence Strategies
Learn more about developing robust cyber security frameworks to understand how businesses can translate theoretical concepts into operational protection mechanisms. Practical applications involve implementing comprehensive technological solutions that address specific organisational vulnerabilities.
These strategies encompass advanced technological tools such as multi-factor authentication, encrypted communication channels, intrusion detection systems, and sophisticated access management protocols. By integrating these technologies, businesses create adaptive security infrastructures capable of responding dynamically to emerging digital threats.
For Brisbane businesses, understanding and implementing real-world cyber security methods means developing proactive, intelligent defense mechanisms that protect critical digital assets while maintaining operational efficiency and technological resilience.
This table summarises how cyber security methods are applied across different industries, highlighting the unique focus and specialised needs present in each sector.
| Industry | Unique Security Requirements | Example Focus |
|---|---|---|
| Financial Services | Protection of sensitive transaction data | Fraud detection, data encryption |
| Healthcare | Managing confidential patient information | Privacy controls, access management |
| Legal Firms | Safeguarding privileged communications | Secure client correspondence |
| Professional Services | Managing client intellectual property | Document protection, secure sharing |
Emerging Trends in Cyber Security Methods
The landscape of cyber security methods continues to evolve rapidly, driven by sophisticated technological advancements and increasingly complex digital threat environments. Businesses must remain agile and informed about emerging trends that reshape digital protection strategies and respond to innovative cybercrime techniques.
Artificial Intelligence and Machine Learning Integration
Research from the Australian Cyber Security Centre highlights the transformative potential of artificial intelligence in cybersecurity methodologies. Modern cyber security methods are increasingly incorporating intelligent systems capable of predictive threat analysis and autonomous response mechanisms.
Key emerging technological trends include:
- Advanced machine learning threat detection algorithms
- Self-adapting security protocols
- Real-time anomaly identification systems
- Predictive risk assessment technologies
Next Generation Security Frameworks
Discover our comprehensive approach to emerging cyber technologies to understand how businesses can stay ahead of evolving digital threats. Modern cyber security methods are transitioning from reactive to proactive and predictive security models that anticipate and neutralise potential vulnerabilities before they can be exploited.
These advanced frameworks leverage quantum computing principles, blockchain technologies, and zero-trust security architectures to create more resilient and intelligent digital defense mechanisms. By integrating sophisticated technological tools with human expertise, businesses can develop comprehensive security strategies that adapt dynamically to emerging digital risks.
For Brisbane businesses, understanding and adopting these emerging cyber security methods represents a critical strategy for maintaining technological resilience and protecting valuable digital assets in an increasingly complex digital ecosystem.
Secure Your Business Future with Cyber Security Tailored for You
You have learned how sophisticated digital threats, real-time monitoring, and multi-layered cyber security methods are now essential for every business in Brisbane. The article clearly highlights that data breaches, reputational harm, and operational risks threaten even the most careful organisations. With an increasing need for proactive strategies, simply knowing about these risks is not enough—building a defence you can rely on is crucial.
Do not leave your business exposed to evolving dangers. The team at IT Start is committed to translating the latest cyber security strategies from theory into robust protection for your company. Our local expertise and security-focused IT support are specifically tailored for small to medium-sized businesses in Queensland, ensuring industry compliance and peace of mind.
Act now to safeguard your information and reputation. Reach out today for a free assessment at IT Start and discover the difference a proactive, Brisbane-based partner can make for your business.
Frequently Asked Questions
What are cyber security methods?
Cyber security methods are strategic approaches used by businesses to protect digital assets, networks, and systems from malicious attacks and security breaches. They aim to safeguard sensitive information and maintain operational integrity.
Why are cyber security methods important for businesses?
Cyber security methods are crucial for businesses as they protect against data theft, financial fraud, reputation damage, and legal challenges that arise from security breaches, thus ensuring the stability and security of operational processes.
How do cyber security methods protect sensitive information?
Cyber security methods protect sensitive information by implementing multilayered security measures such as encryption, continuous monitoring, and proactive threat detection systems that work together to prevent unauthorized access and vulnerabilities.
What is a multilayered security architecture in cyber security?
A multilayered security architecture refers to the integration of multiple defensive barriers within an organisation’s digital infrastructure. It combines various protective measures across network security, application security, and operational security to create a comprehensive protection strategy.



